Method for enhancing system safety, checking device and safety system
A technology to enhance the system and verification device, which is applied in the direction of platform integrity maintenance, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
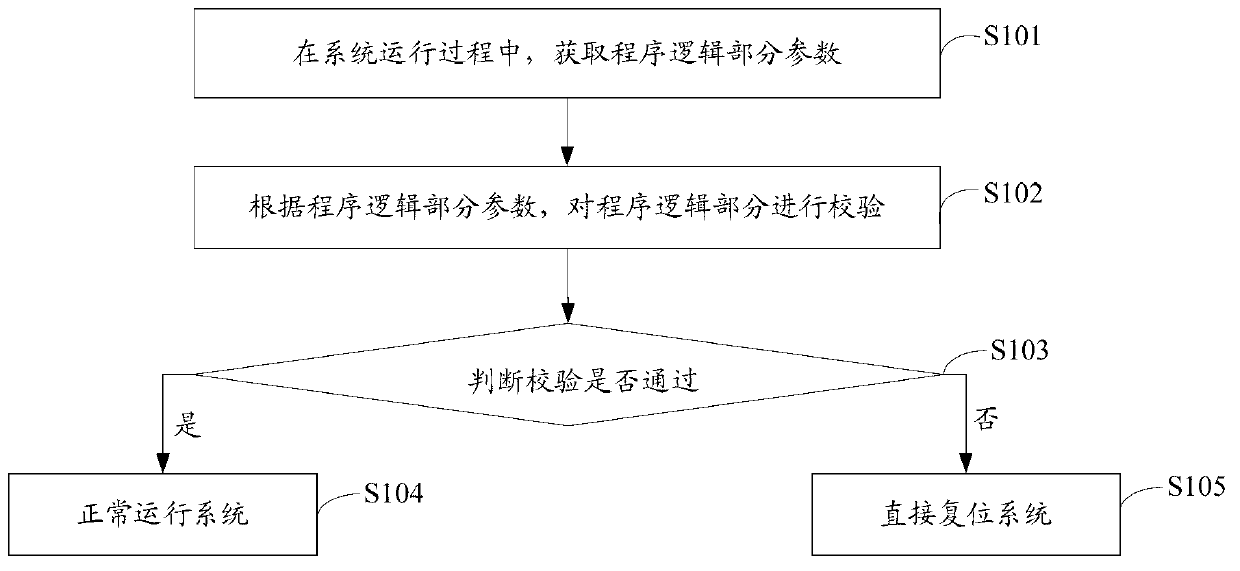
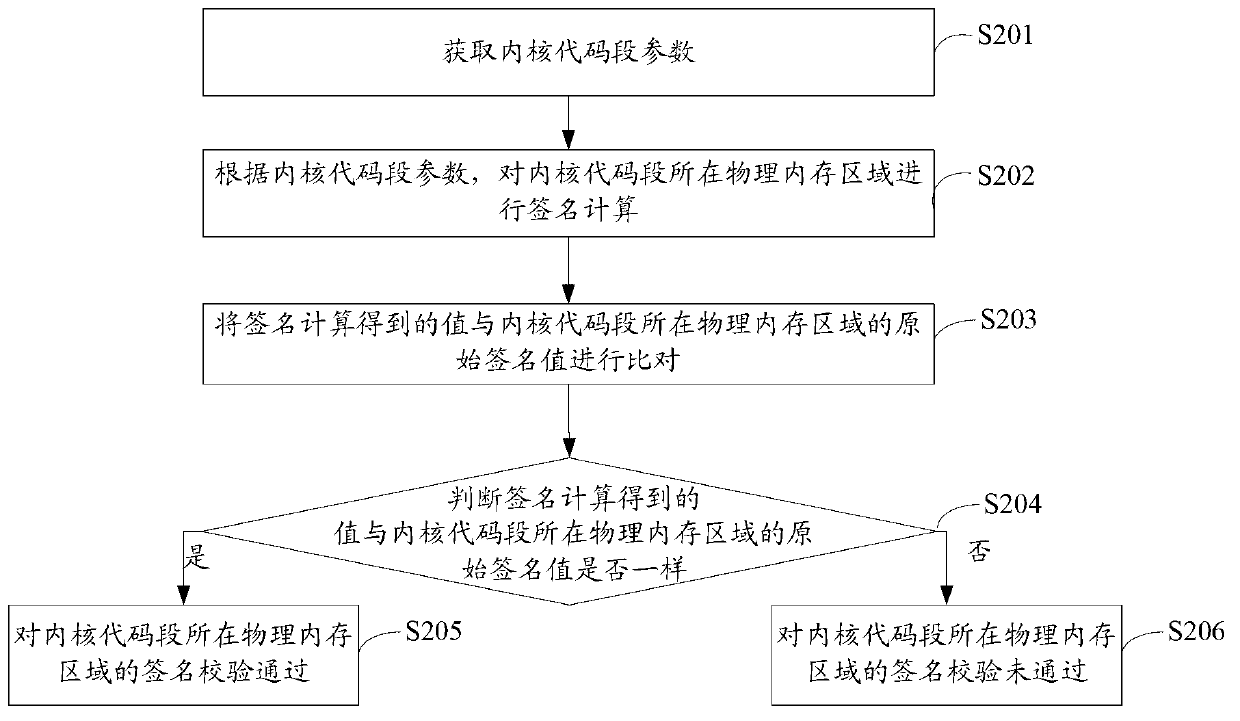
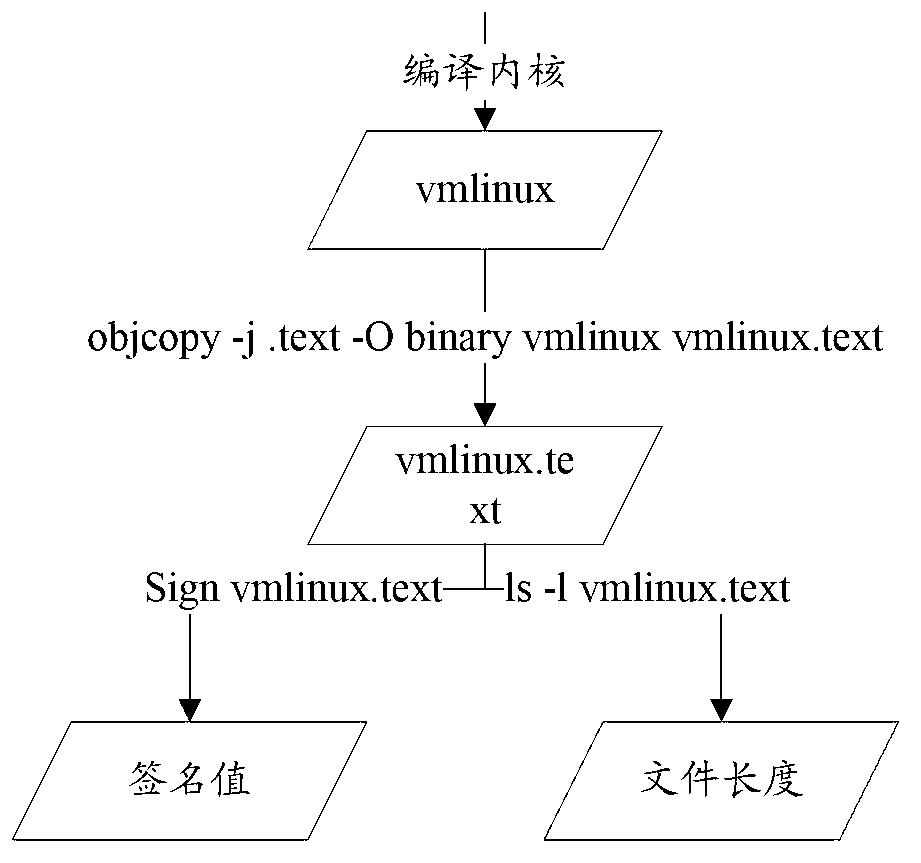
[0040] The core of a software system is composed of program logic with static attributes and data with dynamic attributes. The typical characteristic of static attributes is invariance, while the characteristic of dynamic attributes is variability. Theoretically speaking, it is impossible to predict the change law of the data inside a large-scale software system, that is to say, its value change is random and disordered; and the unchanging program logic (commonly known as code) is often changed once it changes. It means risks, such as being inserted into illegal codes or being tampered with, etc. Therefore, the invariance of active protection program logic parts can improve the security of system software.
[0041] The method for enhancing system security in the present application introduces an active protection strategy to protect the immutable program logic part of the software and prevent behaviors of tampering with system software by exploiting system loopholes. Wherein, ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com