Confidential product-sum computation method, confidential product-sum computation system, computation apparatus, and program for same
Technology of a computing device and computing method, applied in the fields of hidden product sum computing systems, computing devices and their programs
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
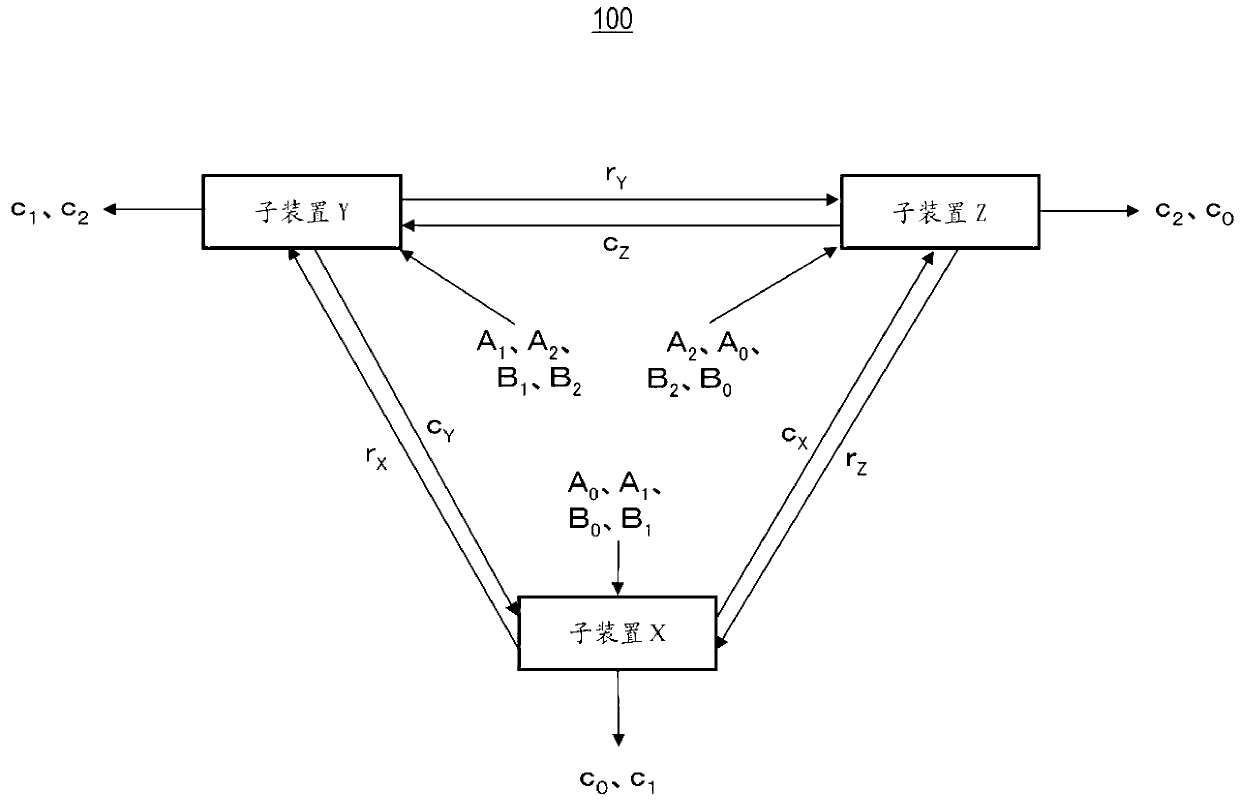
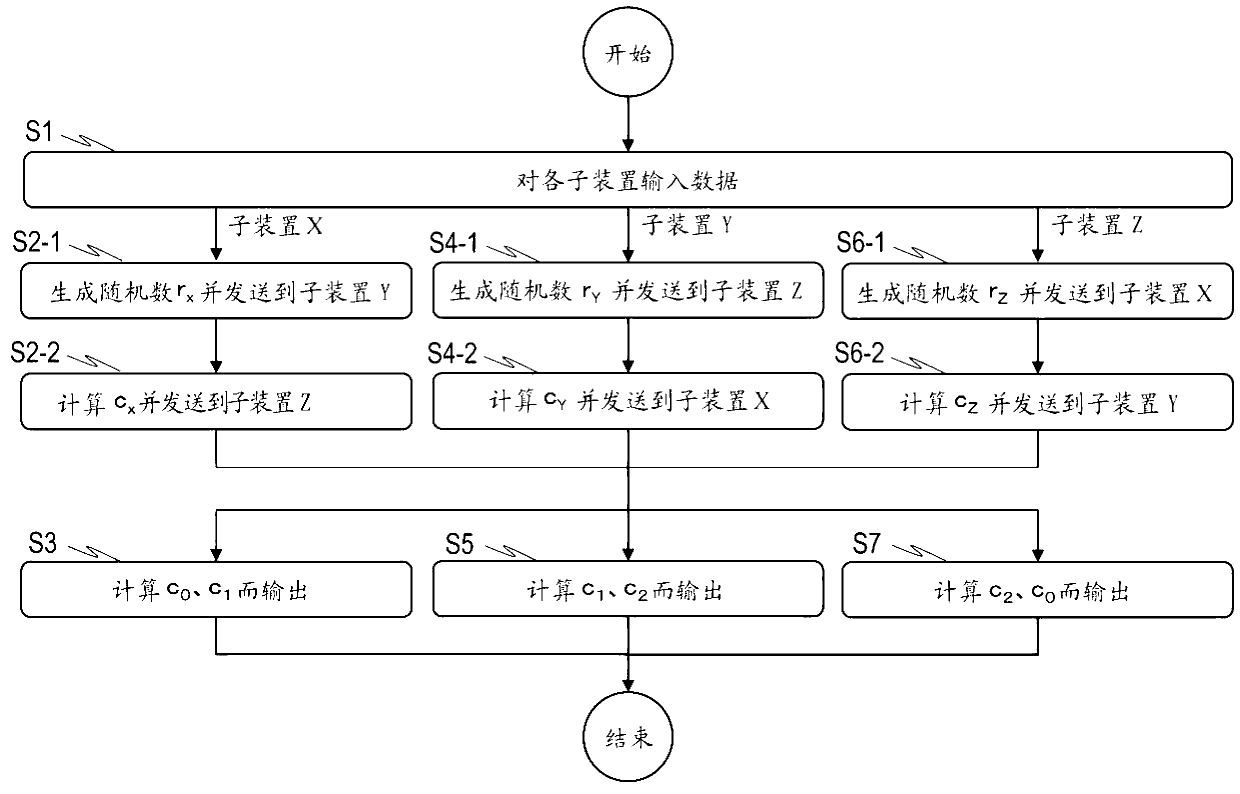
[0073] figure 1 shows a configuration example of the hidden product sum computing system 100, figure 2 Indicates an example of its processing flow. The hidden product sum computing system 100 includes a sub-device (party) X, a sub-device (party) Y, and a sub-device (party) Z as computing devices that respectively perform symmetrical calculation processing.
[0074] The hidden product sum calculation of the present invention is carried out through the coordinated calculation of the three calculation devices of sub-device X, sub-device Y, and sub-device Z to perform data sequence A 0 =(a0 0 ,...,a0 na0-1 ), A 1 =(a1 0 ,...,a1 na1 -1 ) and A 2 =(a2 0 ,...,a2 na2-1 ) with data column B 0 =(b0 0 ,...,b0 nb0-1 ), B 1 =(b1 0 ,...,b1 nb1-1 ) and B 2 =(b2 0 ,...,b2 nb2-1 ) product and calculation. na0, na1, na2, nb0, nb1, and nb2 are natural numbers respectively.
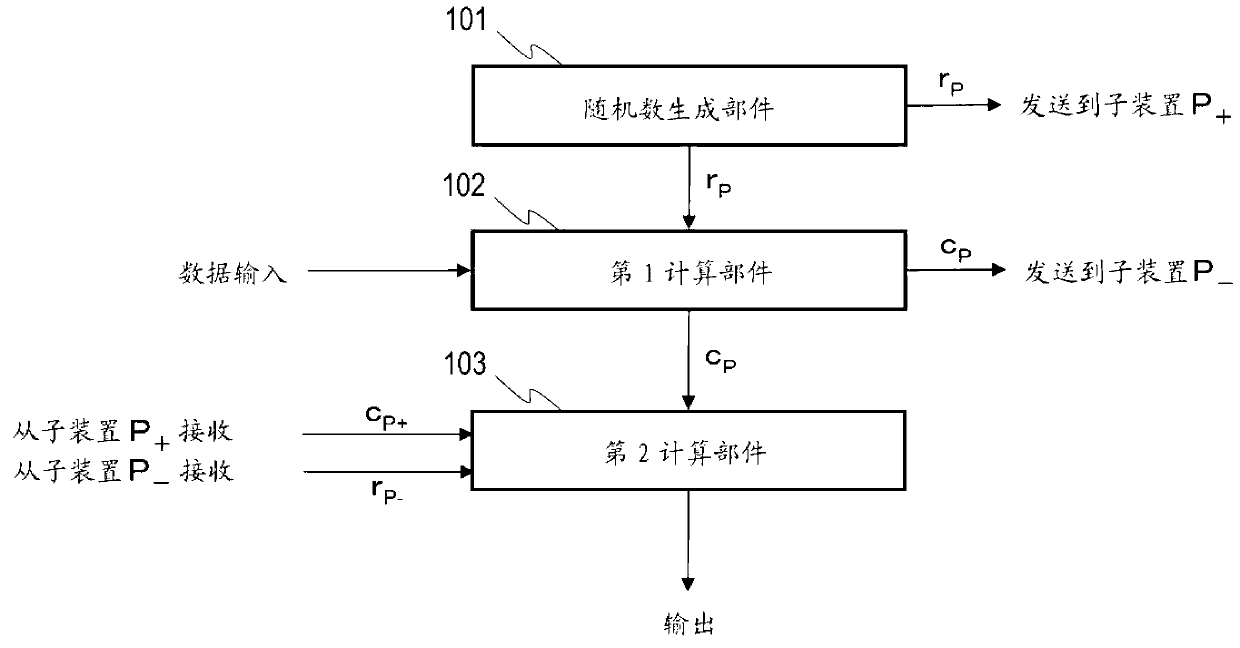
[0075] Such as image 3 As shown, each sub-device includes a random number generation unit 101 , a ...
Embodiment 2
[0112] Embodiment 2 is a specific example of Embodiment 1, and is na0=na1=na2=nb0=nb1=nb2=n (n is an integer greater than 1), e00=e01=e10=e11=e12=e21=e22=e20= The case of e02=1. Figure 4 A configuration example of the hidden product sum computing system 200 of this embodiment is shown, Figure 5 Indicates an example of its processing flow. The hidden product sum calculation system 200 includes a sub-device X, a sub-device Y, a sub-device Z, a data sequence decomposition supply unit 210 , and an output unit 220 . Same as Example 1, such as image 3 As shown, each sub-device includes a random number generation unit 101 , a first calculation unit 102 , and a second calculation unit 103 .
[0113] The hidden product sum calculation system 200, through the coordinated calculation of the three calculation devices of sub-device X, sub-device Y, and sub-device Z, calculates the element a of a natural number smaller than the prime number p i , b i (i=0,...,n-1) two data columns A...
Embodiment 3
[0154] Embodiment 3 is a structure in which a fraud detection function is added to Embodiments 1 and 2 which perform product sum calculation. Figure 6 shows a configuration example of the hidden product sum computing system 300, Figure 7 Indicates an example of its processing flow. The hidden product sum calculation system 300 includes a sub-device X, a sub-device Y, and a sub-device Z as computing devices that perform respective symmetrical calculation processing.
[0155] The hidden product sum calculation of the present invention is performed for a total of m groups of q=0,...,m-1 (m is an integer greater than 1) through the coordinated calculation of the three computing devices of sub-device X, sub-device Y, and sub-device Z (Parallel when m is 2 or more) Perform data column A q_0 =(a0 q_0 ,...,a0 q_na0-1 ), A q_1 =(a1 q_0 ,...,a1 q_na1-1 ) and A q_2 =(a2 q_0 ,...,a2 q_na2-1 ) with data column B q_0 =(b0 q_0 ,...,b0 q_nb0 -1 ), B q_1 =(b1 q_0 ,...,b1 q_nb1...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com