High-safety JPEG image steganography method
A high-security, image technology, applied in the field of high-security JPEG image steganography, can solve the problems of no model or solution, different degrees of importance, unreasonable distortion functions, etc., to achieve good image quality and ensure security , to ensure the effect of image quality
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
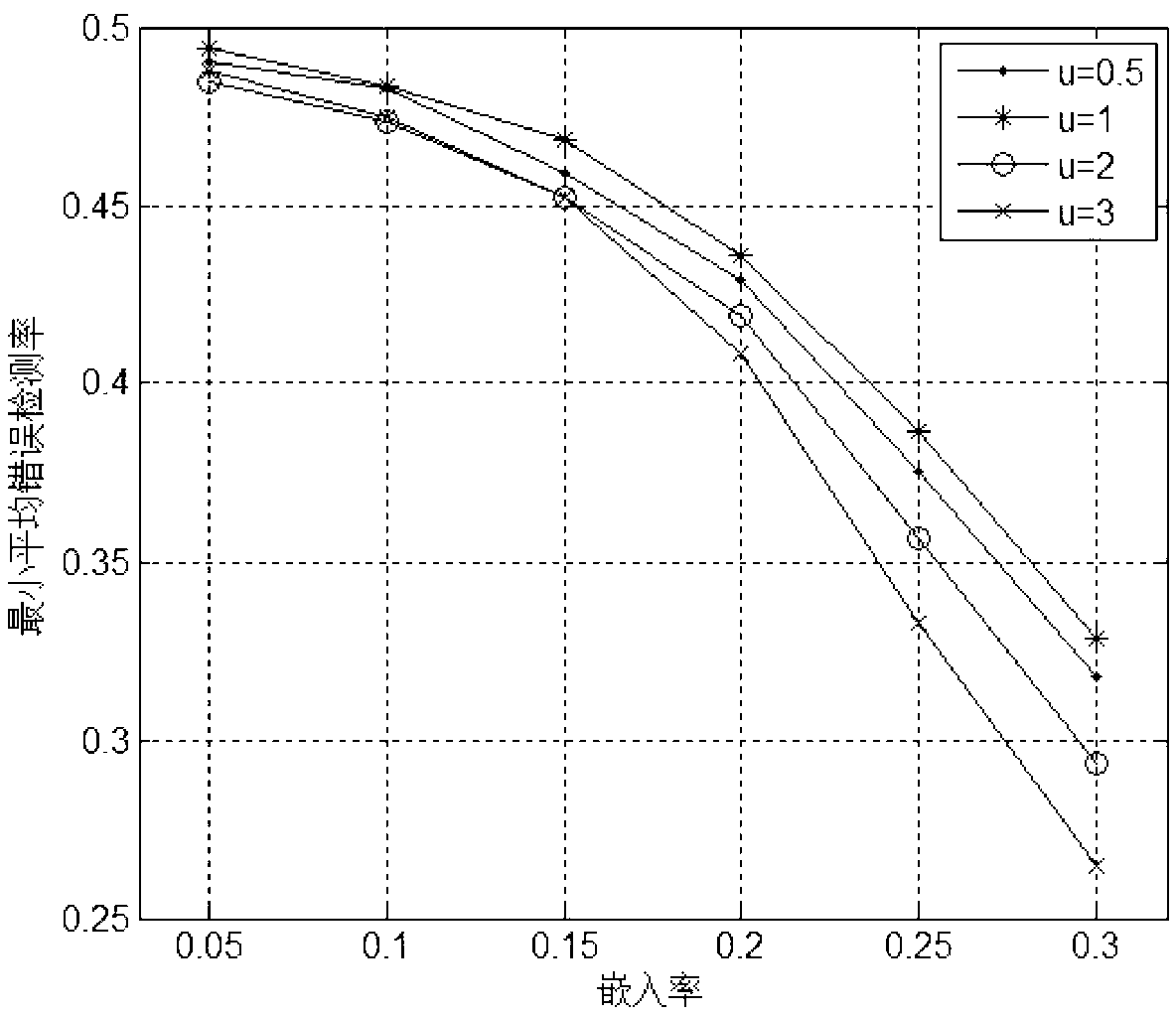
Image
Examples
Embodiment 1
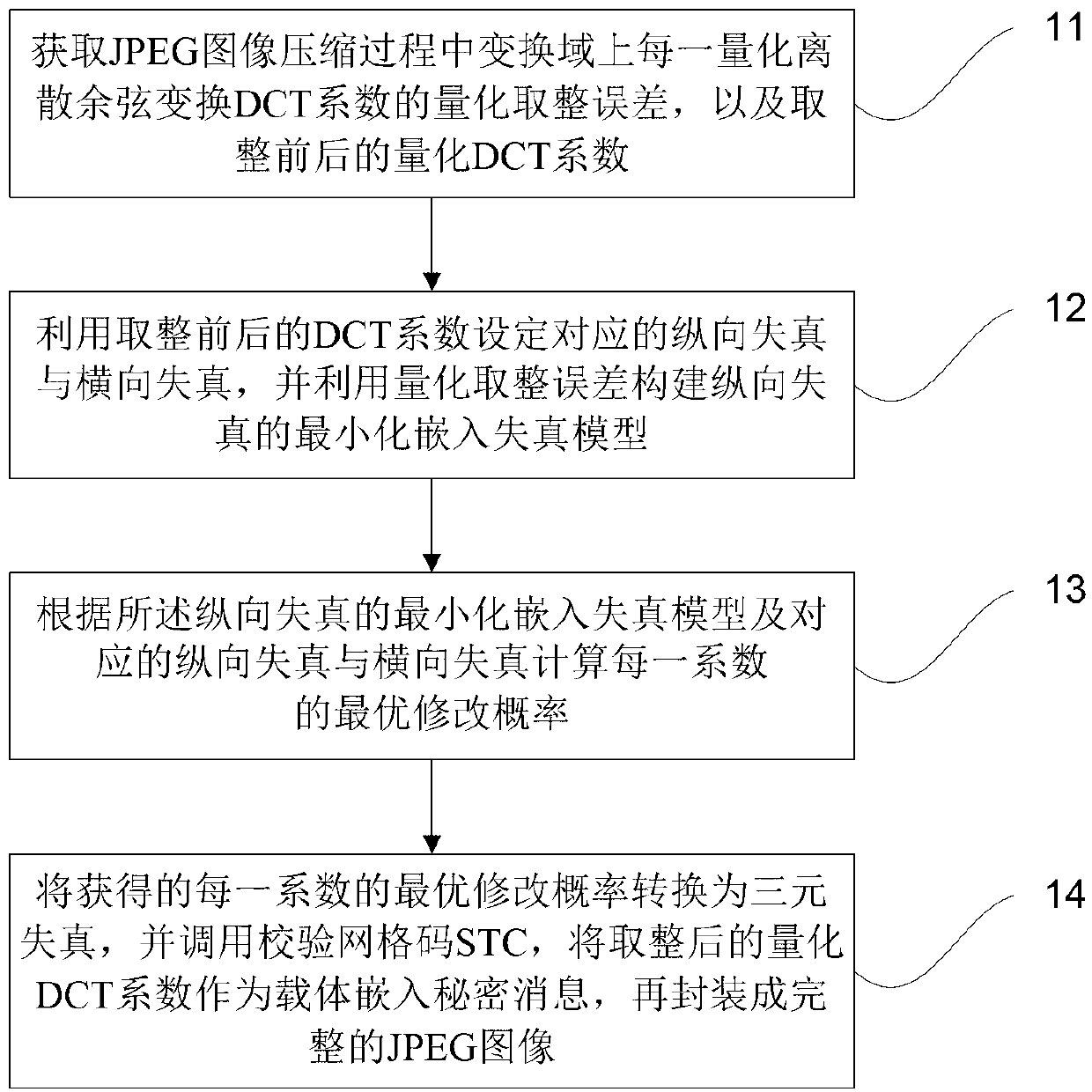
[0021] figure 1 It is a flow chart of a high-security JPEG image steganography method provided by Embodiment 1 of the present invention. Such as figure 1 As shown, the method mainly includes the following steps:
[0022] Step 11, obtain the quantized rounding error of each quantized discrete cosine transform DCT coefficient in the transform domain during the JPEG image compression process, and the quantized DCT coefficient x before and after rounding i with X i ;.
[0023] The DCT coefficients include DC coefficients and AC coefficients. After the DCT transformation is performed according to the 8×8 blocks, the coefficient in the upper left corner of the 8×8 block is the DCT DC coefficient, and the remaining 63 coefficients are all the DCT AC coefficients.
[0024] In addition, the quantized DCT coefficient x before and after rounding i with X i The relationship between can be expressed as: X i =round(x i ), that is, X i to take the closest to x i an integer of .
...
Embodiment 2
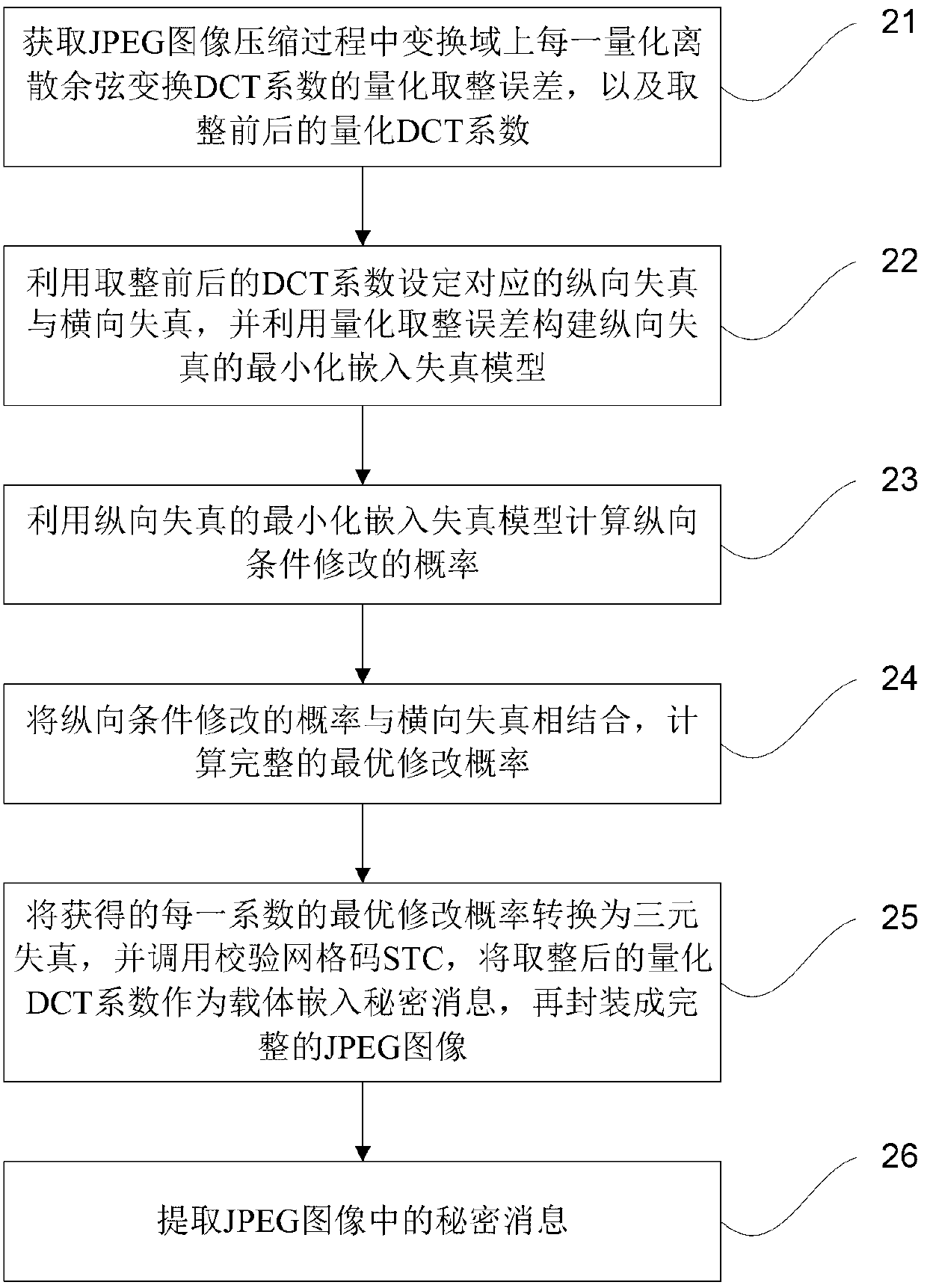
[0039] In order to facilitate understanding of the present invention, below in conjunction with figure 2 The present invention is further introduced. Such as figure 2 As shown, the method mainly includes the following steps:
[0040] Step 21, obtain the quantized rounding error of each quantized discrete cosine transform DCT coefficient in the transform domain during the JPEG image compression process, and the quantized DCT coefficient x before and after rounding i with X i ;.
[0041] The DCT coefficients include DC coefficients and AC coefficients. After DCT transformation is performed according to 8×8 blocks, the coefficient in the upper left corner of the 8×8 block is DCT DC coefficients, and the remaining 63 coefficients are all DCT AC coefficients.
[0042] In addition, the quantized DCT coefficient x before and after rounding i with X i The relationship between can be expressed as: X i =round(x i ), that is, X i to take the closest to x i an integer of .
...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com