Method and device for initializing electronic signature tool
An electronic signature tool and initialization technology, applied in the electronic field
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
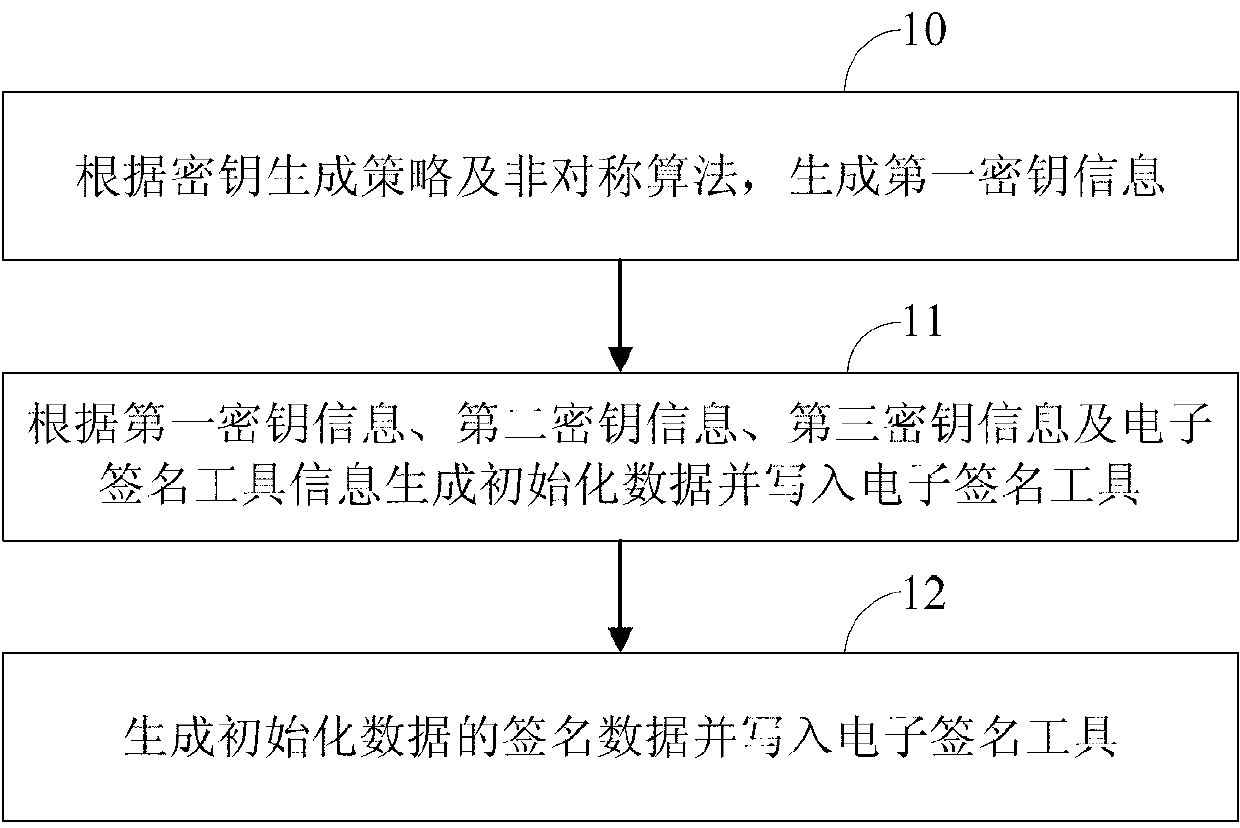
[0112] figure 1 This is a flowchart of Embodiment 1 of the method for initializing an electronic signature tool of the present invention. Combine now figure 1 , the first embodiment of the method for initializing an electronic signature tool of the present invention is described, and the details are as follows:
[0113]Step 10: generate the first key information according to the key generation strategy and the asymmetric algorithm;
[0114] The first key information includes at least a public key and a private key; the public key included in the first key information includes at least two public key parameters, and the number of the public key parameters can be determined by the algorithm used to generate the first key information , the public key parameters that make up the public key are used as a public key in the process of encryption and signature verification; the key generation strategy is the asymmetric algorithm required to generate the public key and private key co...
Embodiment 2
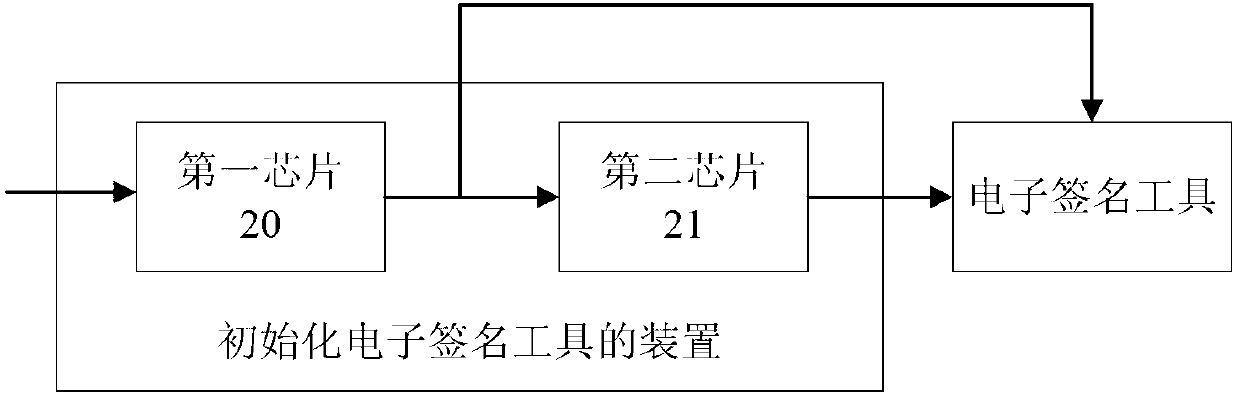
[0134] figure 2 This is a flow chart of Embodiment 2 of the apparatus for initializing an electronic signature tool according to the present invention. Combine now figure 2 , the second embodiment of the device for initializing the electronic signature tool of the present invention will be described, and the details are as follows:
[0135] The apparatus for initializing the electronic signature tool of the second embodiment includes: a first chip 20 and a second chip 21 .
[0136] The first chip 20 generates the first key information according to the key generation strategy and the asymmetric algorithm; the first chip 20 generates the first key information according to the public key contained in the first key information, the public key contained in the second key information and its version information , the public key and its version information contained in the third key information, and the electronic signature tool information, generate initialization data and write...
Embodiment 3
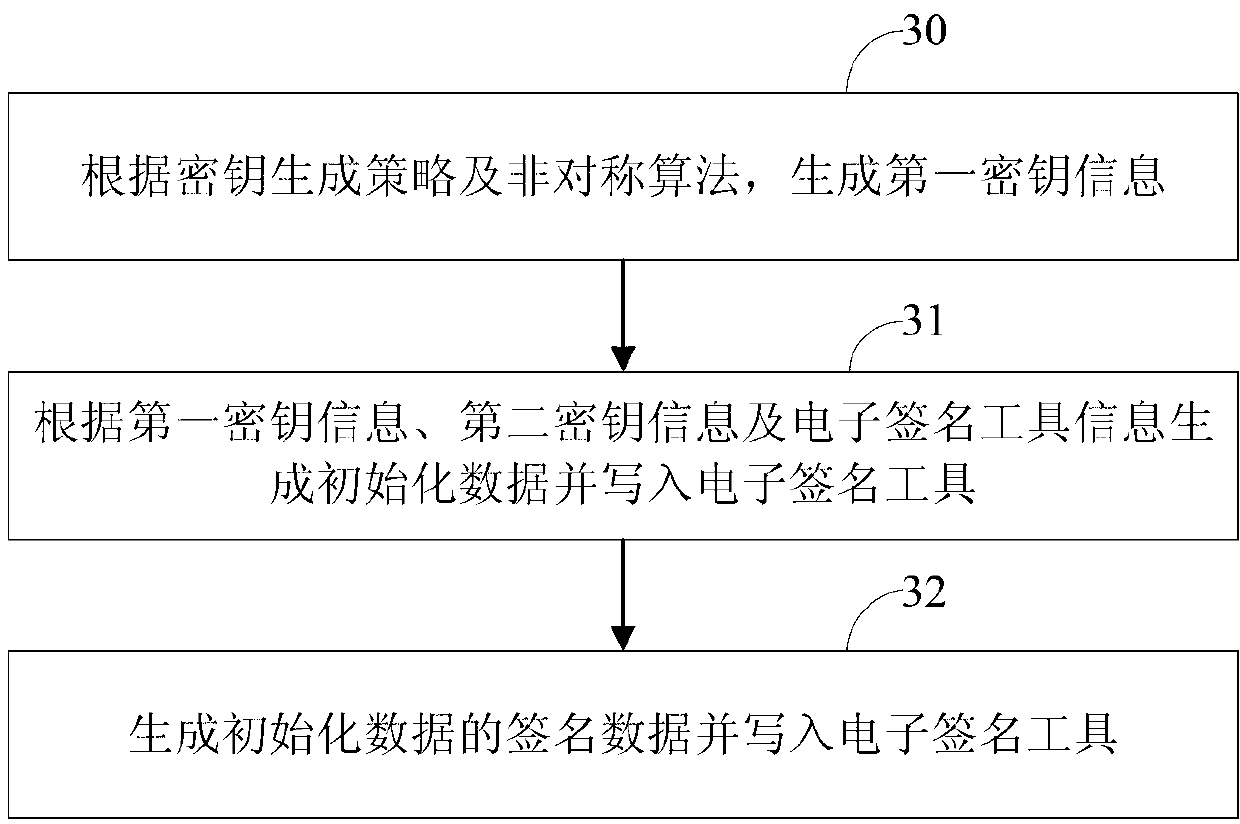
[0150] image 3 This is a flowchart of Embodiment 3 of the apparatus for initializing an electronic signature tool according to the present invention. Combine now image 3 , the third embodiment of the device for initializing the electronic signature tool of the present invention will be described, and the details are as follows:
[0151] Step 30: Generate first key information according to the key generation strategy and the asymmetric algorithm;
[0152] The first key information includes at least a public key and a private key; the public key included in the first key information includes at least two public key parameters, and the number of the public key parameters can be determined by the algorithm used to generate the first key information , the public key parameters that make up the public key are used as a public key in the process of encryption and signature verification; the key generation strategy is the asymmetric algorithm required to generate the public key an...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com