Terminal and display control method of user interface
A display control method and user interface technology, applied in the field of data security, can solve the problems of private data theft, user information insecurity, etc., and achieve the effect of improving security, avoiding damage or tampering, and ensuring security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment approach 1
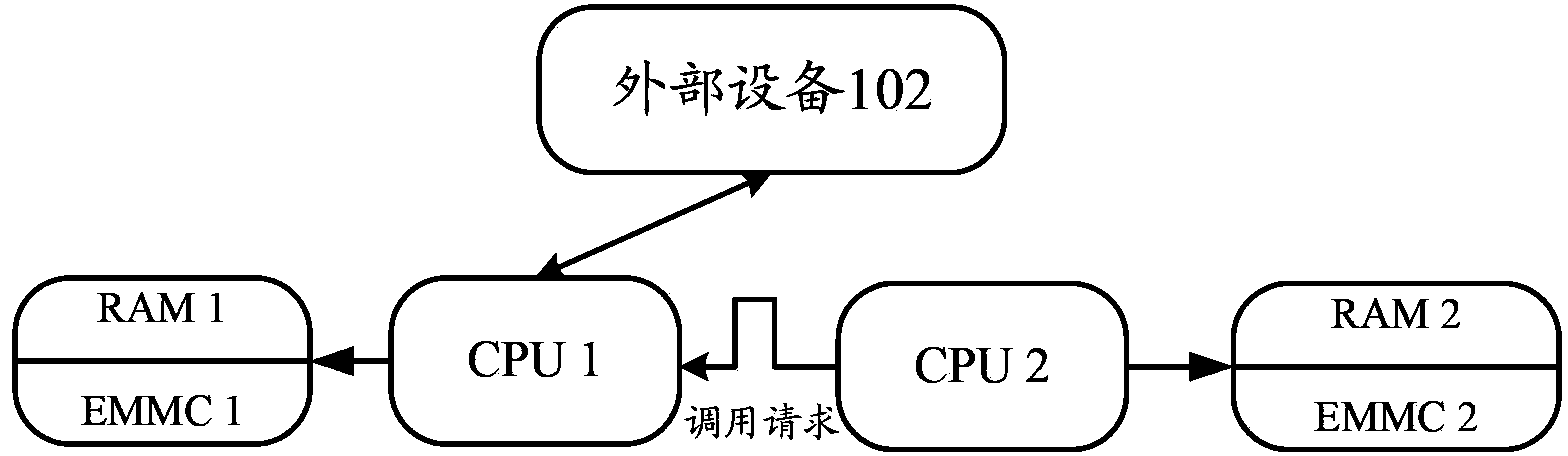
[0053] Such as figure 2 As shown, the interaction process between CPU2 and external device 102 is realized through data forwarding by CPU1.
[0054]Specifically, in the downlink process, the external device 102 transmits all the data to be sent to CPU1, and if CPU1 detects private data, it directly processes the private data, and transmits non-private data to CPU2; , CPU1 forwards the received data from CPU2 to external device 102 .
[0055] Since CPU1 is dedicated to processing private data, it is a more secure processor than CPU2, so all data is sent to CPU1, even if non-private data is sent by other applications (compared to what should have been sent to The acquisition and utilization of the application program) will not lead to the leakage of private information; as long as the private data can be guaranteed not to be processed by CPU2, the acquisition and utilization of private data by illegal applications based on CPU2 can be physically isolated, thereby The data sec...
Embodiment approach 2
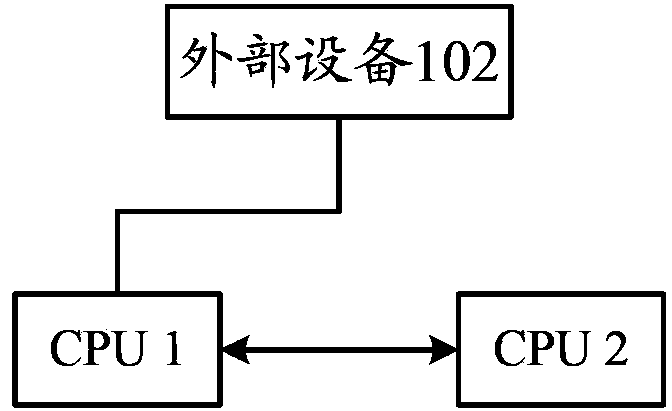
[0057] Such as image 3 As shown, CPU1 realizes the connection and interaction with the external device 102 through the peripheral interface, and realizes the connection with CPU2 through the forwarding interface, and realizes CPU2 and CPU2 by configuring and closing the connection between the forwarding interface and the described peripheral interface. The connection and interaction of the external device 102.
[0058] In the downlink process: the external device 102 transmits all the data to be sent to the CPU1, and if the CPU1 detects the private data, it directly processes the private data and transmits the non-private data to the CPU2.
[0059] In the uplink process: there is a one-to-one correspondence between the peripheral interface on the CPU1, the forwarding interface and the external device 102, and the CPU2 is provided with a transceiver interface that is connected to the forwarding interface on the CPU1 in one-to-one correspondence, then the When the CPU2 needs t...
Embodiment approach 3
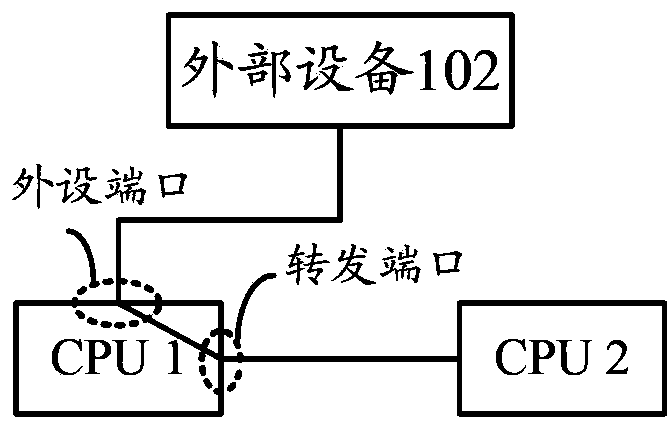
[0062] Such as Figure 4 As shown, CPU1 realizes the connection and interaction with the external device 102 through the peripheral interface, and realizes the connection with the CPU2 through the forwarding interface, and establishes a DMA transmission channel by configuring between the forwarding interface and the peripheral interface , realizing the connection and interaction between the CPU2 and the external device 102 .
[0063] Embodiment 3 is similar to Embodiment 2, except that after receiving the connection instruction from CPU2, CPU1 does not adopt "close the path between CPU2 and the specified external device 102", but determines the corresponding interface of the specified transceiver interface. Forwarding the interface and the peripheral interface, and configuring and establishing a DMA transmission channel between the forwarding interface and the peripheral interface.
[0064] The technical solution of the present application can be applied to various applicatio...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com