Side channel energy analysis method for SM3 cryptographic algorithm HMAC mode
A technology of energy analysis and cryptographic algorithm, applied in the field of side channel energy analysis
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
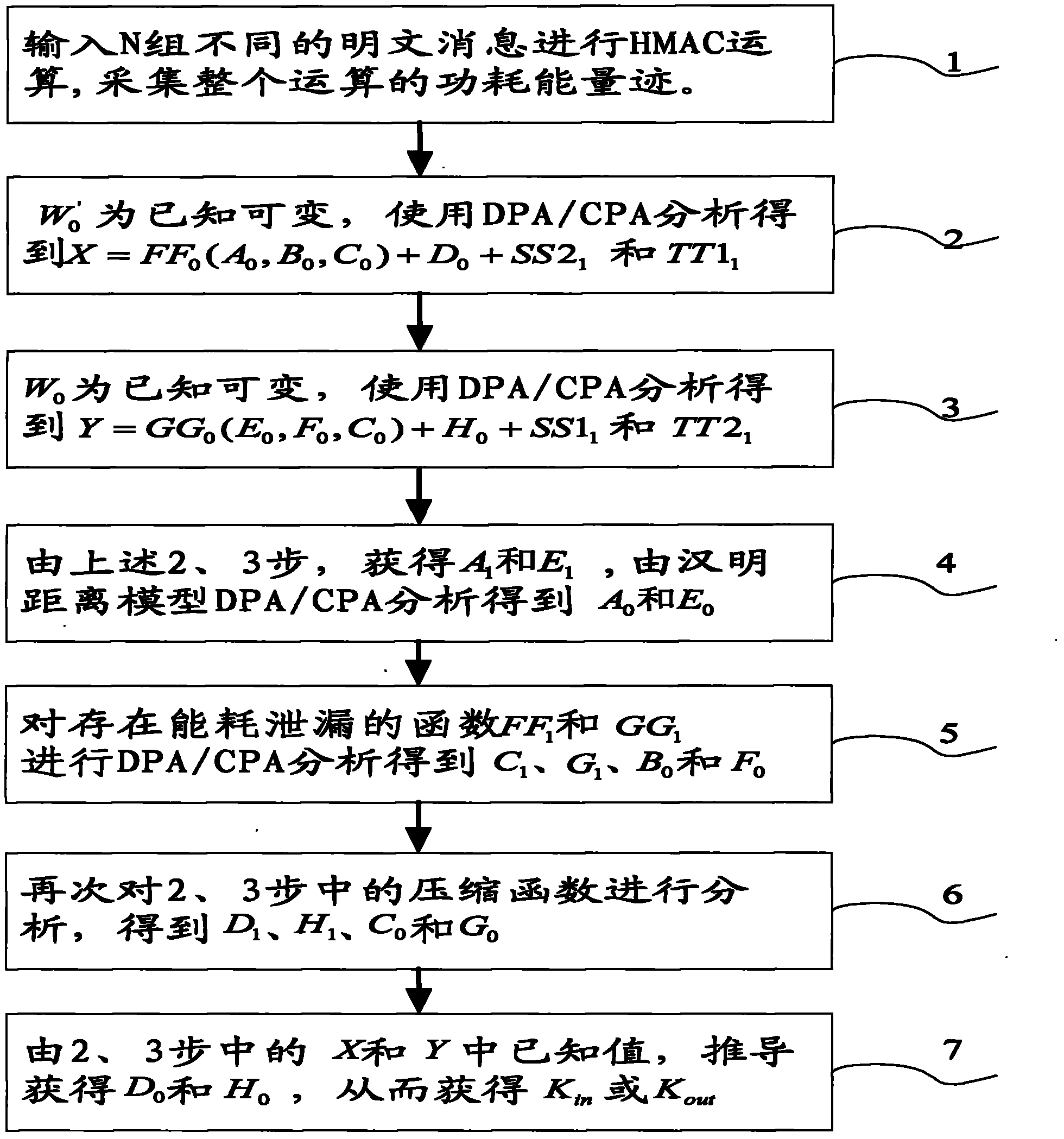
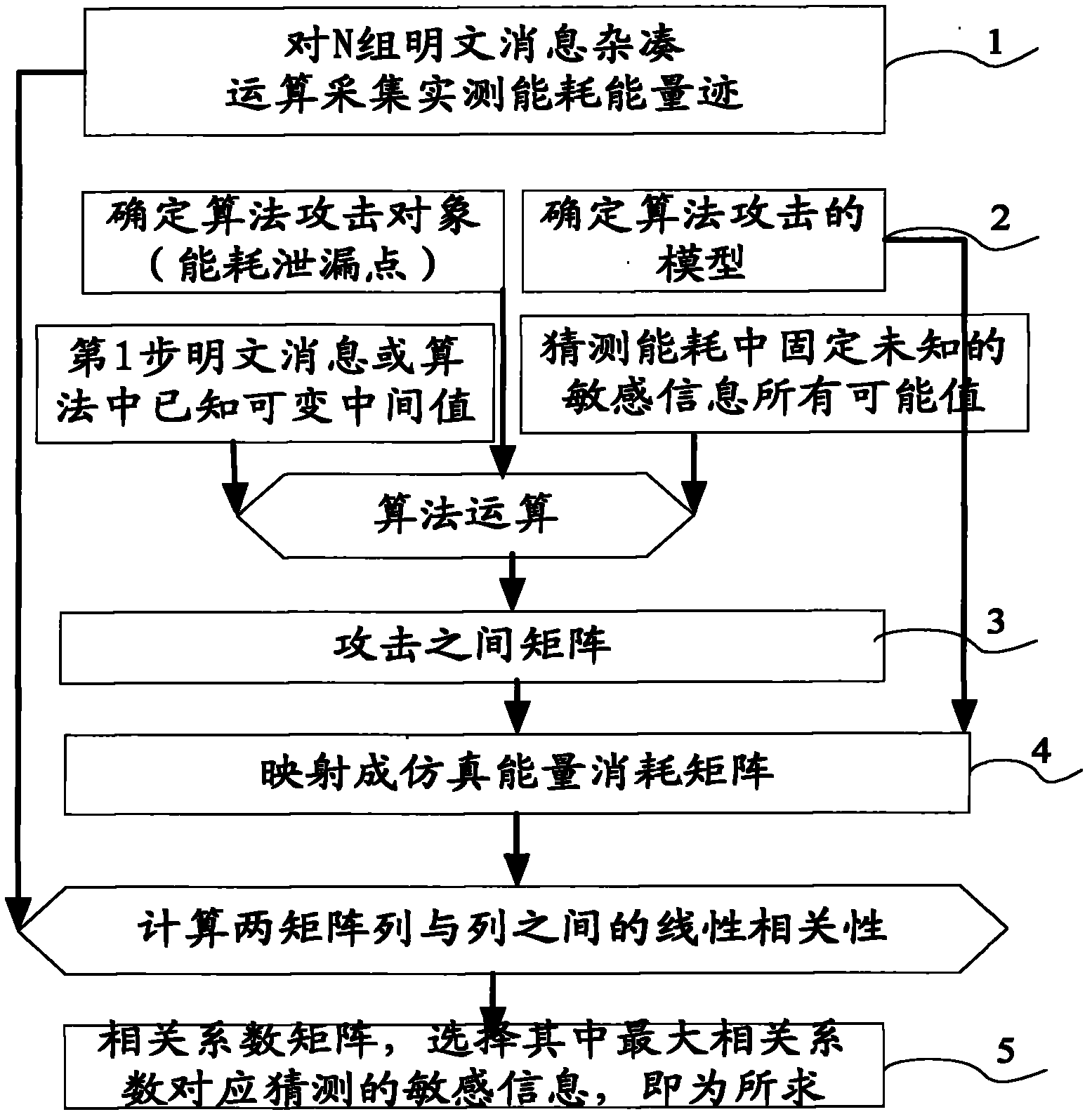
[0103] The present invention will be further described below in conjunction with embodiment:
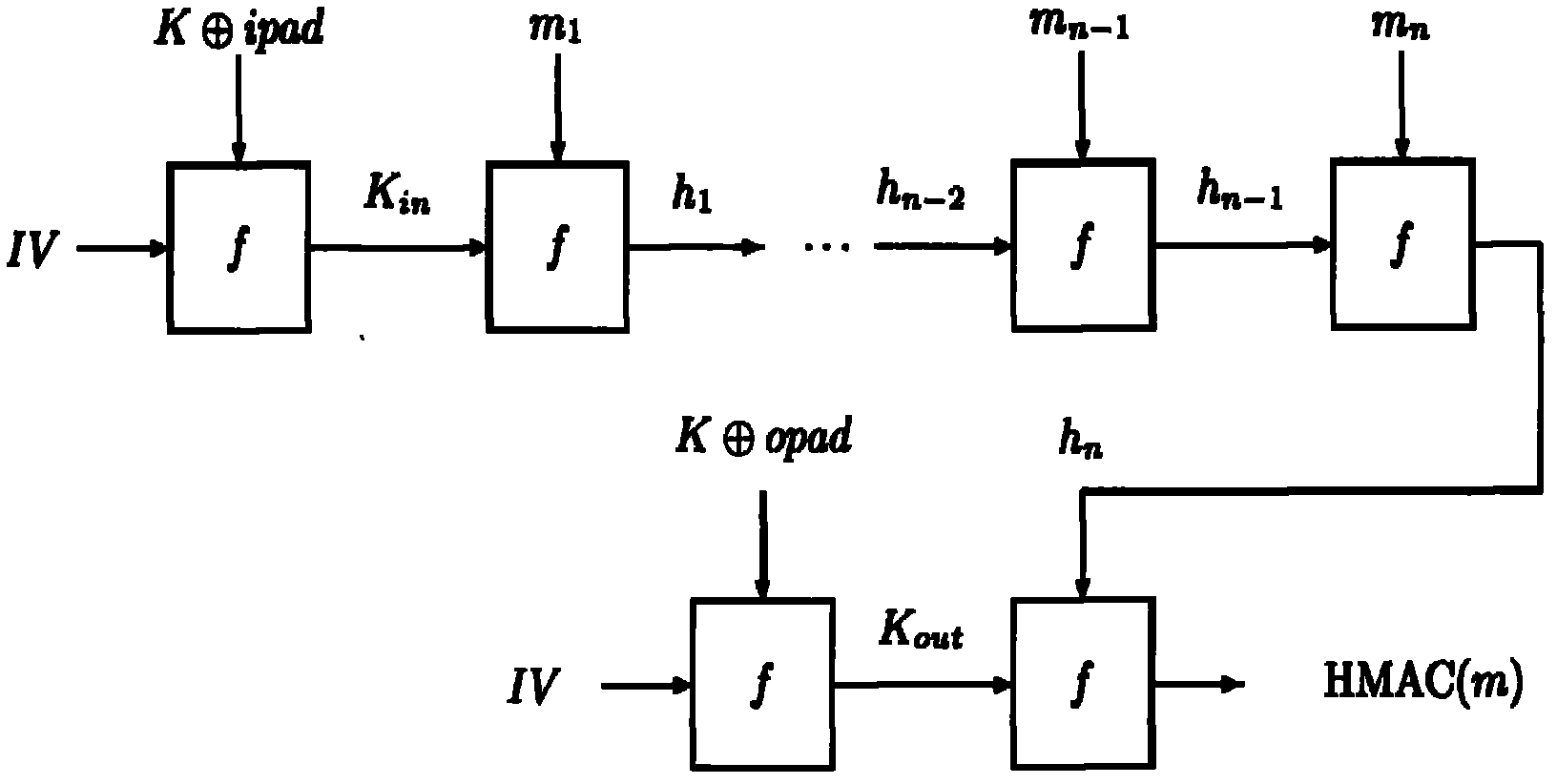
[0104] The present invention analyzes K with the CPA method in As an example, CPA analysis K out , DPA analysis K in / K out The implementation mode is consistent with this scheme.
[0105] 1. Collect energy traces
[0106] Input N different messages W=(m 1 ,...,m n ), let each input m 1 The values are different, and the energy traces during the HMAC operation are collected separately, and K is selected in =A 0 B 0 C 0 D. 0 E. 0 f 0 G 0 h 0 Participate in the energy consumption part of the operation to obtain the energy trace matrix E ( N × T ) = e 1 1 . . . ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com