Method and system for real-name authentication based on face recognition
A technology of real-name authentication and face recognition, which is applied in the transmission system, digital data authentication, user identity/authority verification, etc., can solve the problem that the security of off-site real-name authentication cannot be guaranteed, and achieve reliable sources, prevent fraudulent use, and reduce workload effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
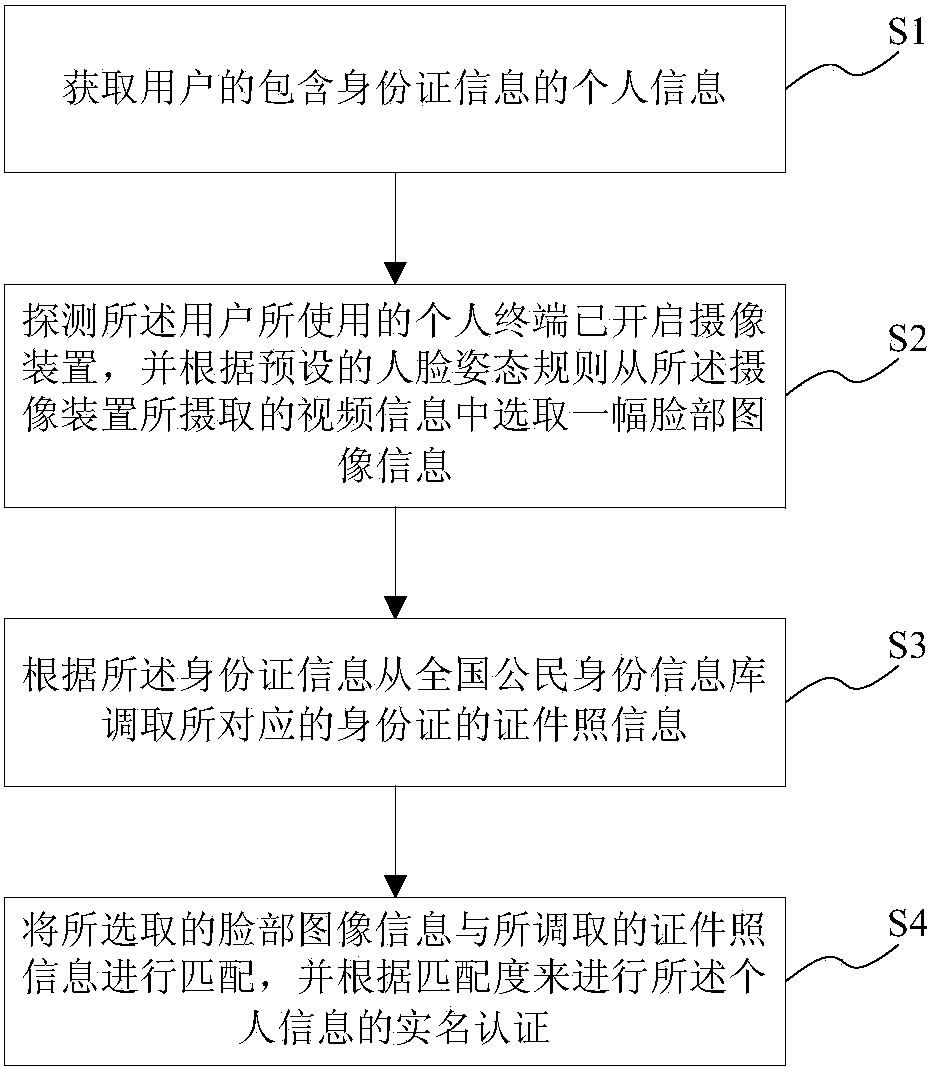
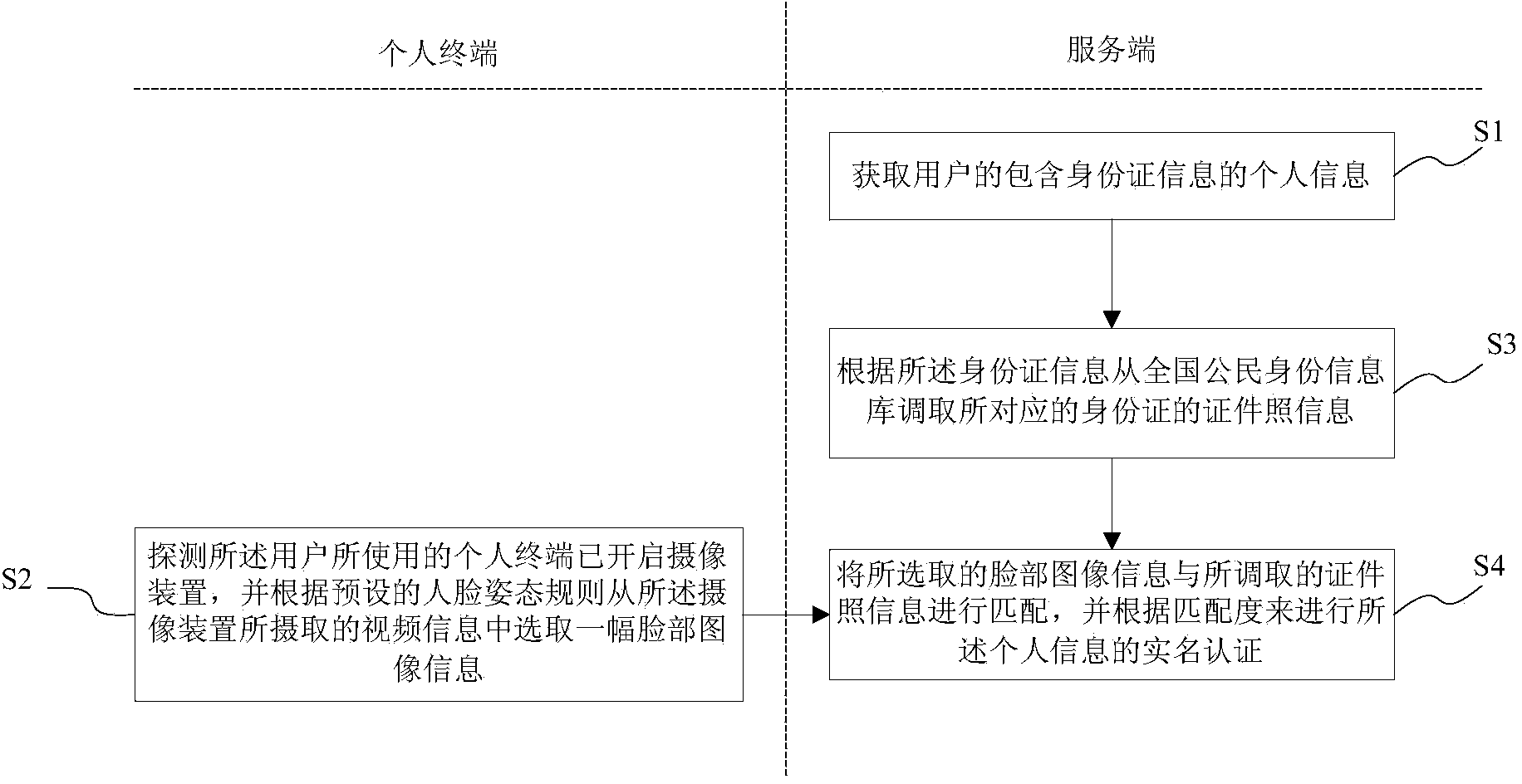
[0030] see figure 1 , 2 , the present invention provides a real-name authentication method based on face recognition. The authentication method performs real-name authentication by remotely acquiring face images, and effectively prevents the occurrence of impersonation. The authentication method is mainly performed by an authentication system, wherein the authentication system is software installed on a server, the server can communicate with the user's personal terminal through the network, and can push part of the calculation process to the personal terminal. The terminal is processed by the personal terminal, so as to reduce the system load of the server. The server includes, but is not limited to: servers, cloud-based server groups, clustered servers, and the like. The personal terminal has a built-in or external camera device. The personal terminals include but are not limited to: personal computers, mobile phones, tablet computers, and the like.
[0031] In step S1,...
Embodiment 2
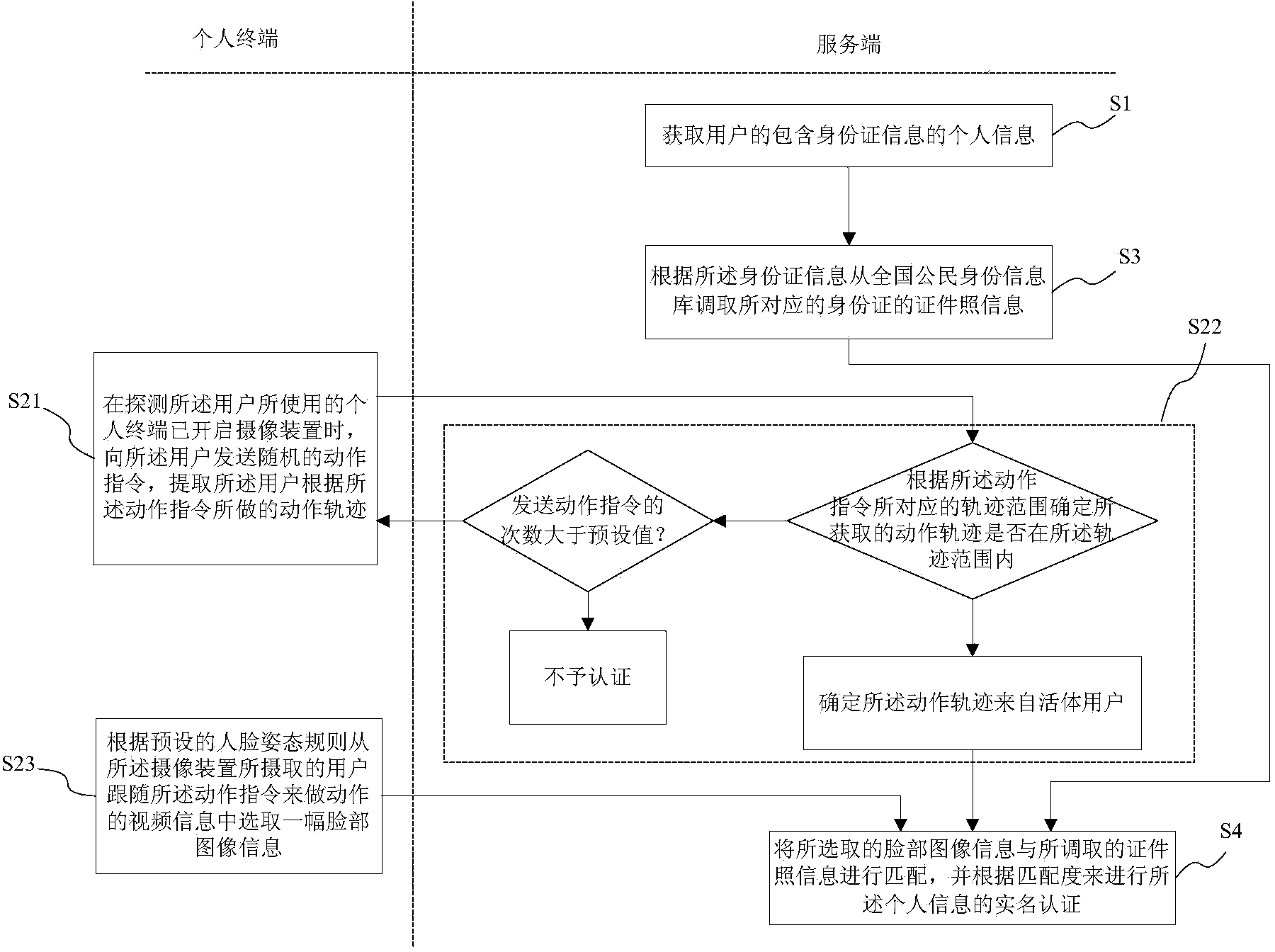
[0044] Such as image 3 As shown, the difference from the first embodiment is that, in order to prevent people with ulterior motives from using videos such as video recordings to impersonate, the step S2 further includes: steps S21, S22, and S23.
[0045] In step S21, when the authentication system detects that the personal terminal used by the user has turned on the camera device, it sends a random action instruction to the user, and extracts the action trajectory of the user according to the action instruction. Wherein, the action instructions include, but are not limited to: actions such as blinking eyes, opening mouth, turning head, etc., and combined action instructions.
[0046] Specifically, the authentication system randomly selects one or a group of action instructions from the pre-stored action instructions, and sends it to the personal terminal where the user is located through a web page, so as to prompt the user to follow the action instruction to perform an actio...
Embodiment 3
[0054] Such as Figure 4 As shown, the present invention also provides a real-name authentication system based on face recognition. The authentication system is software installed on the server. The server can communicate with the user's personal terminal through the network, and can push part of the calculation process to the personal terminal for processing by the personal terminal, so as to reduce service costs. End system burden. The server includes, but is not limited to: servers, cloud-based server groups, clustered servers, and the like. The personal terminal has a built-in or external camera device. The personal terminal includes, but is not limited to: personal computer, mobile phone, tablet computer, etc.
[0055] The authentication system 1 includes: a personal information acquisition module 11 , an image behavior extraction module 12 , a remote call module 13 , and an authentication module 14 . Wherein, the personal information obtaining module 11, the remote c...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com