A method for authentication and key agreement between devices
A technology of key agreement and equipment, applied in the field of digital communication, can solve the problem of low security, achieve the effect of improving security, ensuring security and reliability, and protecting security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0040] Before the two devices in the digital communication system need to exchange data, in order to ensure the security of the exchanged data, the two devices need to recognize each other’s identity. Encrypt transmission with session key.
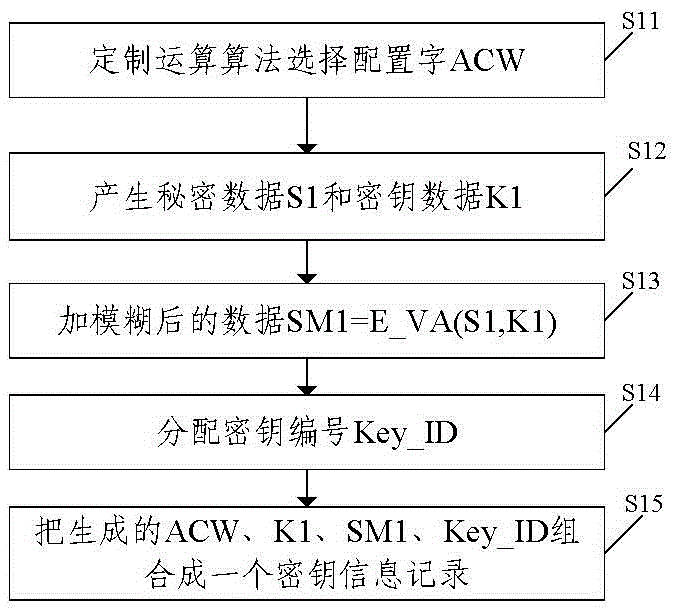
[0041] Before performing authentication and negotiation between two devices, the present invention assumes that the two devices already have the same key information record, that is, the key number Key_ID of the record of key-related data owned by the two devices is the same. A key information record is composed of key number Key_ID, plus fuzzy data SM1, key data K1, and configuration word ACW selected by an algorithm. One or more key information records can exist in a device, and a security area with access restrictions is opened up in the memory of the device, and one or more key information records are stored in the security area to form a "key store".
[0042] Such as figure 1 As shown, the generation of a key information record in t...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com