Asymmetric encryption authentication method and embedded device based on asymmetric encryption authentication
An asymmetric encryption and embedded device technology, applied in digital data protection, electrical digital data processing, instruments, etc., can solve problems such as inappropriate embedded devices, and achieve the effect of increasing security features and system security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
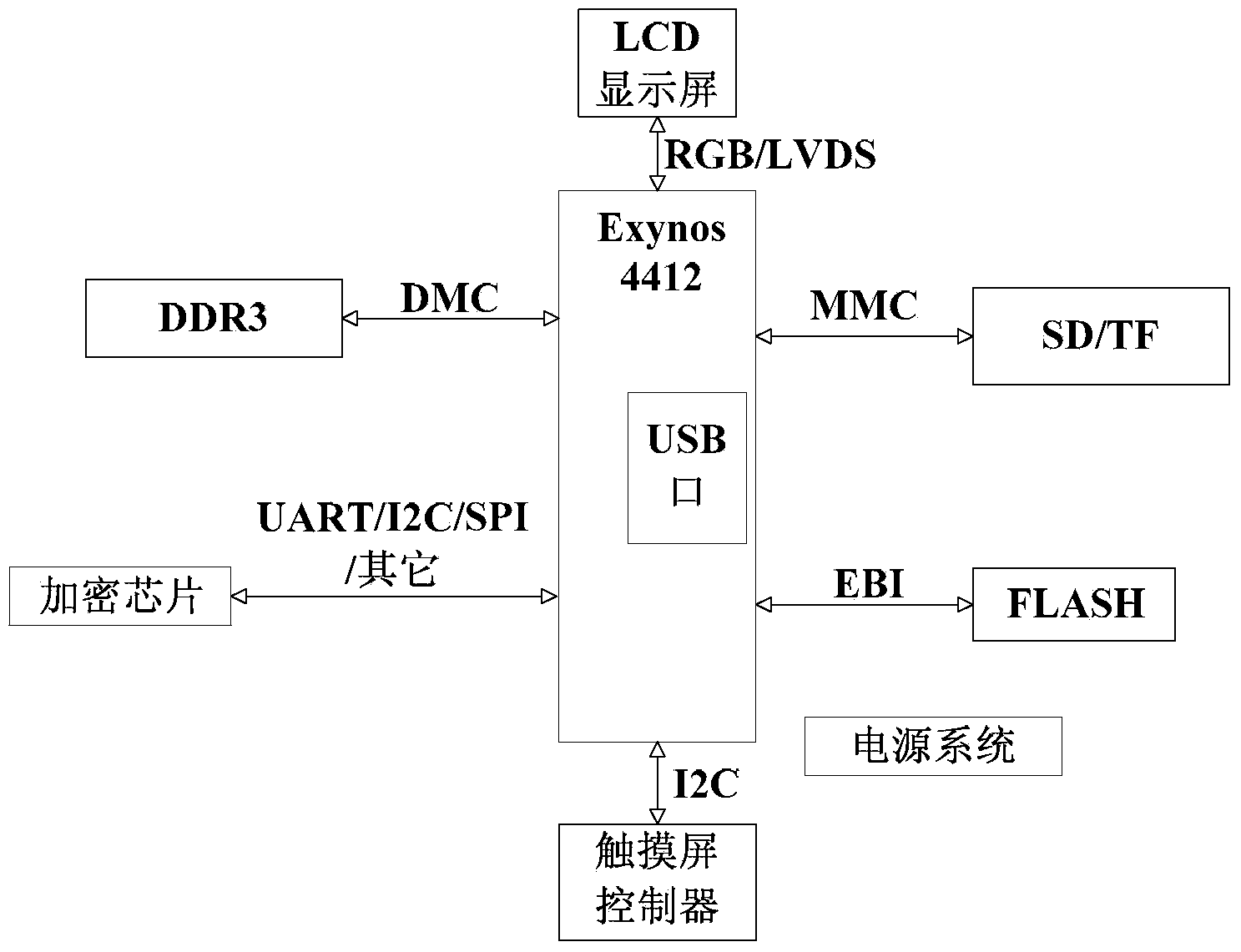
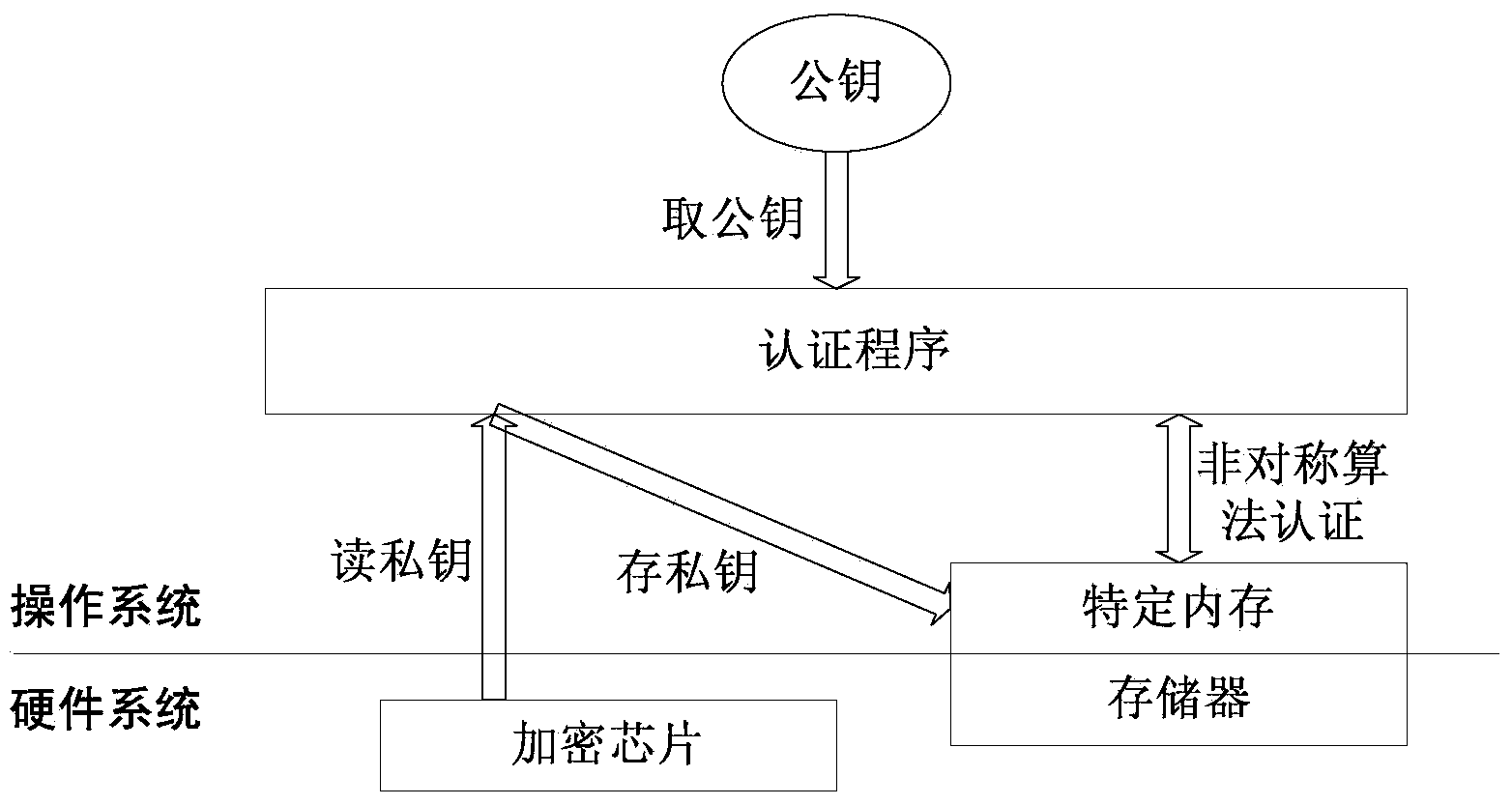
[0033] like Figure 1-2 , the hardware system consists of an encryption chip for generating private keys, Exynos4412 processor, touch screen, serial port, I2C port, SPI port, USB port, FLASH, SD / TF, DDR3, power supply, etc. The software system is based on the Linux operating system, adding an asymmetric encryption authentication program. The program needs to complete the following tasks: 1) Obtain the private key from the encryption chip, 2) Save the private key to a specific storage area, 3) Obtain the public key passed in by other drivers or upper-level applications in the kernel, 4) Store the private key in a specific storage area. The RSA asymmetric encryption algorithm is used for key authentication in the area (such as memory or FLASH). This authentication procedure is invisible to the application and is only scheduled by the operating system.
[0034] The present invention selects Exynos4412 as the processor, and the processor has a good application in the tablet fiel...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com