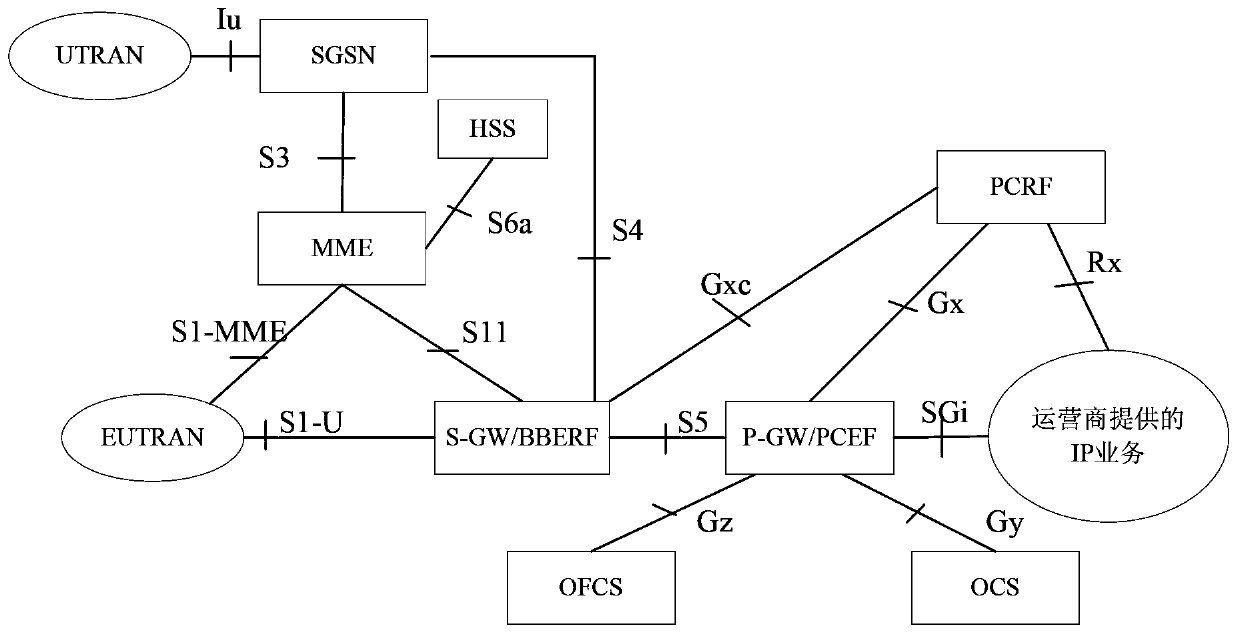
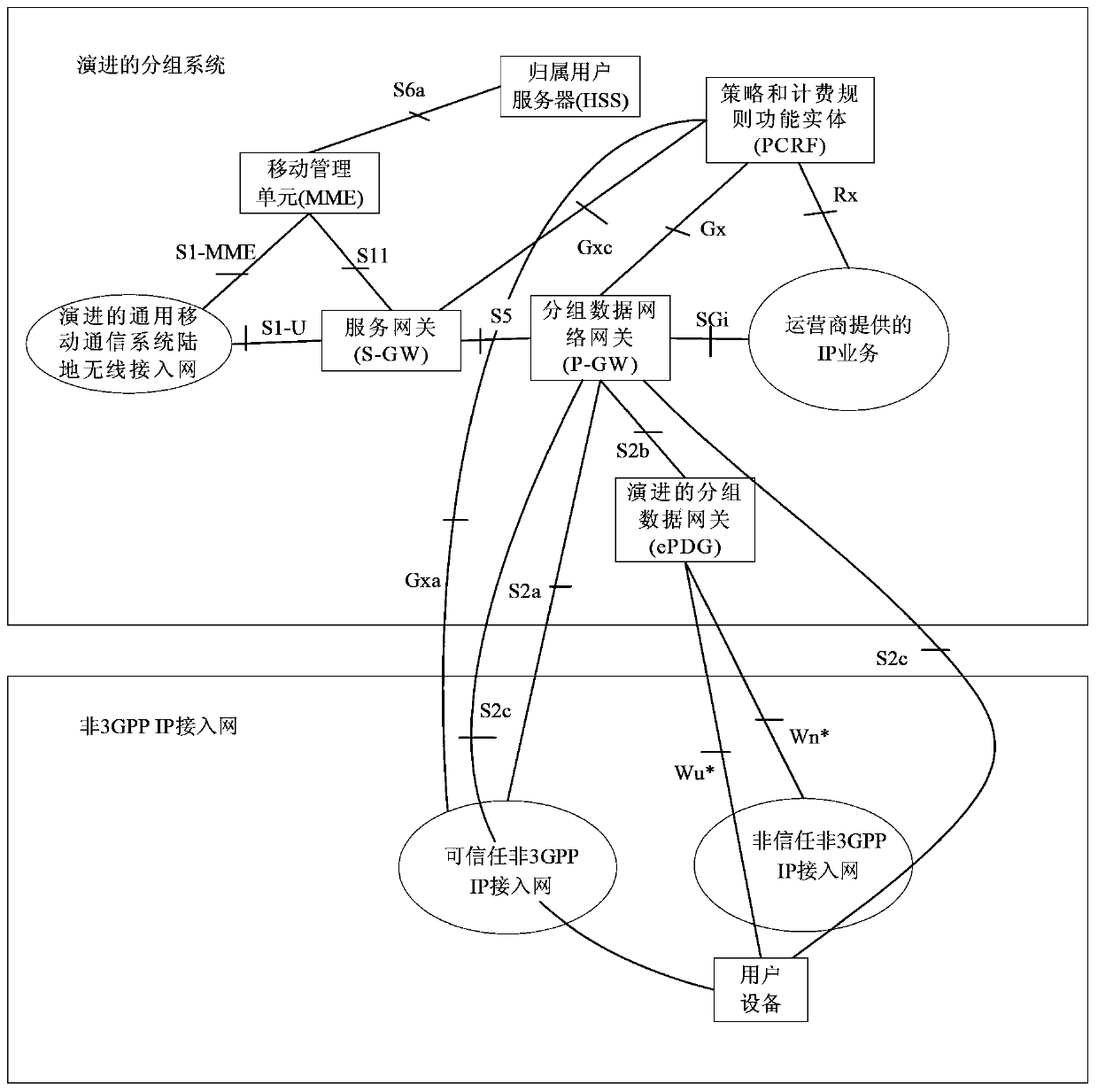
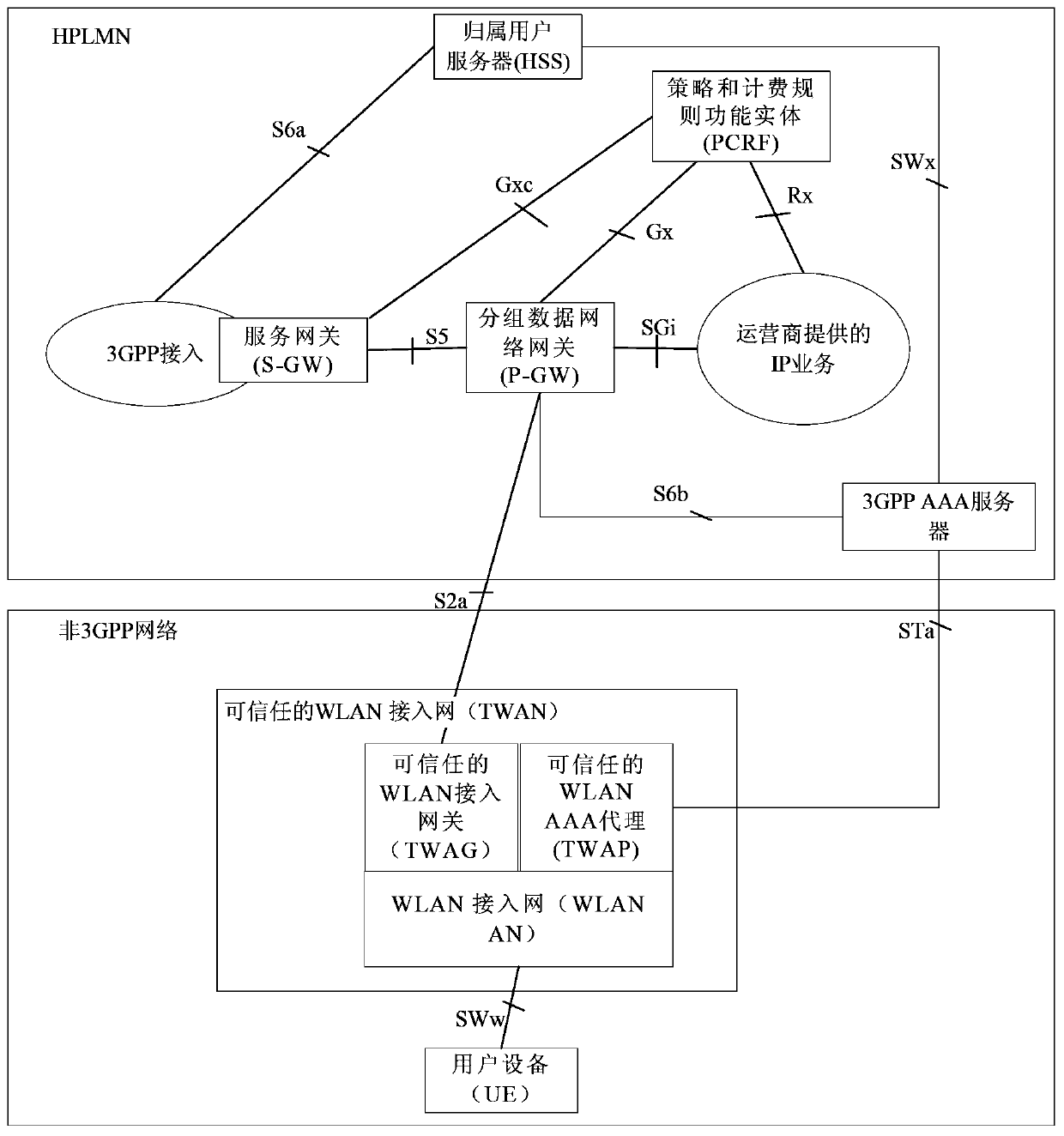
Billing control method and device
A charging control and charging strategy technology, applied in the communication field, can solve the problem of indistinguishable charging strategies, and achieve the effect of improving the scope of application and flexibility
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
[0084] Picture 10 It is a flowchart of the method for obtaining a charging policy according to the first embodiment of the present invention Figure one ,Such as Picture 10 As shown, when a user attaches from a WLAN for the first time and accesses an EPC with a trusted WLAN access network, the user signs a contract in the HSS during the Extensible Authentication Protocol (EAP) access authentication process The charging strategy is transferred to TWAN, and TWAP in TWAN passes the charging strategy to P-GW in the subsequent GTP establishment process through TWAG.
[0085] Step S1002: The UE and the WLANAN execute a non-3GPP-specific access procedure to establish an L2 connection.
[0086] Step S1004: WLANAN sends an EAP request identity (identity) message to the UE, requesting to obtain the identity of the terminal. Start the EAP authentication process.
[0087] Step S1006: The UE returns an EAP response / identity to the WLAN AN, which carries the identity of the terminal (the identi...
Embodiment 2
[0110] Picture 11 It is a flowchart of the method for obtaining a charging policy according to the second embodiment of the present invention Figure II ,Such as Picture 11 As shown, after the user accesses from 3GPP, he switches to the WLAN coverage area and uses a trusted WLAN access network to access the EPC. During the EAP access authentication process, the user signs in the HSS based on the access network The charging strategy of the type is sent to the TWAN, and the TWAP in the TWAN passes the charging strategy to the P-GW in the subsequent GTP establishment process through the TWAG.
[0111] Step S1102: The UE accesses from 3GPP, and there is a GTP tunnel on the S5 interface.
[0112] Step S1104: The UE discovers a trusted WLAN access system, and decides to switch from the attached 3GPP access to the discovered trusted non-3GPP access system.
[0113] Step S1106: The UE executes the access authentication and authorization process of the trusted non-3GPP access system. The 3...
Embodiment 3
[0130] Picture 12 It is a flowchart of the method for obtaining a charging policy according to the third embodiment of the present invention Figure three ,Such as Picture 12 As shown, when the charging policy based on the access network type at the HSS changes, the HSS informs the P-GW of the changed charging policy.
[0131] Step S1202: The charging policy based on the access network is changed at the HSS, and the HSS informs the AAA user that the charging policy based on the access network has changed through a subscription information update request message, and AAA informs the TWAP in the TWAN of the change at the same time.
[0132] Step S1204: After receiving the charging policy change request based on the access network in the TWAN, the TWAP returns an update response.
[0133] Step S1206: At the same time, the TWAP in the TWAN sends a bearer modification command through TWAG to inform the P-GW of the changed charging policy.
[0134] Step S1208: The PGW performs new charging...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com