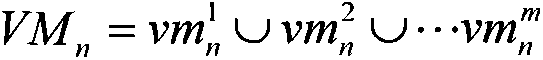Virtual machine security monitoring method based on cellular neural network
A neural network and security monitoring technology, applied in the field of information security, can solve problems such as not considered, and achieve the effect of improving monitoring efficiency
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
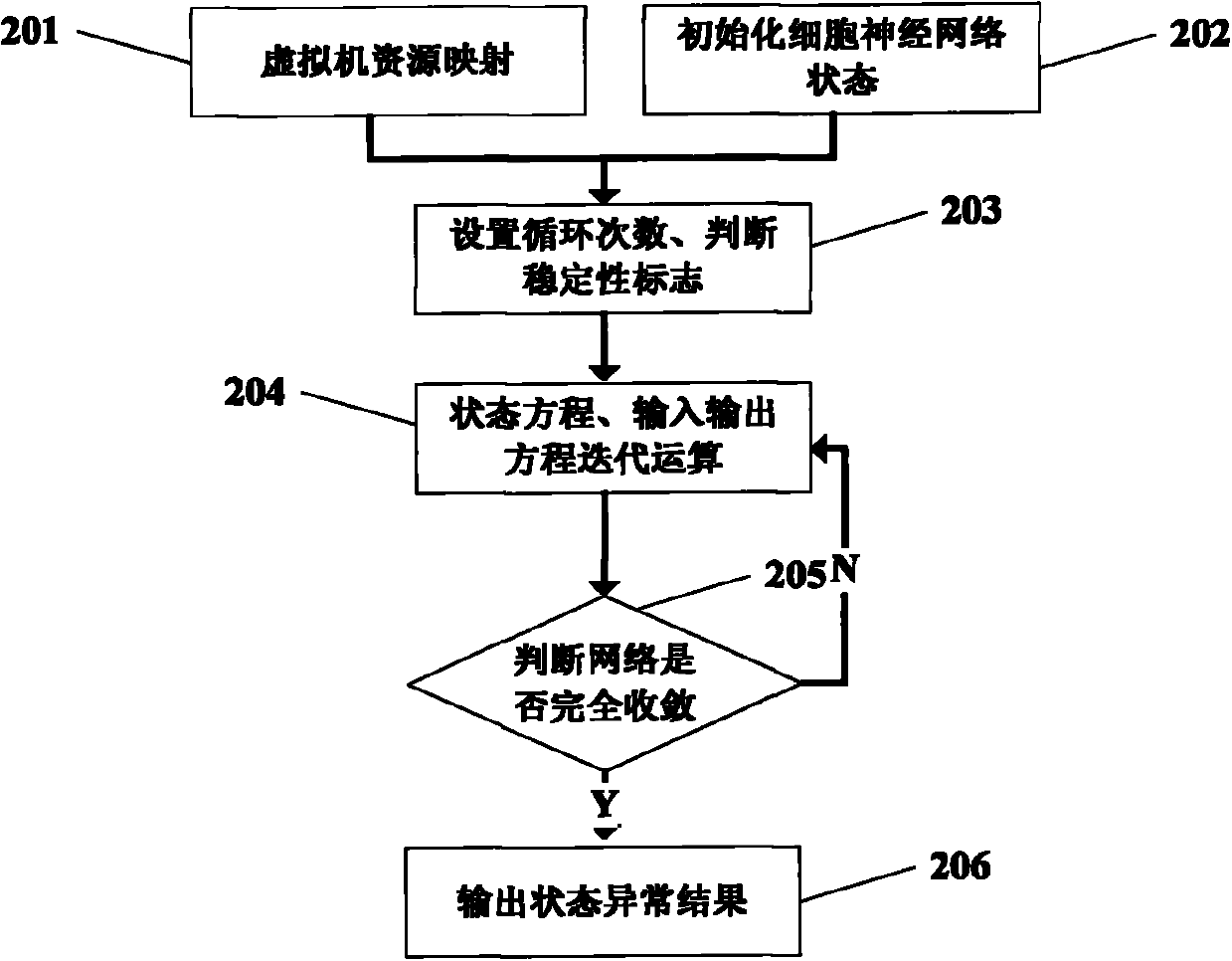
[0010] In view of the current cloud computing virtualization environment, when there are a large number of virtual machines in a physical machine, it is necessary to be able to monitor these virtual machines at the same time. The embodiment of the present invention is based on a cellular neural network as a parallel processing algorithm. It has the advantages of small amount of calculation and easy large-scale VLSI integration to realize real-time monitoring of the security status of customer virtual machines on the same physical machine.
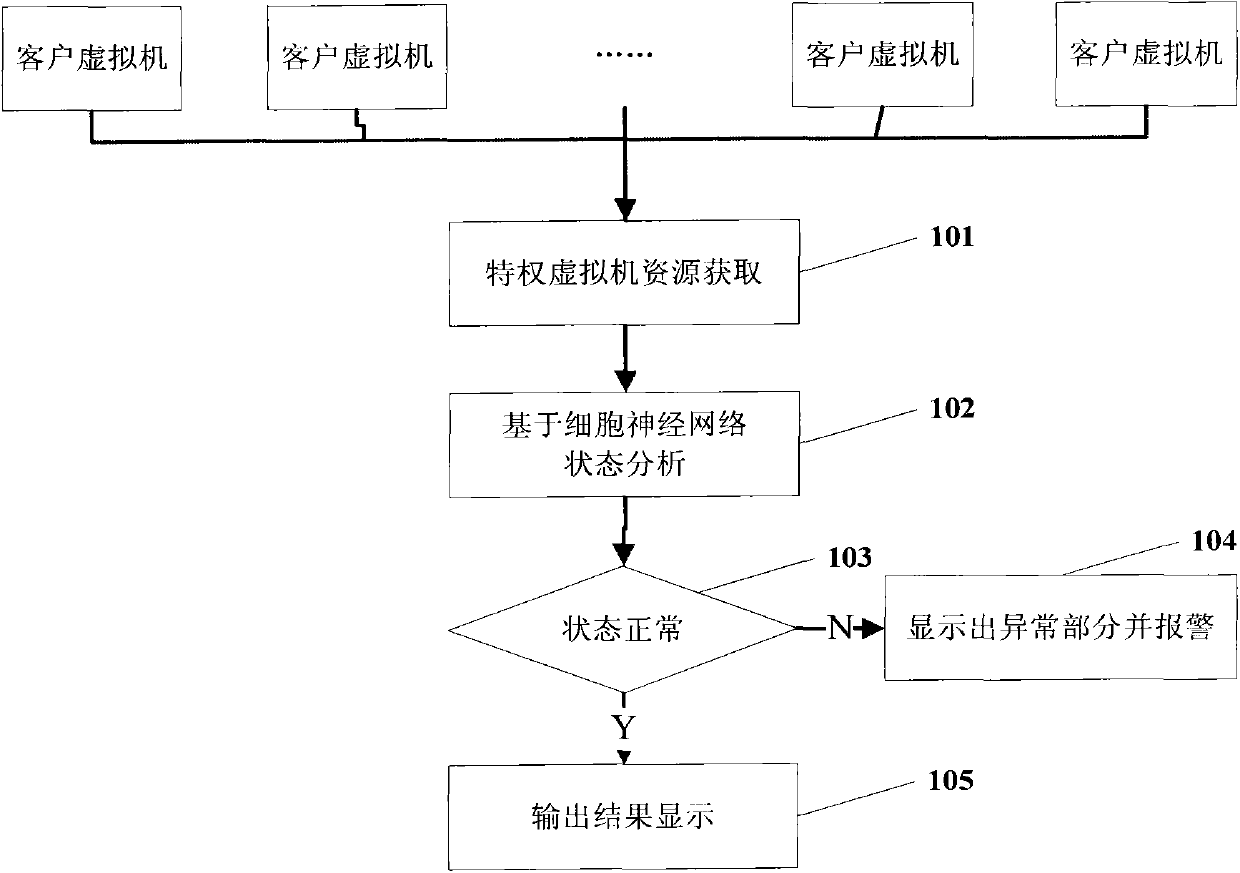
[0011] Such as figure 1 As shown, the cellular neural network-based virtual machine security monitoring method provided by the embodiment of the present invention includes the following steps:
[0012] Step 101, the privileged virtual machine dynamically obtains the resources of the client virtual machine;
[0013] Step 102, analyzing the obtained resource content based on the cellular neural network;
[0014] Step 103, determine whether ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com