Detecting and filtering method of spam mail based on counterfeit sender
A spam and filtering method technology, applied in the Internet field, can solve the problem of no way to authenticate and track the identity and address of spam, and cannot authenticate the sender of the mail, so as to achieve the effect of convenient installation, deployment and uninstallation, and high operating efficiency
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment
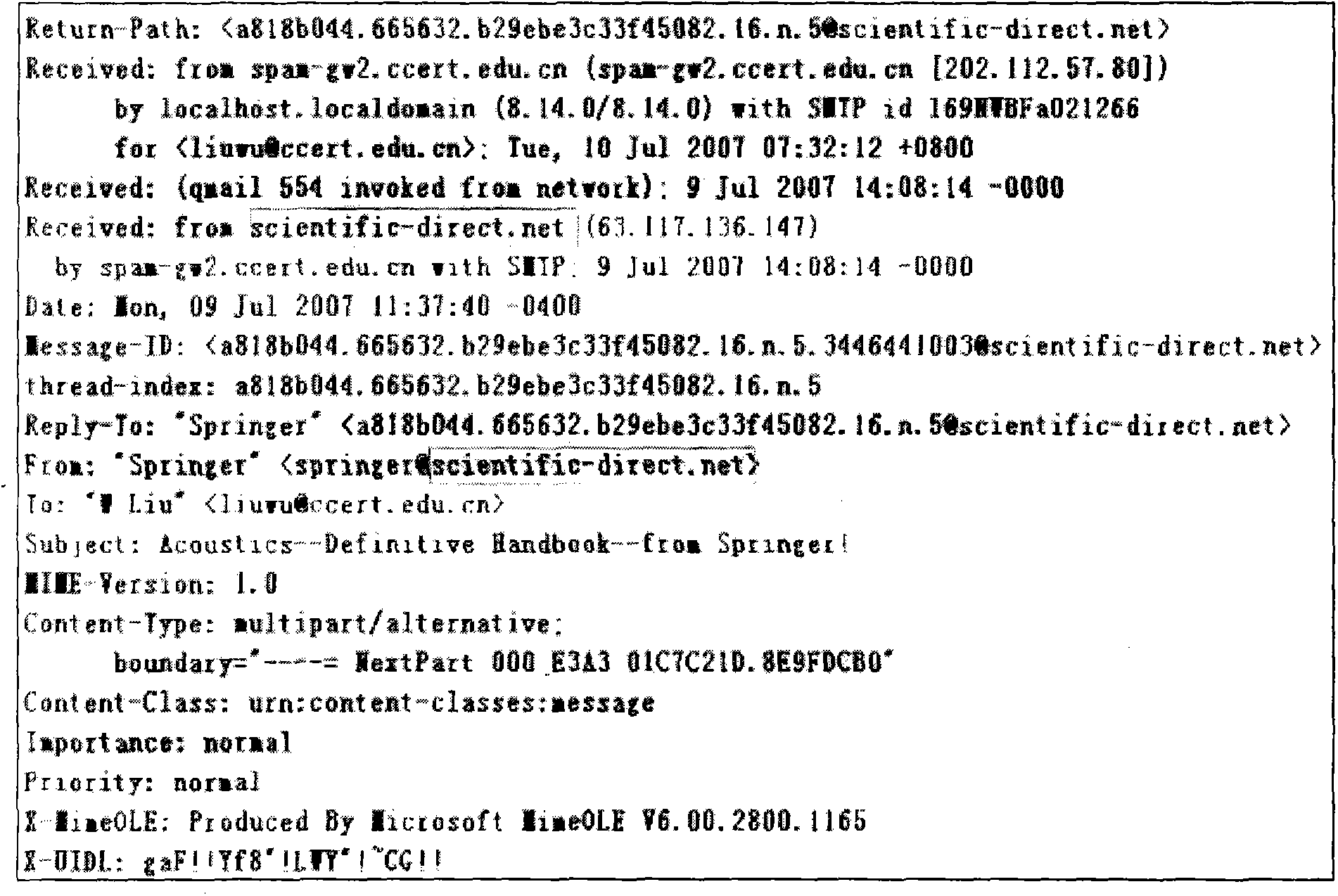
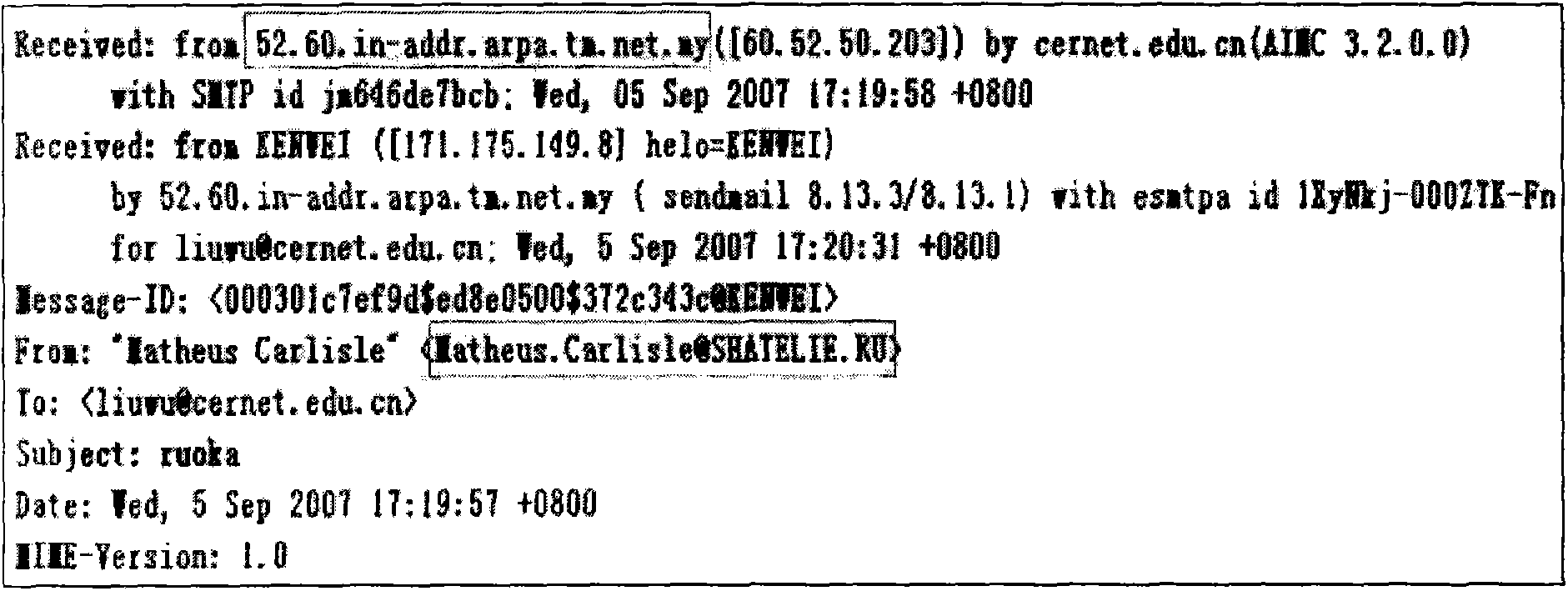
[0036] Because different mail systems do not strictly follow the relevant protocols and standards of e-mail, such as RFC822, etc., and the configuration errors of the mail system itself, some technical problems may be encountered when implementing FSpam detection and filtering. For example, when some non-standard mail systems send mail, what is written in the Received field is not the domain name but the IP address; in addition, some mail systems support virtual mail domains (that is, one mail system manages multiple mail domains at the same time). The mail domain ND written in the Received field is not necessarily the mail domain MD in the From field. This may bring some operational difficulties to the detection of FSpam, and the possibility of killing normal emails by mistake. For the above problems, technical means such as DNS forward query, reverse resolution, and NSLOOKUP query of MX records can be better solved.
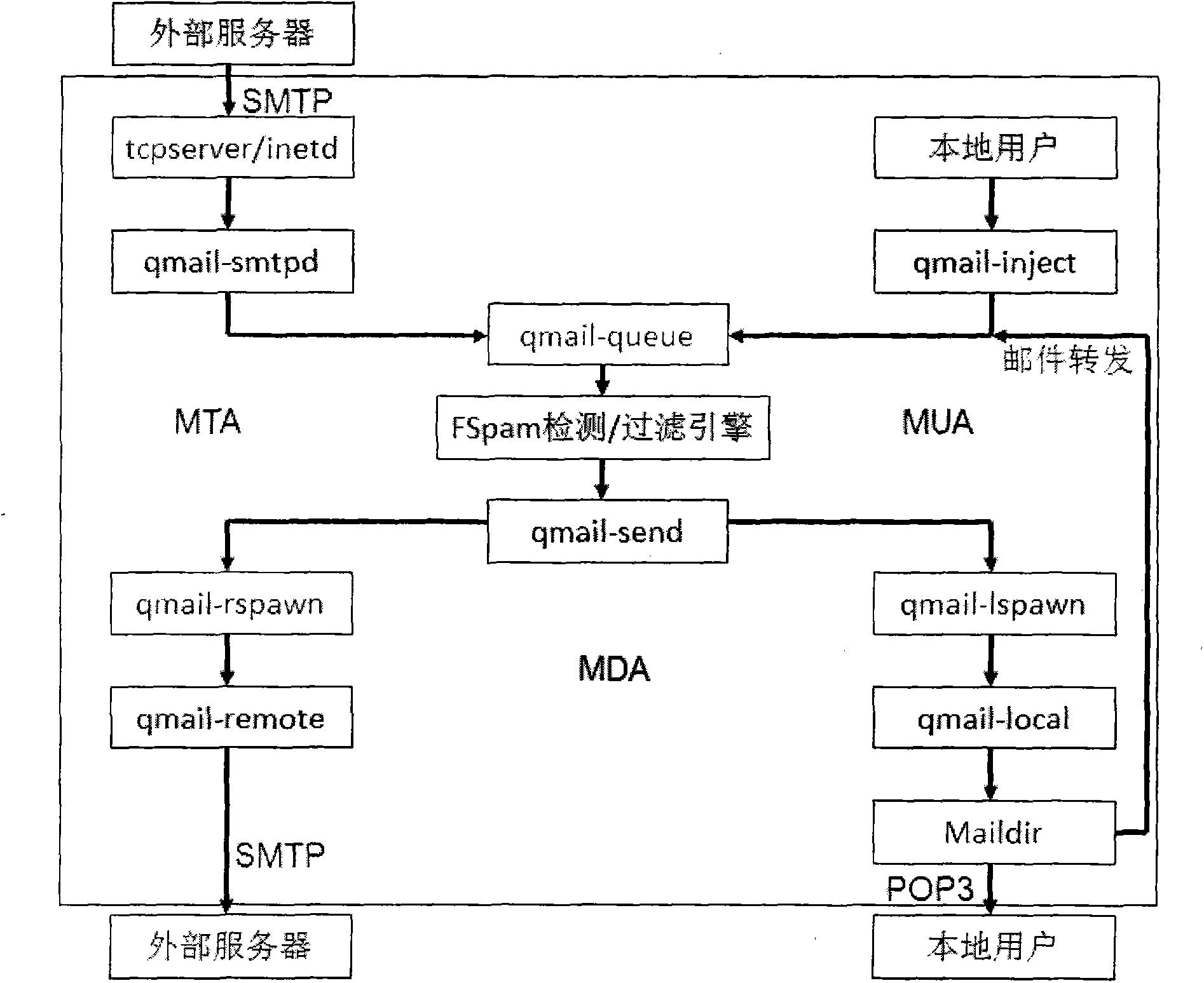
[0037] The spam detection and filtering method based on ...
experiment example
[0056] Performance test of FSpam detection / filtering engine AFSpam
[0057] In order to verify the functionality of the FSpam detection / filter, a design such as Figure 5 The shown FSpam filtering comparison experiment:
[0058] 1. Randomly send some FSpam emails and normal emails to the recipient l iuwucernet.edu.cn through the FSpam sending platform
[0059] 2. The FSpam detection / filter Anti-FSpam is not deployed on the mail server cernet.edu.cn, and the mail server of cernet.edu.cn will automatically forward the mail sent to l iuwucernet.edu.cn to l iuwuvhost.galaxy.edu. cn
[0060] 3. The FSpam detection filter Anti-FSASpam is deployed on the mail server vhost.galaxy.edu.cn.
[0061] 4. If the Anti-FSpam detection and filtering system works normally, the mailbox of liuwucernet.edu.cn will receive all emails from FSpam senders, while the mailbox of liuwuvhost.galaxy.edu.cn can only receive FSpam Normal mail sent by the sender. Then, by comparing the emails in liuwucer...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com