Piccolo encryption algorithm hardware achieving method
A hardware implementation, encryption algorithm technology, applied in the field of cryptographic algorithms, can solve the problem of occupying resources, increasing the chip implementation area, and not conducive to repeated operation of the same module.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
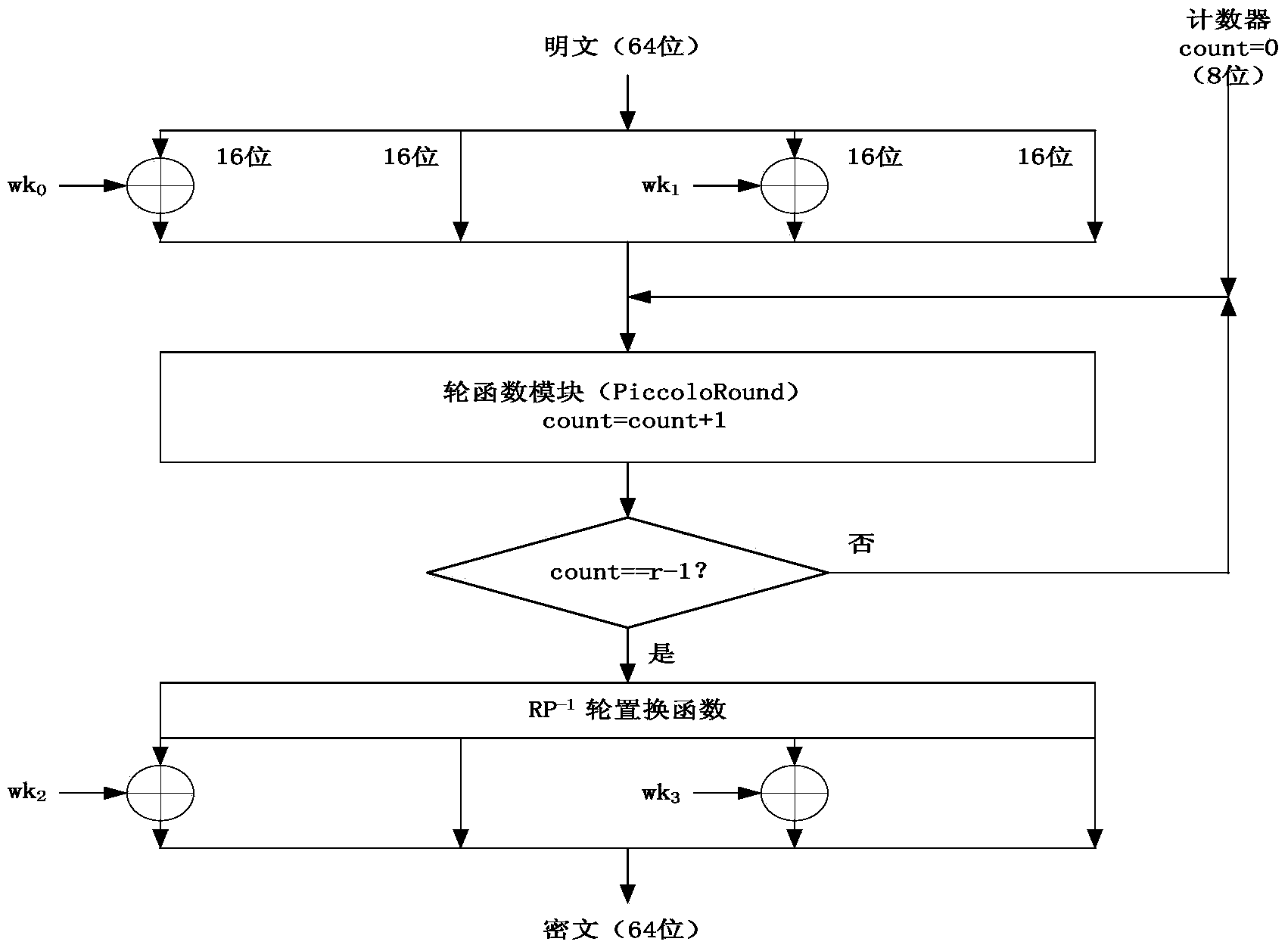
[0070] Piccolo-80 encryption algorithm optimization principle and specific operation process are as follows:
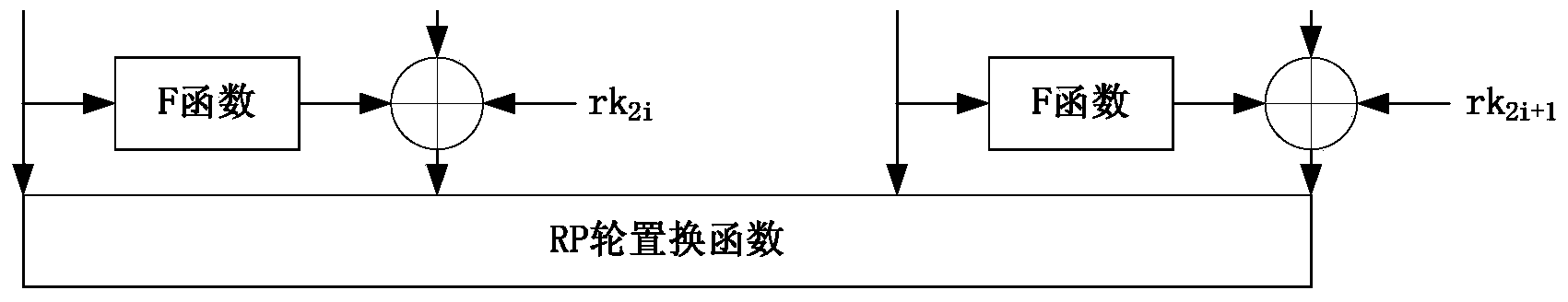
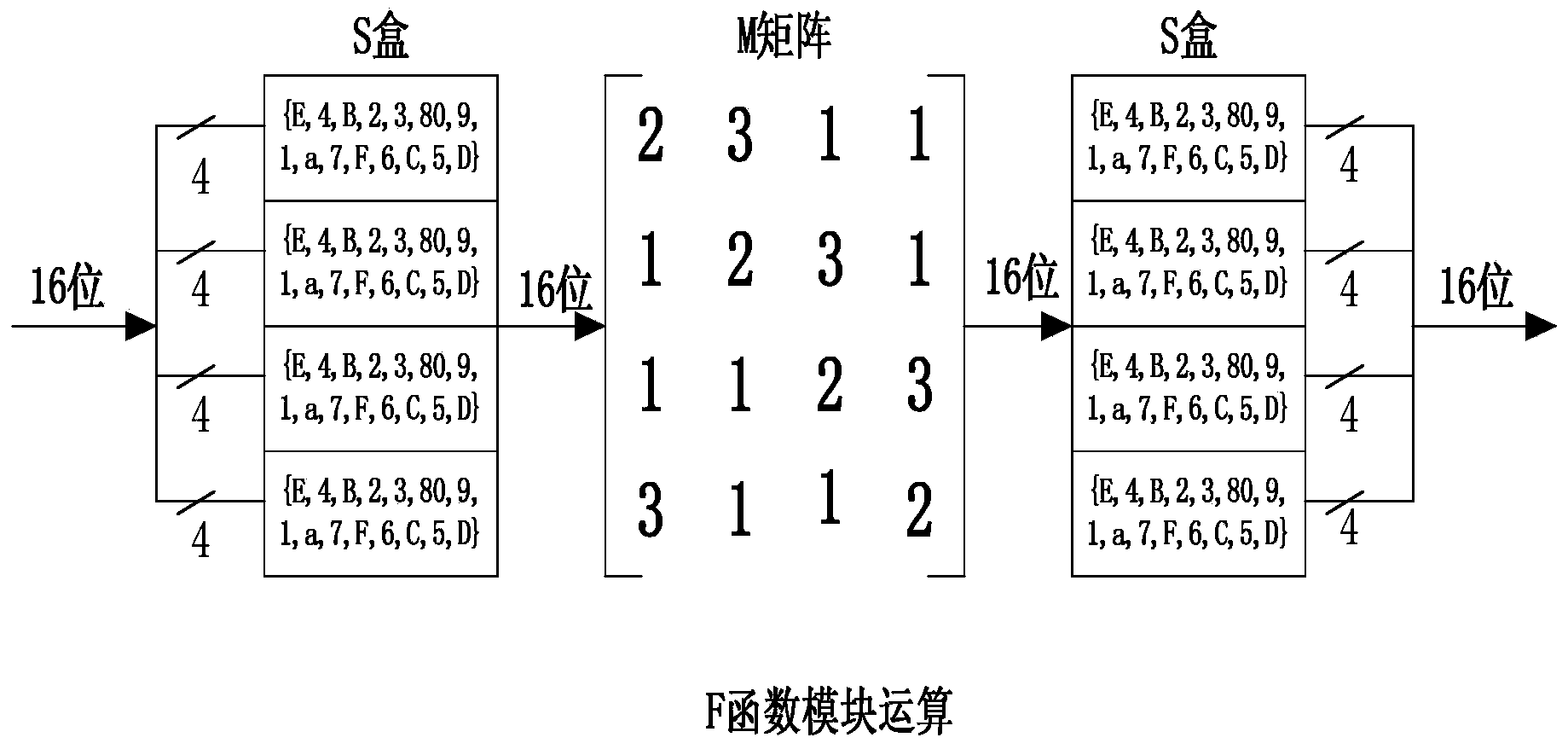
[0071] The encryption operation includes the following modules: a constant update module (UpdateConstant), an F function transformation module (Function), a round function module (PiccoloRound), and a main control module (Piccolo).
[0072] The UpdateConstant module includes four ports. In the code of the UpdateConstant module: the three input ports are the initial key key (80 bits), the number of rounds i (0i+1 (5 digits) is equal to the number of rounds i+1 and is represented by c_i; one output port is the subkey rk (by rk 2i 、rk 2i+1 composition). Use continuous assignment (assign) to construct by constant c_i Parameters, where the parameter generation code is: constant={c_i[3:7], 5'b00000, c_i[3:7], 2'b00, c_i[3:7], 5'b00000, c_i[3:7] }^32'hf1e2d3c, where 5'b00000 represents a 5-bit wide binary number. The value of q is used as the corresponding bit of the sel...
Embodiment 2
[0112] Piccolo-128 encryption algorithm optimization principle and specific operation process are as follows:
[0113] The encryption operation includes the following modules: a constant update module (UpdateConstant), an F function transformation module (Function), a round function module (PiccoloRound), and a main control module (Piccolo).
[0114] The UpdateConstant module includes input ports. In the UpdateConstant module code: key (128 bits), constant c i+1 (5 bits) is equal to the number of rounds i+1 (02i 、rk 2i+1 Composition), when (2i+2)mod8=0, use the network type variable up_key (128 bits) to indicate the readjustment of the key element value. Use continuous assignment (assign) to construct by constant c_i Parameters, where the parameter generation code is: constant={c_i[3:7], 5'b00000, c_i[3:7], 2'b00, c_i[3:7], 5'b00000, c_i[3:7] }^32'hf1e2d3c, where 5'b00000 represents a 5-bit wide binary number. The value of the last two digits of the constant c_i (equivalen...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com