An Authentication Method for Wireless Sensor Network Nodes
A sensor node and wireless sensor technology, applied in the field of Internet of Things, can solve the problems of high communication overhead, sensor node calculation and large storage capacity, etc., achieve the effect of low consumption, reduce real-time calculation amount, and ensure security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0021] The specific implementation manners of the present invention will be described in detail below in conjunction with the accompanying drawings.
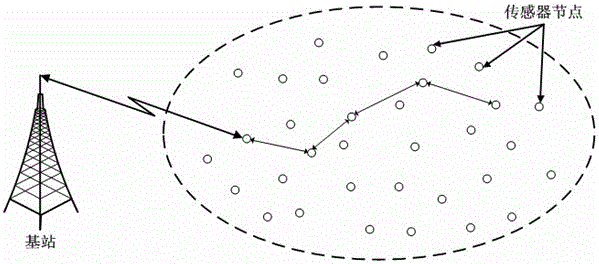
[0022] figure 1 It is a distributed network topology diagram. When the topology of the network is a distributed structure, sensor nodes communicate directly with the base station or communicate with the base station through other sensor nodes as a route. The authentication process is logically carried out directly between the base station and the sensor nodes.
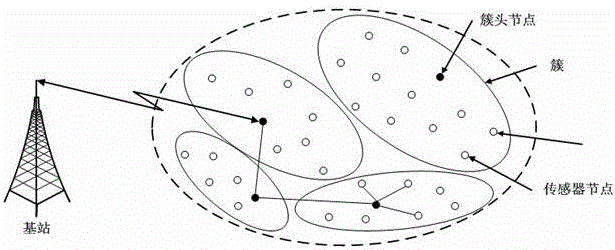
[0023] figure 2 It is a layer-cluster network topology diagram. When the topology of the network is a layered cluster structure, the sensor nodes only communicate directly with the cluster head nodes of the cluster, and the cluster head nodes have more computing resources and storage resources than the sensor nodes. Therefore, the process of authenticating the sensor node by the base station in step 3 of the method can be transplanted to the authentication of the se...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com