Method and apparatus for detecting integrity of video
A detection method and integrity technology, which is applied in the electronic field, can solve problems such as smart TVs not being able to start normally, affecting the stability of the smart TV system, and not being able to play video files normally.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
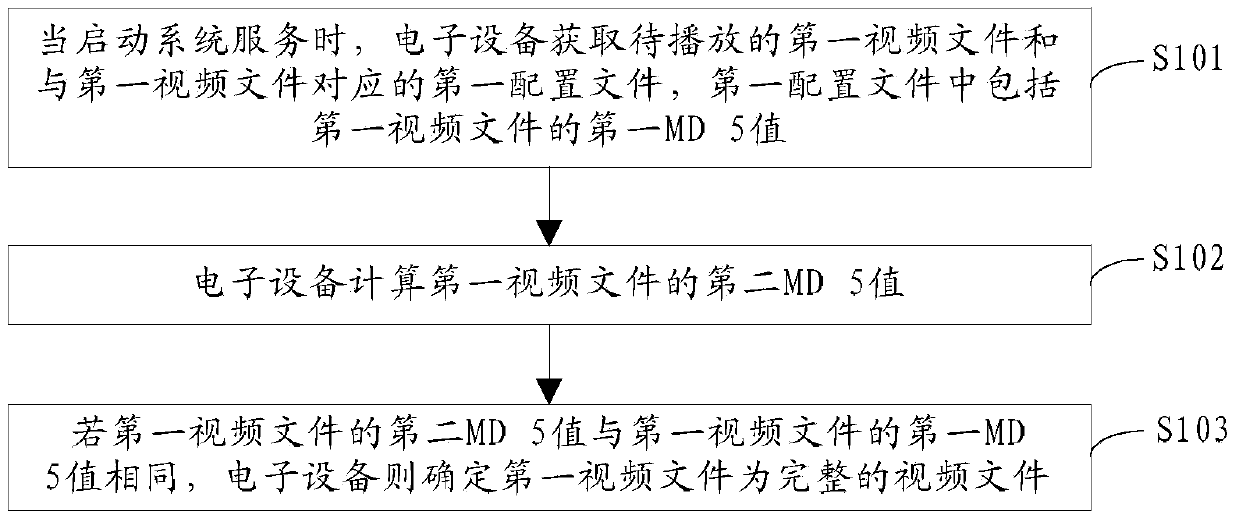
[0045] Embodiments of the present invention provide a method for detecting video integrity, such as figure 1 As shown, the method may include:
[0046] S101. When starting the system service, the electronic device obtains the first video file to be played and the first configuration file corresponding to the first video file, and the first configuration file includes the first MD5 (information digest algorithm 5) of the first video file , Message Digest Algorithm5) value.
[0047] Data integrity is one of the three basic points of information security, which refers to ensuring that information or data is not tampered by unauthorized or can be quickly discovered after tampering during the process of transmitting and storing information or data. In order to ensure the integrity of the data, digital signatures or hash functions are usually used to protect the ciphertext.
[0048] MD5 is a hash function widely used in the field of computer security to ensure the integrity and cons...
Embodiment 2
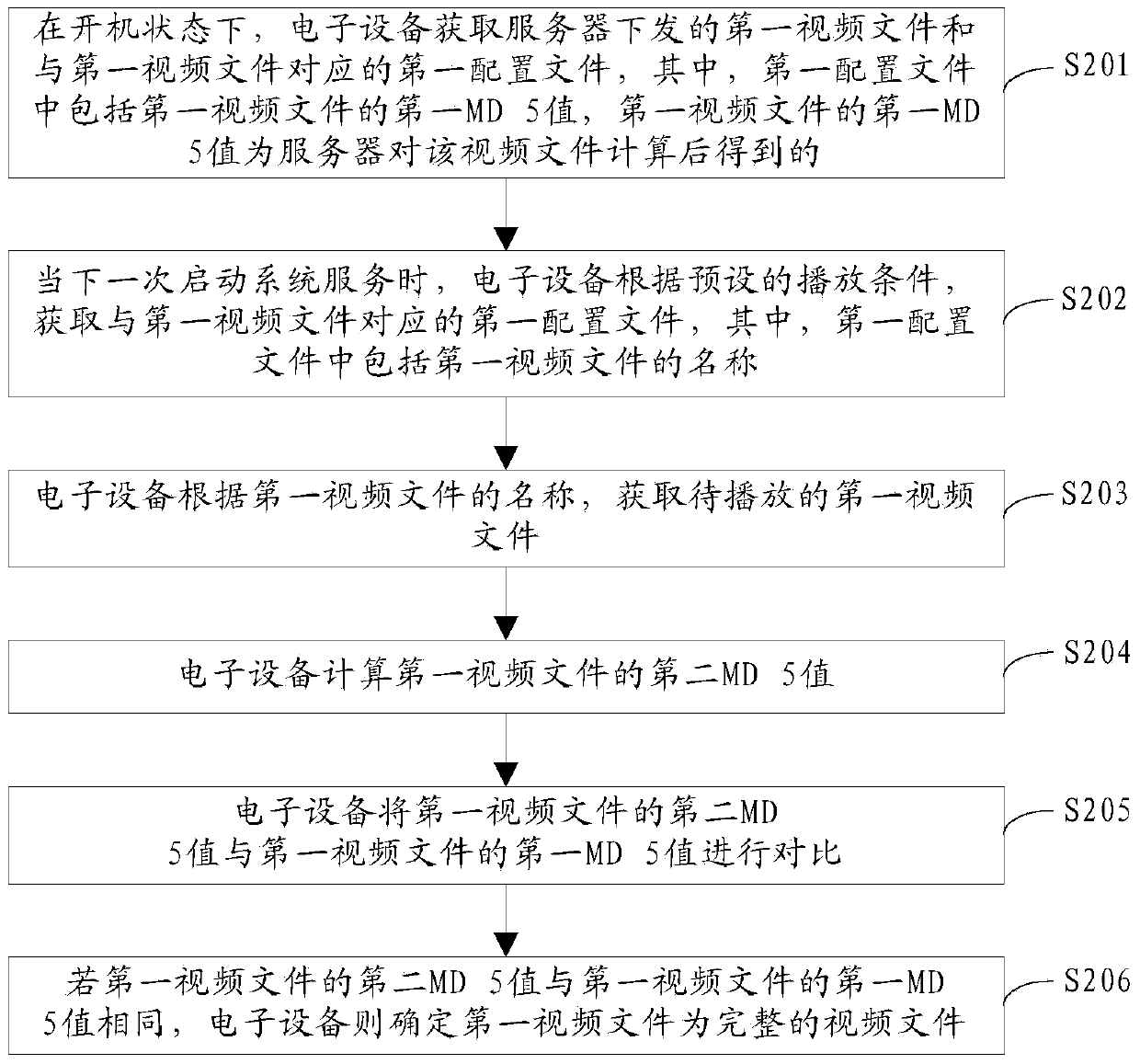
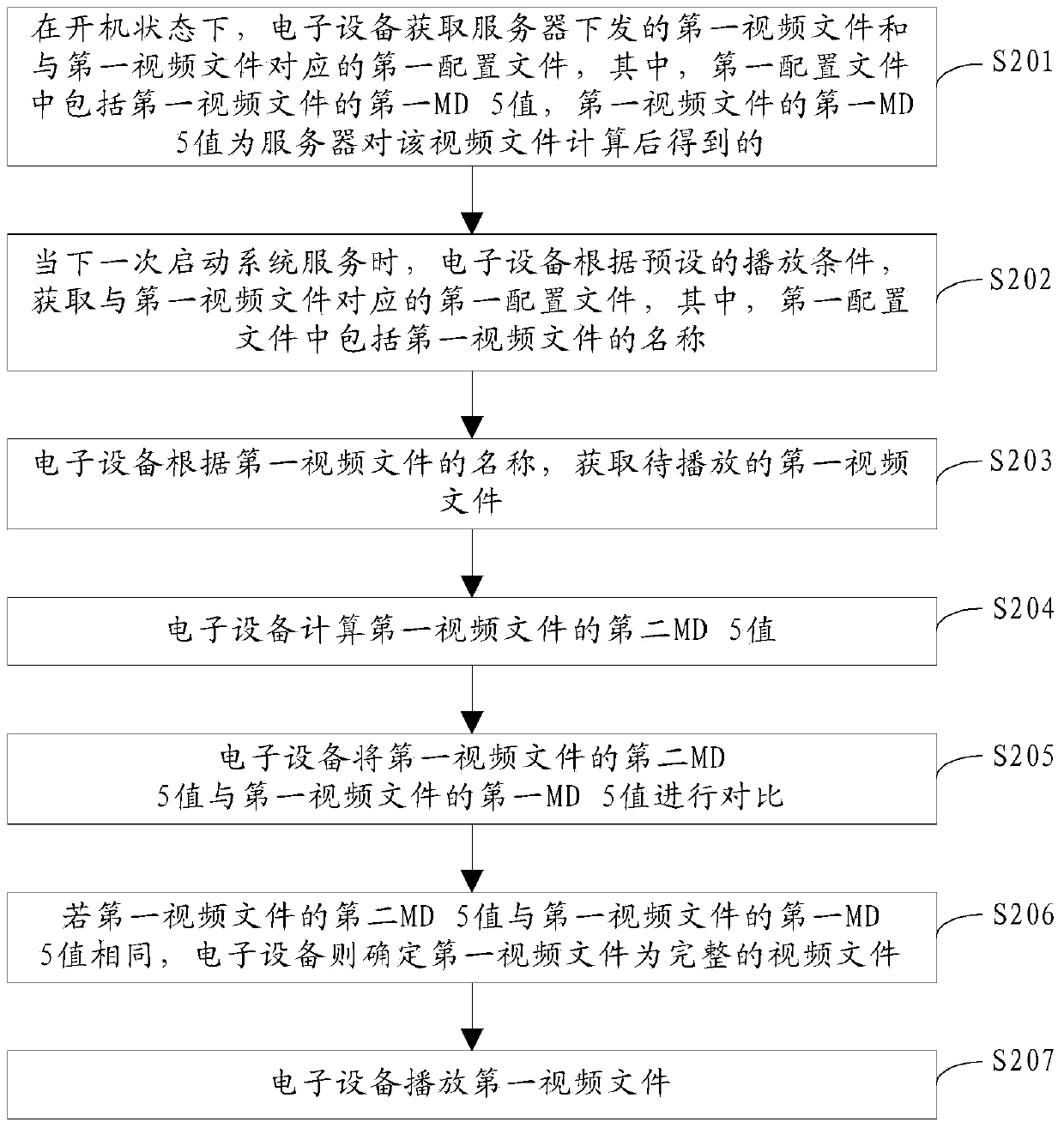
[0065] Embodiments of the present invention provide a method for detecting video integrity, such as figure 2 As shown, the method may include:
[0066] S201. In the power-on state, the electronic device acquires the first video file issued by the server and the first configuration file corresponding to the first video file, wherein the first configuration file includes the first MD5 value of the first video file, and the second The first MD5 value of a video file is obtained after the server calculates the video file.
[0067] Data integrity is one of the three basic points of information security. It refers to ensuring that information or data is not tampered with by unauthorized or can be quickly discovered after tampering. In order to ensure the integrity of data Security, usually using digital signatures or hash functions to protect the ciphertext.
[0068] MD5 is a hash function widely used in the field of computer security to ensure the integrity and consistency of in...
Embodiment 3
[0110] Such as Figure 5 As shown, the embodiment of the present invention provides an electronic device 1, and the electronic device 1 may include:
[0111] The acquiring unit 10 is configured to acquire a first video file to be played and a first configuration file corresponding to the first video file when the system service is started, and the first configuration file includes the configuration file of the first video file The first MD5 value.
[0112] The calculation unit 11 is configured to calculate the second MD5 value of the first video file acquired by the acquisition unit 10 .
[0113] A determining unit 12, configured to determine the The first video file acquired by the acquiring unit 10 is a complete video file.
[0114] Further, the obtaining unit 10 is also configured to obtain the first video file and the first configuration file issued by the server in the power-on state before starting the system service, wherein the first video file The first MD5 value ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com