File sharing method based on encryption and permission system
A file sharing and secret sharing technology, applied in electrical components, transmission systems, etc., can solve problems such as difficulty in satisfying security and sharing, inability to guarantee security of secret files, loss of sharing, etc., and achieve a simple and effective access control method , easy to maintain, large and small effects
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
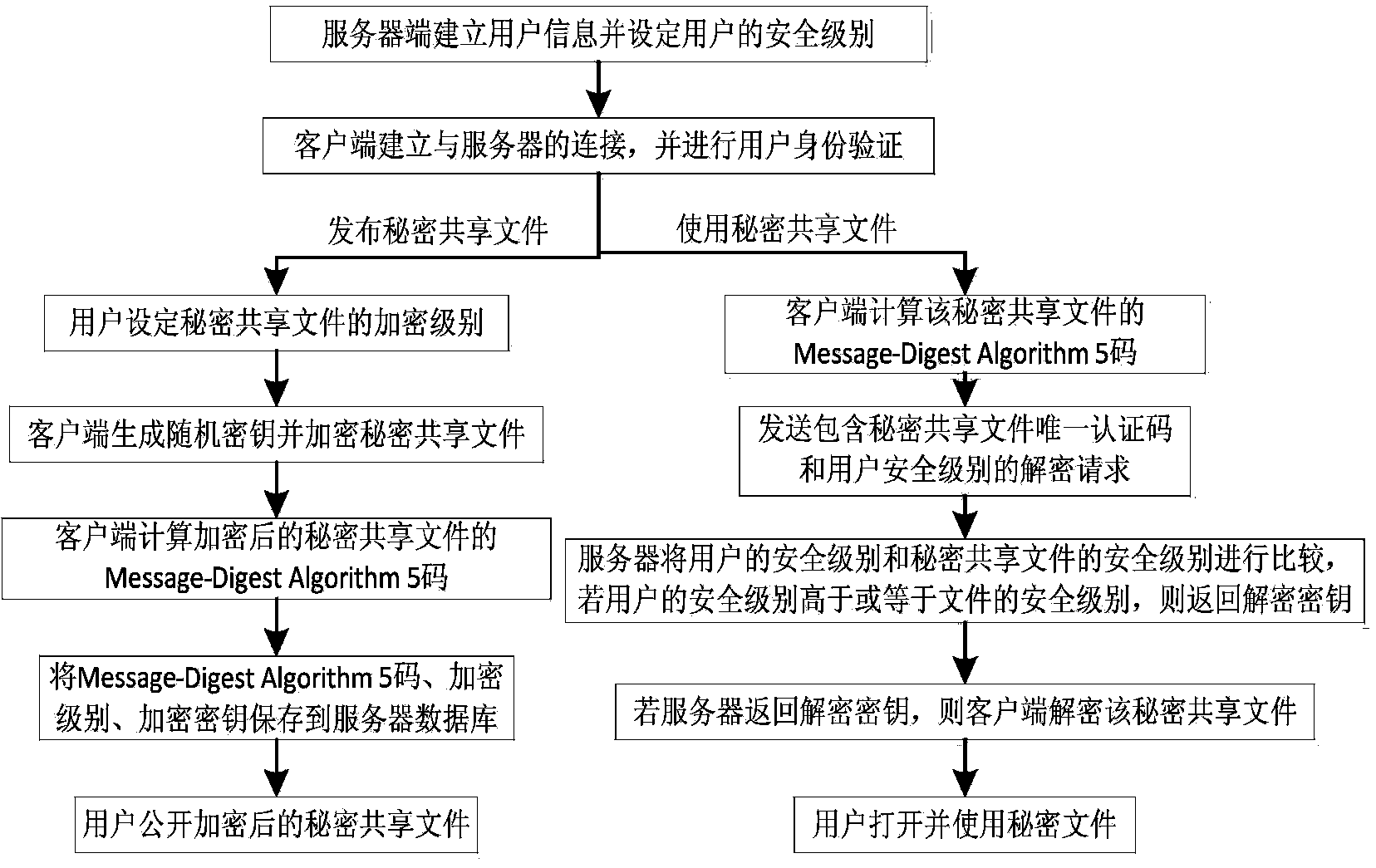
[0030] The present invention will be described in further detail below in conjunction with the accompanying drawings and specific embodiments.
[0031] like figure 1 Shown, the workflow of the present invention is:
[0032] Step 1: Create user information on the file sharing server and set the user's security level.
[0033] The user applies for registration, and then the administrator reviews the application user information. If the review is passed, the user's user name, login password and other information are entered, and a security level is set for the user according to the regulations of the unit.
[0034] Step 2, the user logs in to the file sharing client and performs identity verification.
[0035] The user enters the user name and password to log in, and the login information is sent to the server for verification, and then the server returns the verification result. If the verification is passed, the login is accepted; otherwise, the login is refused.
[0036] St...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com