Cloud resource authorizing method under cloud computing environment
A technology of cloud computing environment and cloud resources, which is applied in the field of cloud computing security, can solve problems such as lack, and achieve the effect of preventing random changes and protecting against loss
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
[0047] Embodiment 1, in the scenario where the cloud platform operator interacts with the cloud platform software and hardware vendors.
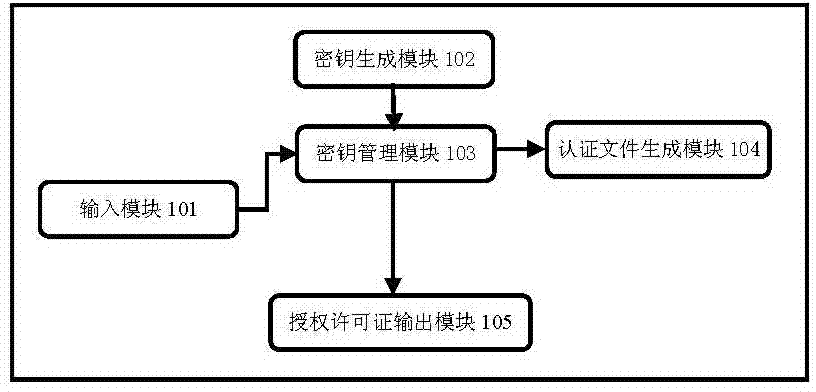
[0048] The authorization license generation module is deployed at the cloud platform software and hardware manufacturer, and the cloud resource authorization verification module is deployed at the cloud platform software and hardware manufacturer or cloud platform operator;
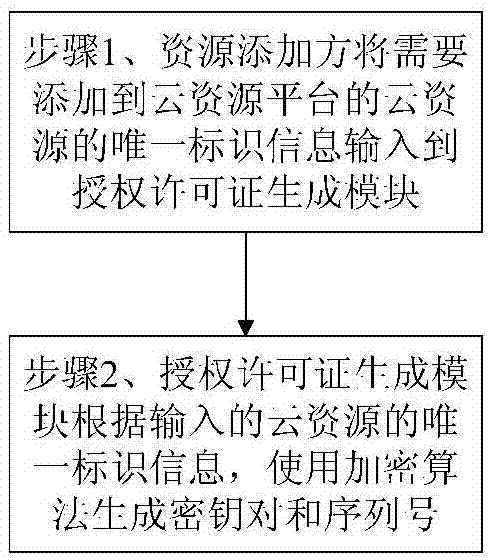
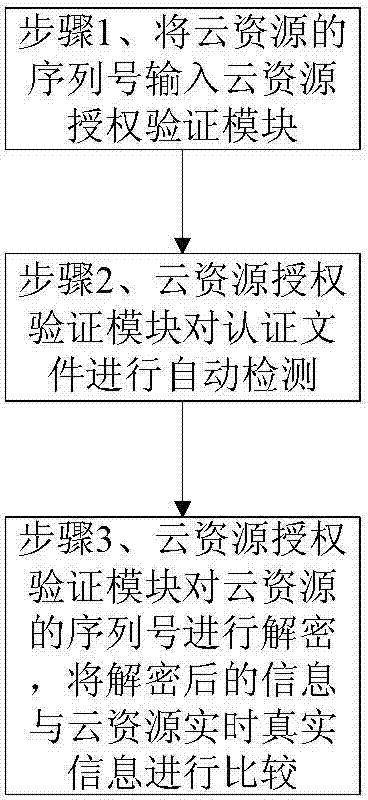
[0049] Such as figure 1As shown, when a new cloud resource needs to be added, an authorization step is performed. The authorization step is completed by an authorization license generation module set on the cloud resource platform. The authorization step includes the following steps:
[0050] Step 1. The resource adding party inputs the unique identification information of the cloud resources to be added to the cloud resource platform into the authorization license generation module;
[0051] The resource adding party is the cloud platform operator;
[0052] What is a...
Embodiment 2
[0066] Embodiment 2, in the scene where the cloud platform tenant interacts with the cloud platform operator.
[0067] Both the authorization license generation module and the cloud resource authorization verification module are deployed at the cloud platform operator.
[0068] Such as figure 1 As shown, when a new cloud resource needs to be added, an authorization step is performed. The authorization step is completed by an authorization license generation module set on the cloud resource platform. The authorization step includes the following steps:
[0069] Step 1. The resource adding party inputs the unique identification information of the cloud resources to be added to the cloud resource platform into the authorization license generation module;
[0070] The resource adding party is a cloud platform tenant;
[0071] What is added is software cloud resources, usually for software or software instances, and the unique identification information of cloud resources is the ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com