A secure re-encryption method for cloud data privacy protection
A privacy protection and re-encryption technology, applied in the field of computer security, can solve problems such as user loss, high consumption cost, user data leakage, etc., to achieve the effect of improving security and efficiency, reducing re-encryption overhead, and improving security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
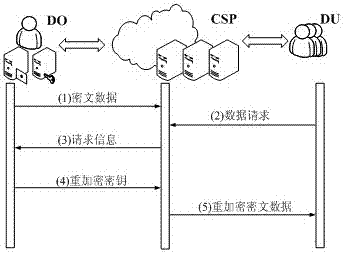
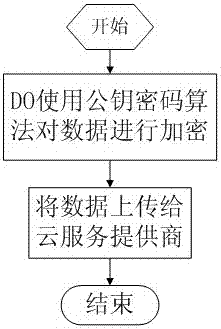
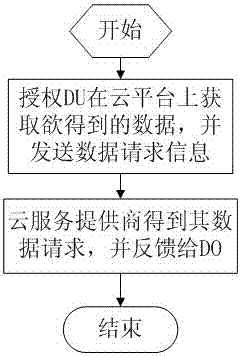
[0049] To solve the problem of incomplete trustworthiness of cloud service providers, the present invention proposes a security model for cloud data services, and converts the ciphertext data of the data owner into a ciphertext data that can be decrypted by the data user by means of the re-encrypted ciphertext conversion feature. text, and ensure that the conversion operator cannot obtain any information of the plain text, forming a re-encryption scheme framework for cloud data privacy protection.
[0050] ElGamal algorithm is a relatively common encryption algorithm, which is based on the public key cryptosystem and elliptic curve encryption system proposed in 1984. For the problems caused by symmetric keys in cloud data services, the present invention constitutes a cloud data privacy protection security re-encryption method based on EIGamal according to the security and effectiveness characteristics of the EIGamal algorithm, so that the cloud data privacy protection security ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com