Authentication method, device and system
An identity verification method and identity verification technology, applied in user identity/authority verification, transmission system, payment system, etc., can solve problems such as low security, phishing problems, and affecting user data security, so as to improve security and improve Effectiveness, effectiveness of preventive means of phishing
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
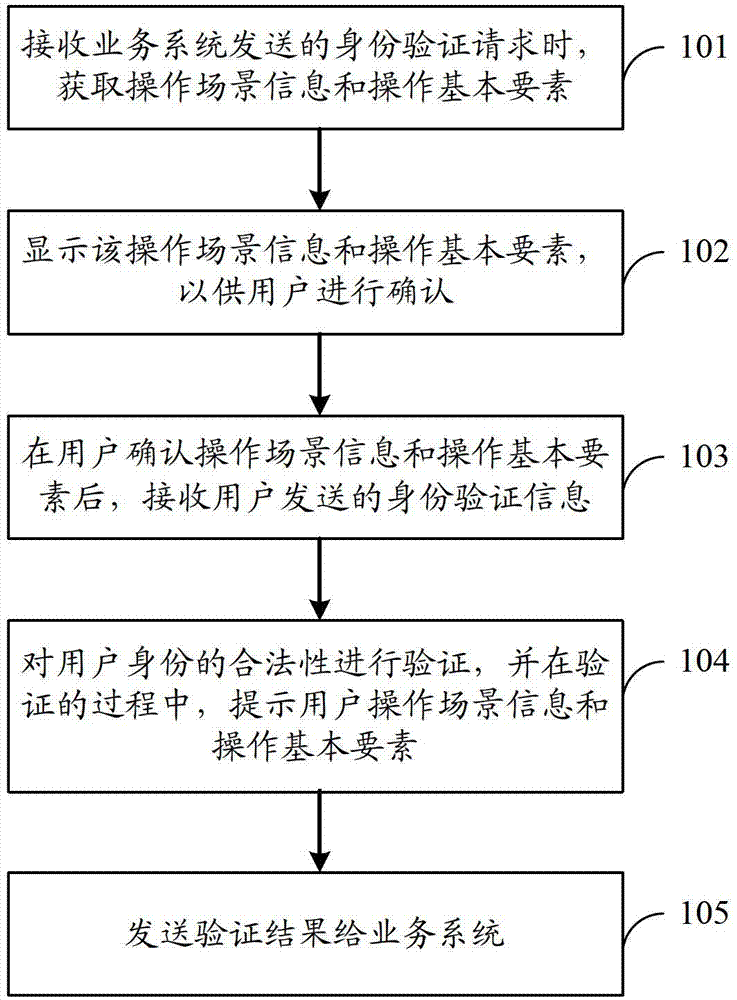
[0028] This embodiment will be described from the perspective of an identity verification device, and the identity verification device may specifically be a device such as a verification server.
[0029] An identity verification method, comprising: when receiving an identity verification request sent by a business system, obtaining operation scenario information and operation basic elements, displaying the operation scenario information and operation basic elements for confirmation by a user, and when the user confirms the operation scenario information After receiving the identity verification information sent by the user and verifying the legitimacy of the user's identity according to the identity verification information, and during the verification process, the user is prompted for the operation scene information and the operation basic elements, and the verification result is sent to business system.
[0030] Such as figure 1 As shown, the specific process can be as foll...
Embodiment 2
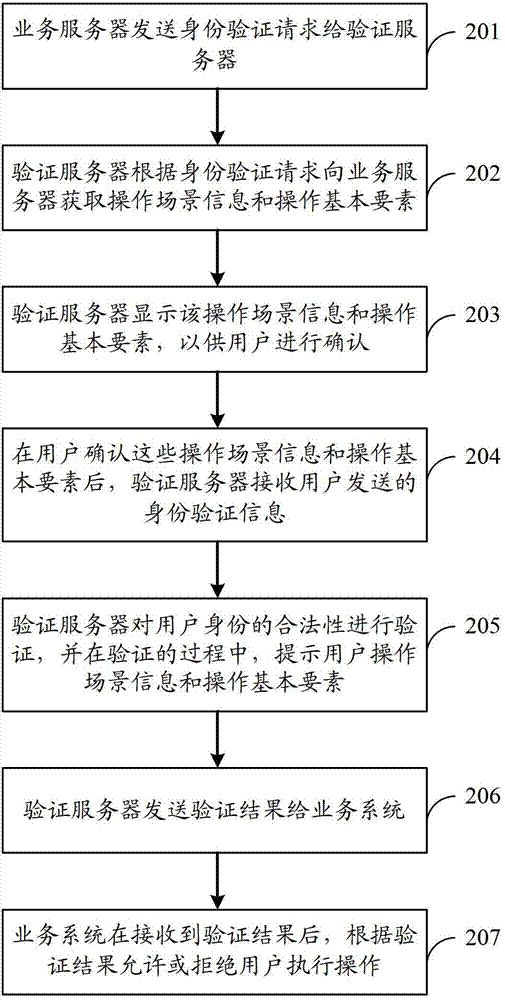
[0053] According to the method described in Embodiment 1, an example will be given below for further detailed description.
[0054] In this embodiment, description will be made by taking the identity verification device as an authentication server and the business system as a business server as an example.
[0055] Such as figure 2 As shown, an authentication method, the specific process can be as follows:
[0056] 201. The service server sends an identity verification request to the verification server.
[0057] 202. After receiving the identity verification request, the verification server acquires operation scenario information and basic operation elements from the service server according to the identity verification request.
[0058] Among them, the operation scene information is mainly used to inform the user of the current operation status in a timely manner, which may specifically include information such as the operation name and / or operation status in the current ...
Embodiment 3
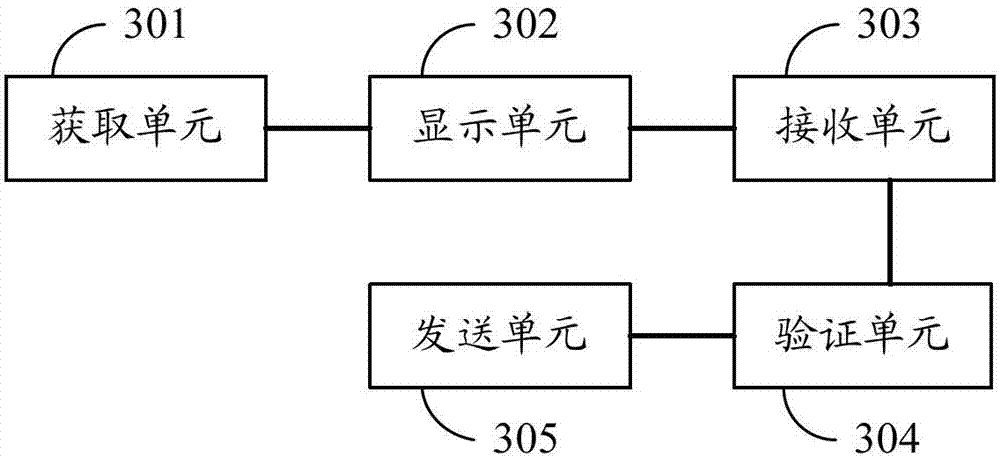
[0076] Correspondingly, the embodiment of the present invention also provides an identity verification device, such as image 3 As shown, the identity verification device includes an acquisition unit 301, a display unit 302, a receiving unit 303, a verification unit 304 and a sending unit 305;
[0077] The obtaining unit 301 is configured to obtain operation scene information and basic operation elements when receiving an identity verification request sent by the business system;
[0078] Wherein, the service system may specifically be a service server; the operation scene information is mainly used to inform the user of the current operation state in time, which specifically may include information such as the operation name and / or operation state in the current operation scene. The basic elements of operation are mainly used to help users define whether an operation is really an operation initiated by themselves.
[0079] For example, for a transfer operation, the basic ele...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com