Fine-grained cloud platform security access control method based on user identity capacity
A technology for secure access and user identity, applied in the field of fine-grained cloud platform security access control, can solve problems such as non-unique user attributes, unsuitable for pervasive cloud environment, and unclear division of permissions, achieving low cost and protection User privacy, the effect of avoiding communication bottlenecks
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0031] The invention will be described in further detail below in conjunction with the accompanying drawings.
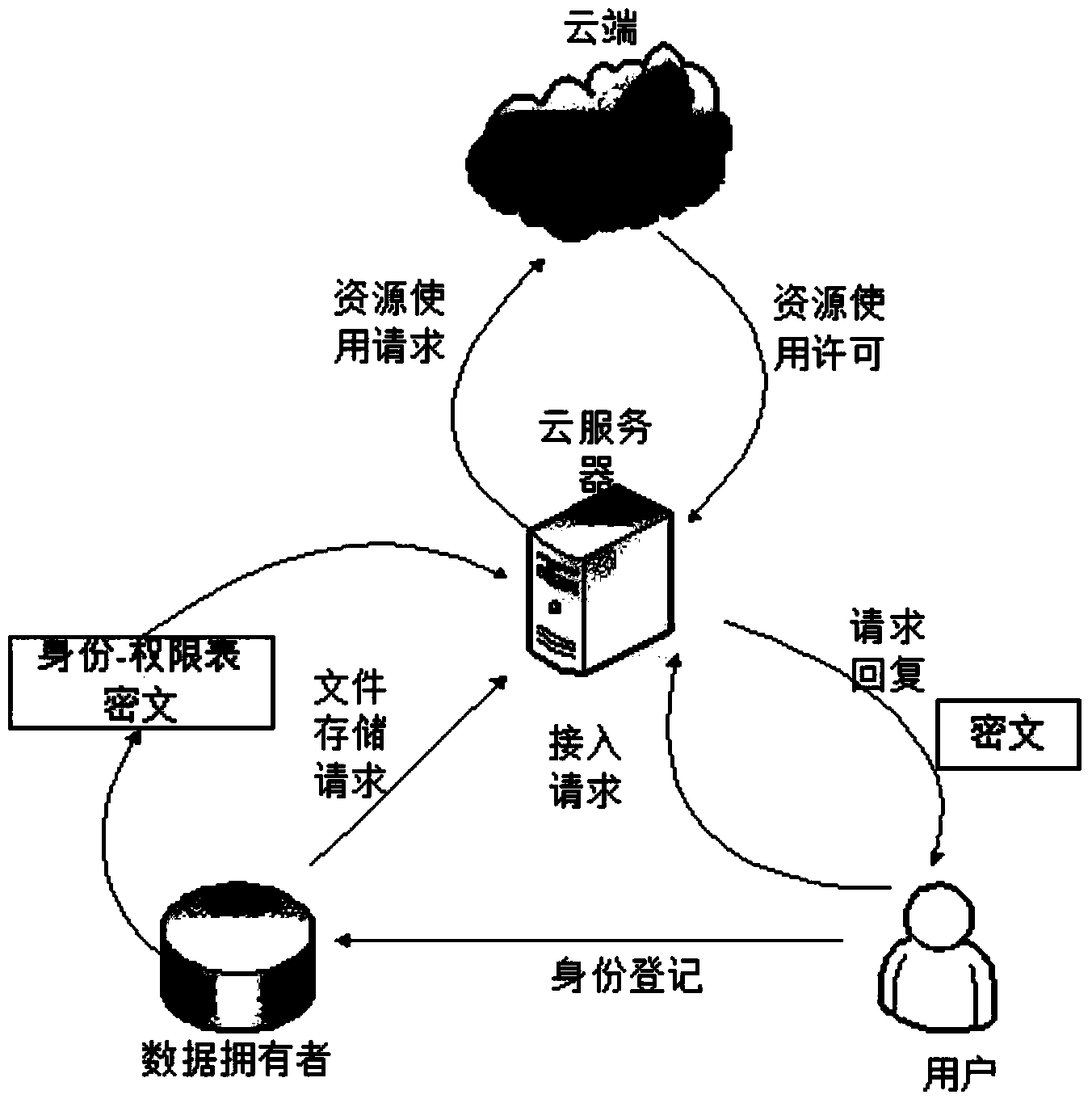
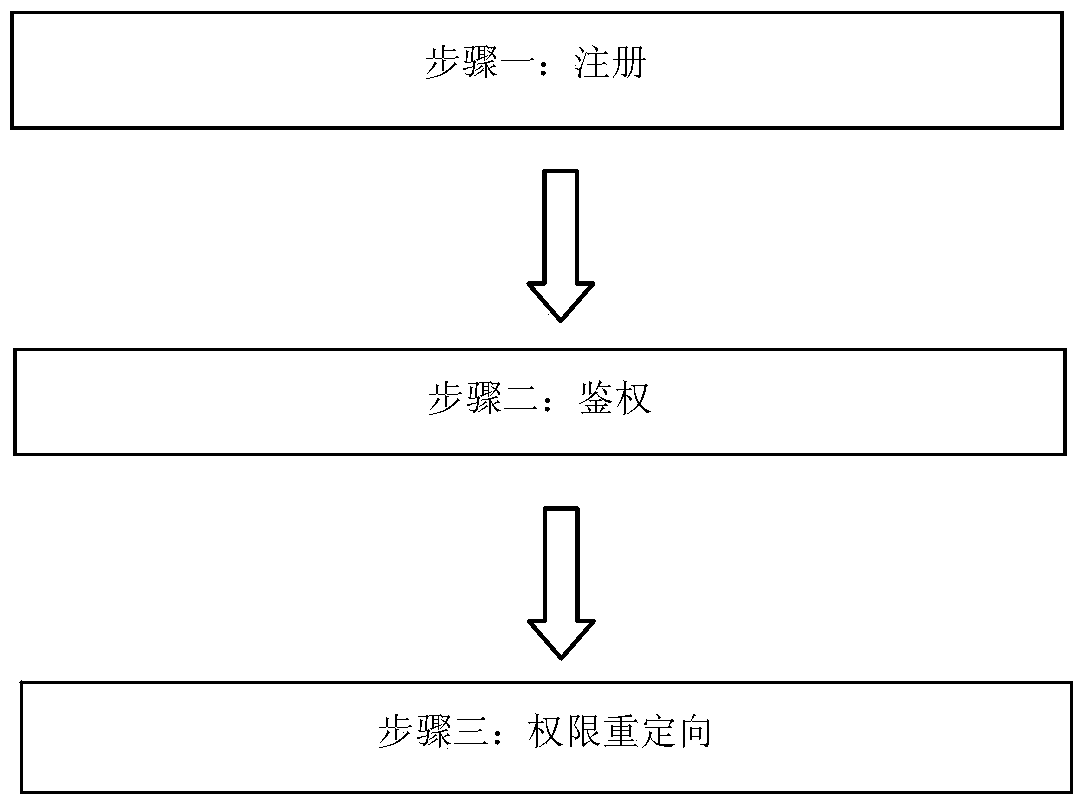
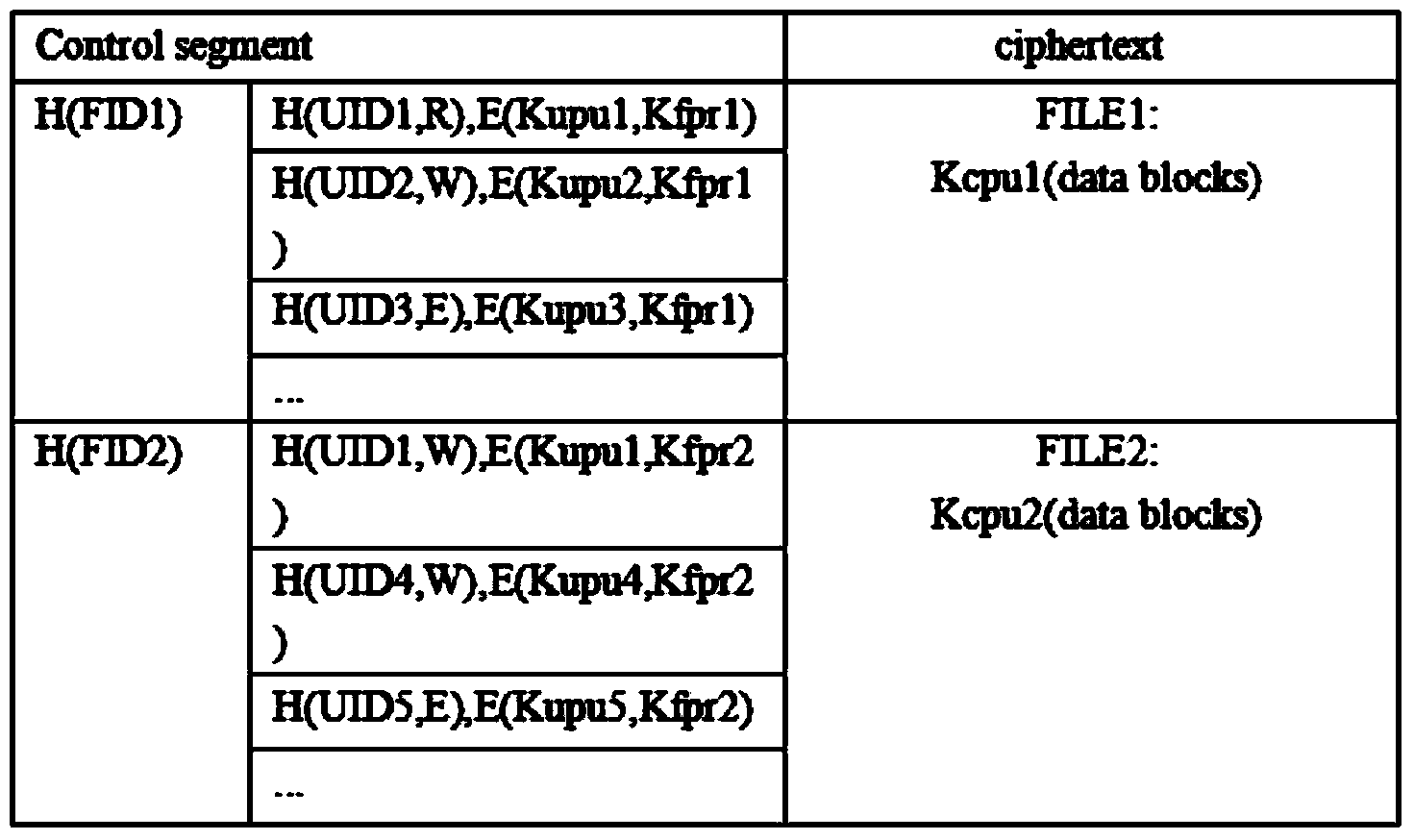
[0032] Such as figure 1 with figure 2 As shown, in this embodiment, a fine-grained cloud platform security access control method based on user identity capability, the system of the present invention is composed of four functional entities: cloud, cloud server, user and DO. Among them, DO is the uploader and resource owner of cloud data, encrypts files and formulates related access strategies. Users are sharers of cloud data and have access rights to read, write, and execute files, but these rights can only be obtained after registration at DO. The cloud server undertakes an important task. It stores the identity-authority-ciphertext table uploaded by the DO. It is not only an agent of DO access control, but also a service provider of cloud computing storage. The cloud is a physical node composed of computer clusters, which only has the function of storage.
[0...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com