Certificate false-proof verification method base on identification authentication technology
A technology for identification authentication and certificate, which is applied in the field of ID photo, seal, signature and biometric information security and authentication, and can solve the problems of poor security performance, high cost of establishing a system, easy to be imitated, etc., and is easy to generate and read. The effect of taking, preventing impersonation and forgery, and being easy to verify
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
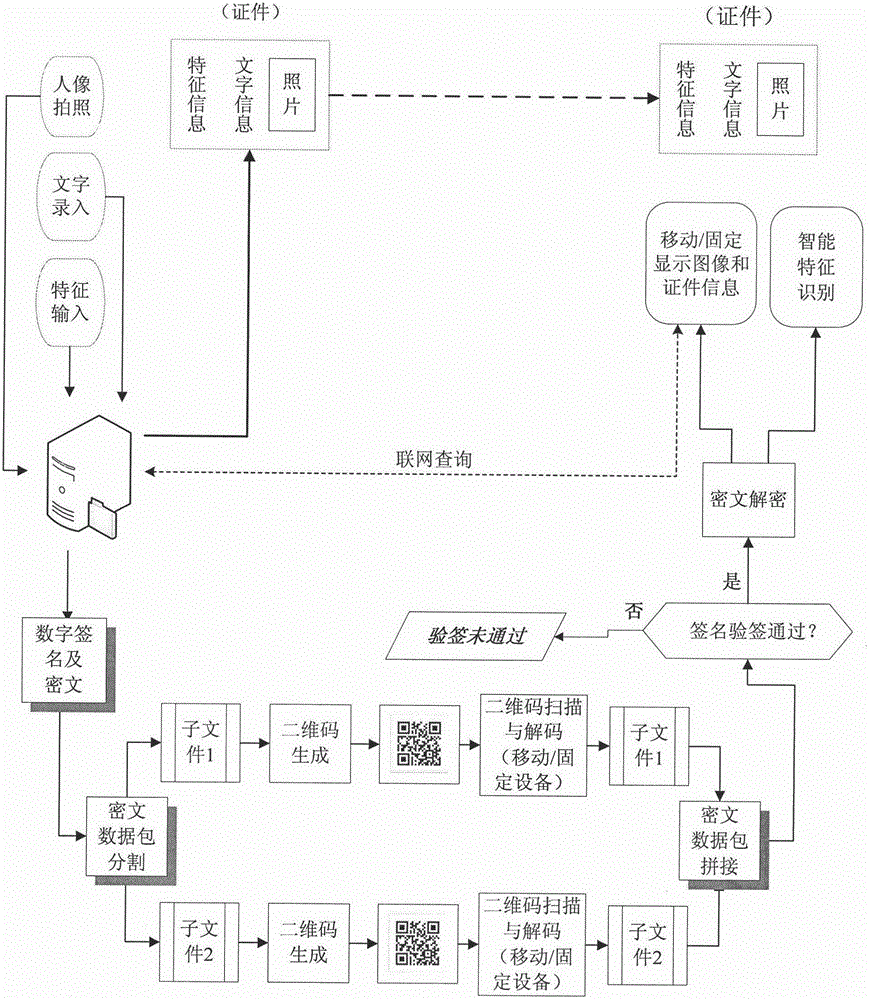
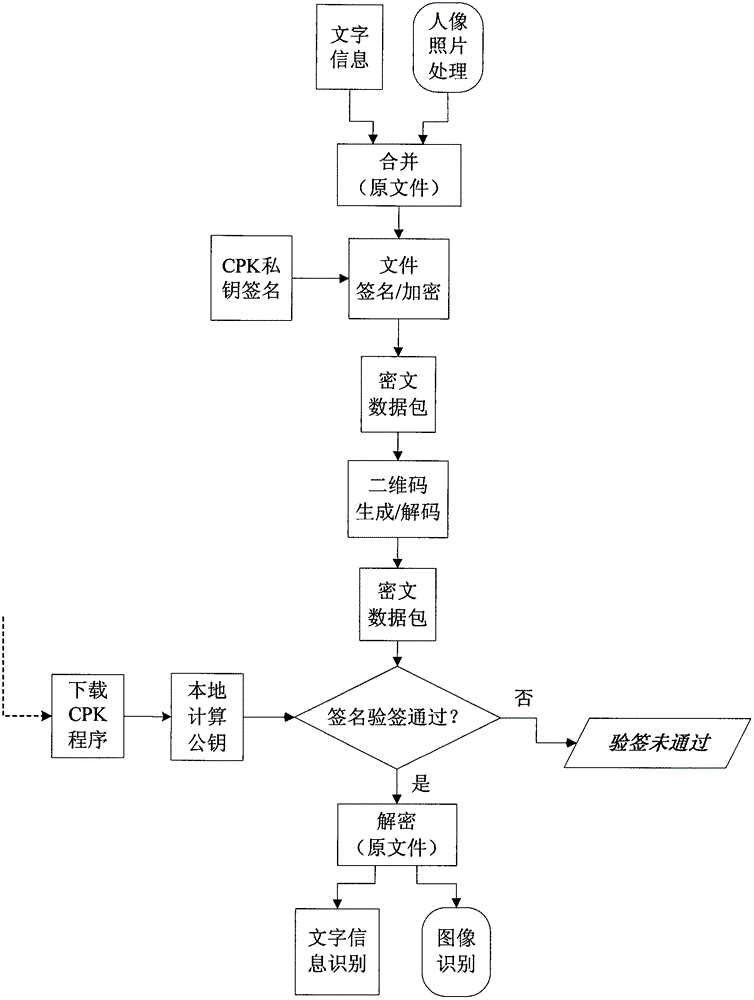
[0039] Example 1: see figure 2 , the identity information of the certificate in this embodiment includes the image of the portrait photo and the text information of the certificate.
[0040] Specific steps are as follows:
[0041] Step 1, document information input: After the certificate issuer takes a photo of the certificate holder, on the one hand, the photo is directly output, printed or pasted on the certificate; on the other hand, the photo is properly compressed to generate a compressed image file , to combine the image file and the certification text information into a certified plaintext original document. Issuing information includes, but is not limited to: photographs, written records of the certificate, name of the issuing authority, place and time of issuing the certificate, and other information.
[0042] Step 2, encryption and two-dimensional code generation: use the CPK identification private key based on identification authentication to digitally sign the o...
Embodiment 2
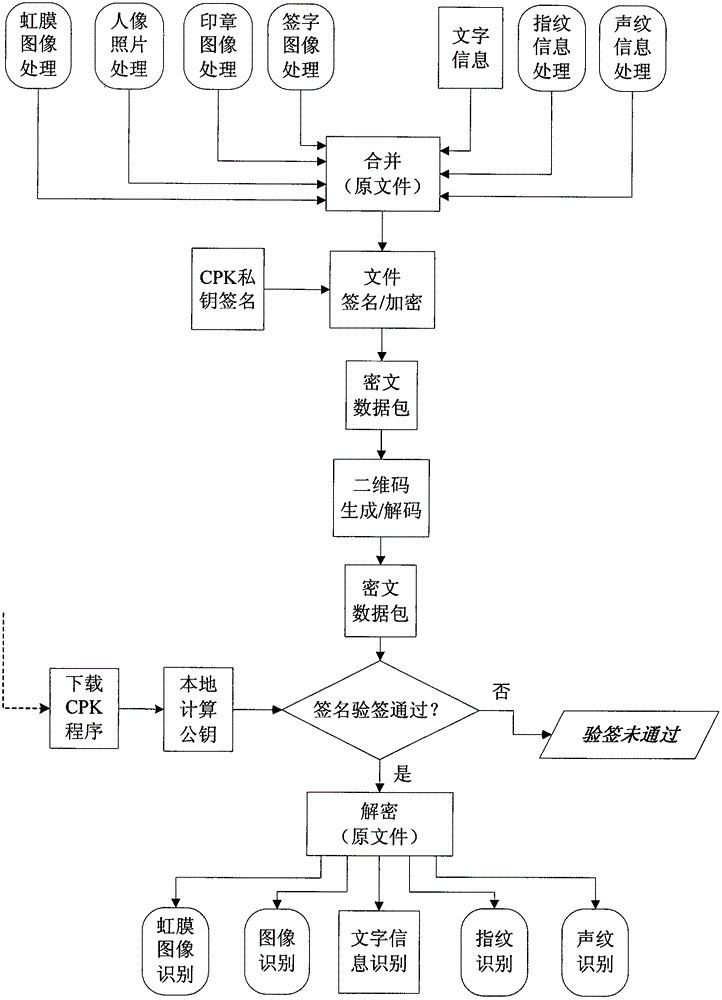
[0046] Example 2: see image 3 , the identity information of the certificate in this embodiment includes not only portrait photos and text information, but also other images and biological information. Other images are stamp images and signature images, and the biological information includes human iris images, voice recording voiceprints, and fingerprints. .
[0047] Specific steps are as follows:
[0048] Step 1, certificate information input: Compress portrait photos, stamp images, and signature images respectively to generate compressed image files, merge image files and other certificate issuance information into a certified plaintext original file, and collect other certificate issuance information Proceed according to the corresponding technical method at the certificate issuing end;
[0049] Step 2, encryption and two-dimensional code generation: use the CPK private key based on identity authentication to digitally sign the original document of the certified plaintex...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com