P2P (peer to peer) worm detection method and device
A P2P network and worm technology, applied in the Internet field, can solve the problems that the traffic does not pass through the firewall, P2P worms are difficult to distinguish, and the firewall cannot be identified, so as to achieve the effect of defending against known P2P worms and improving security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
no. 1 example
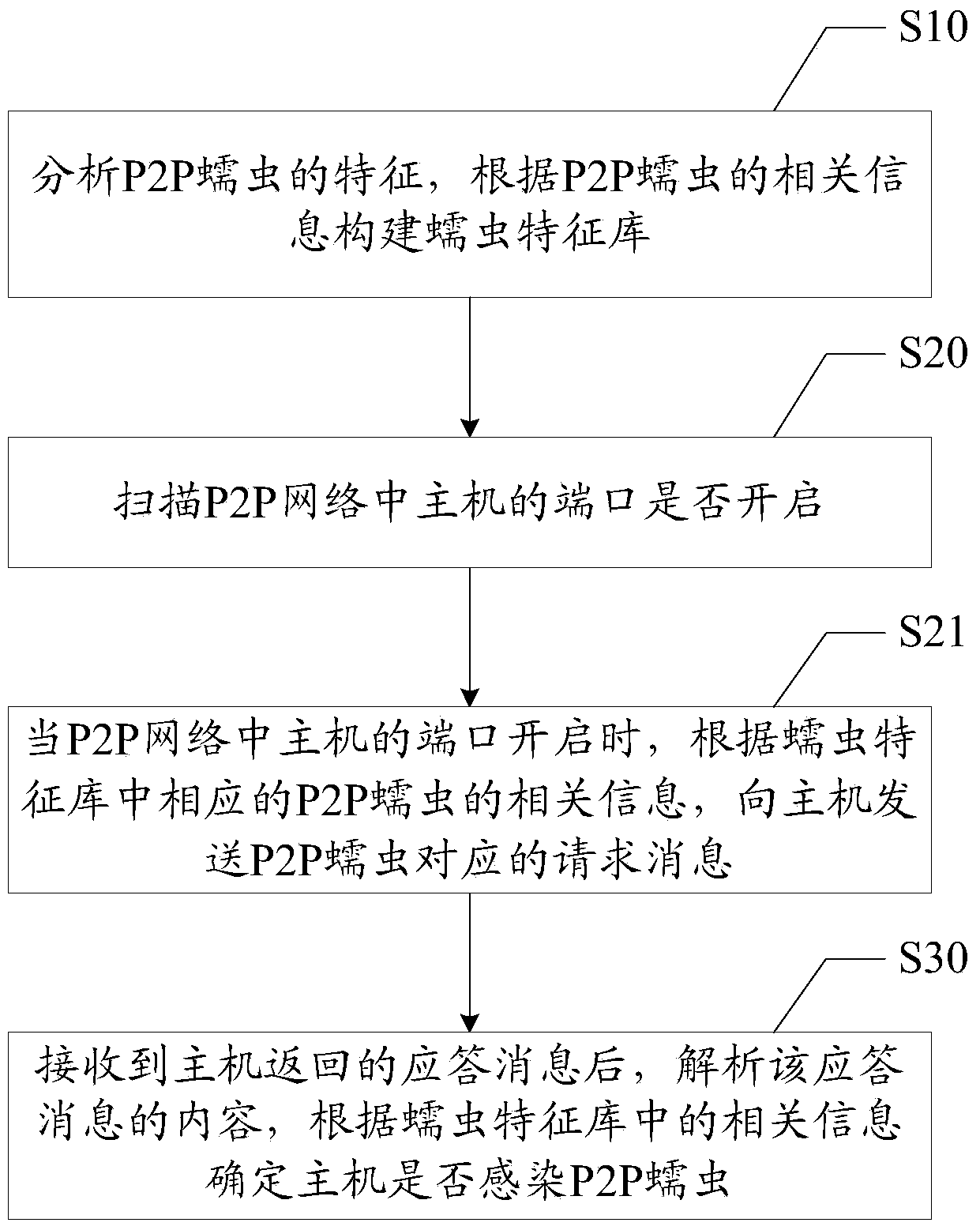
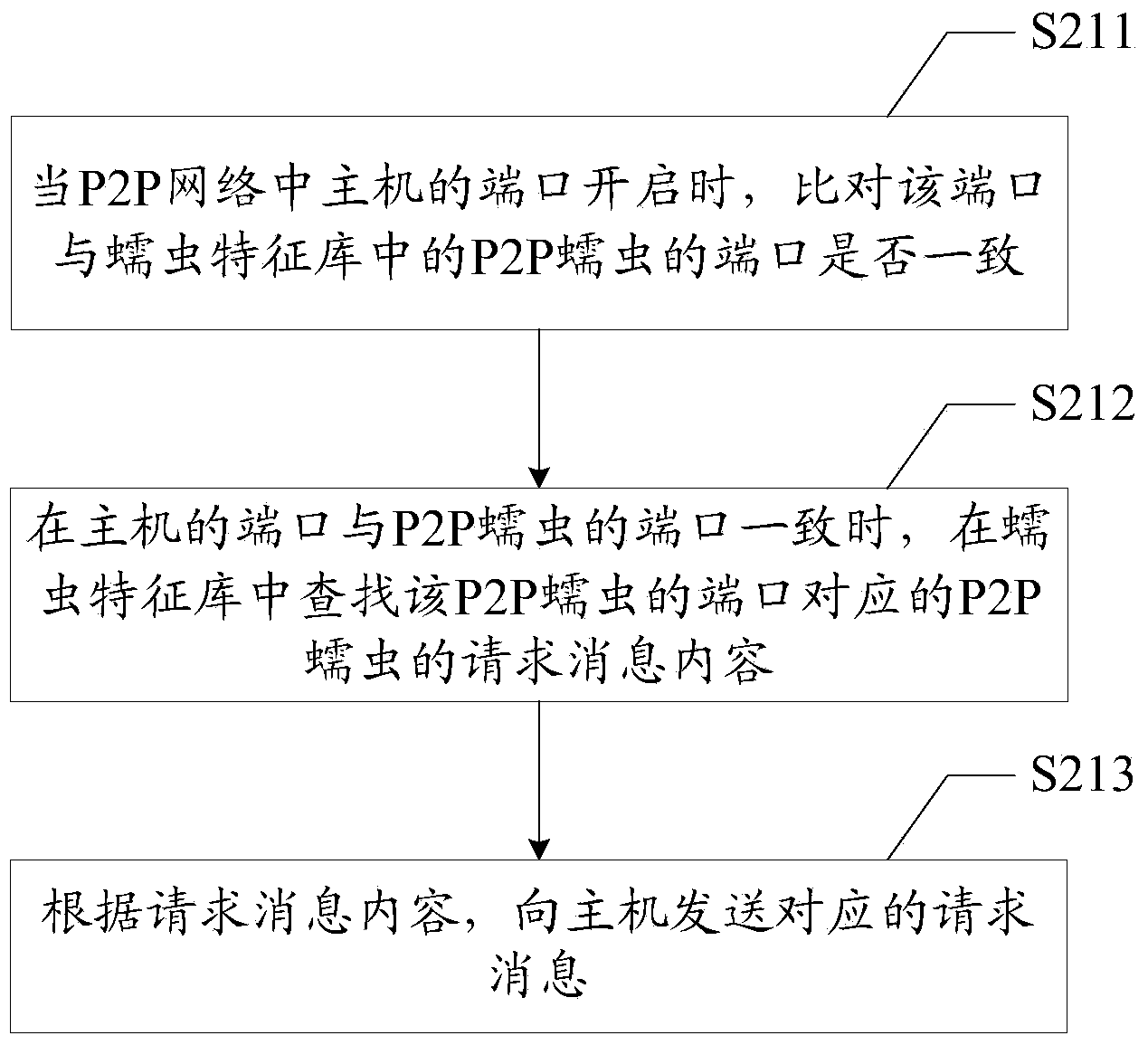
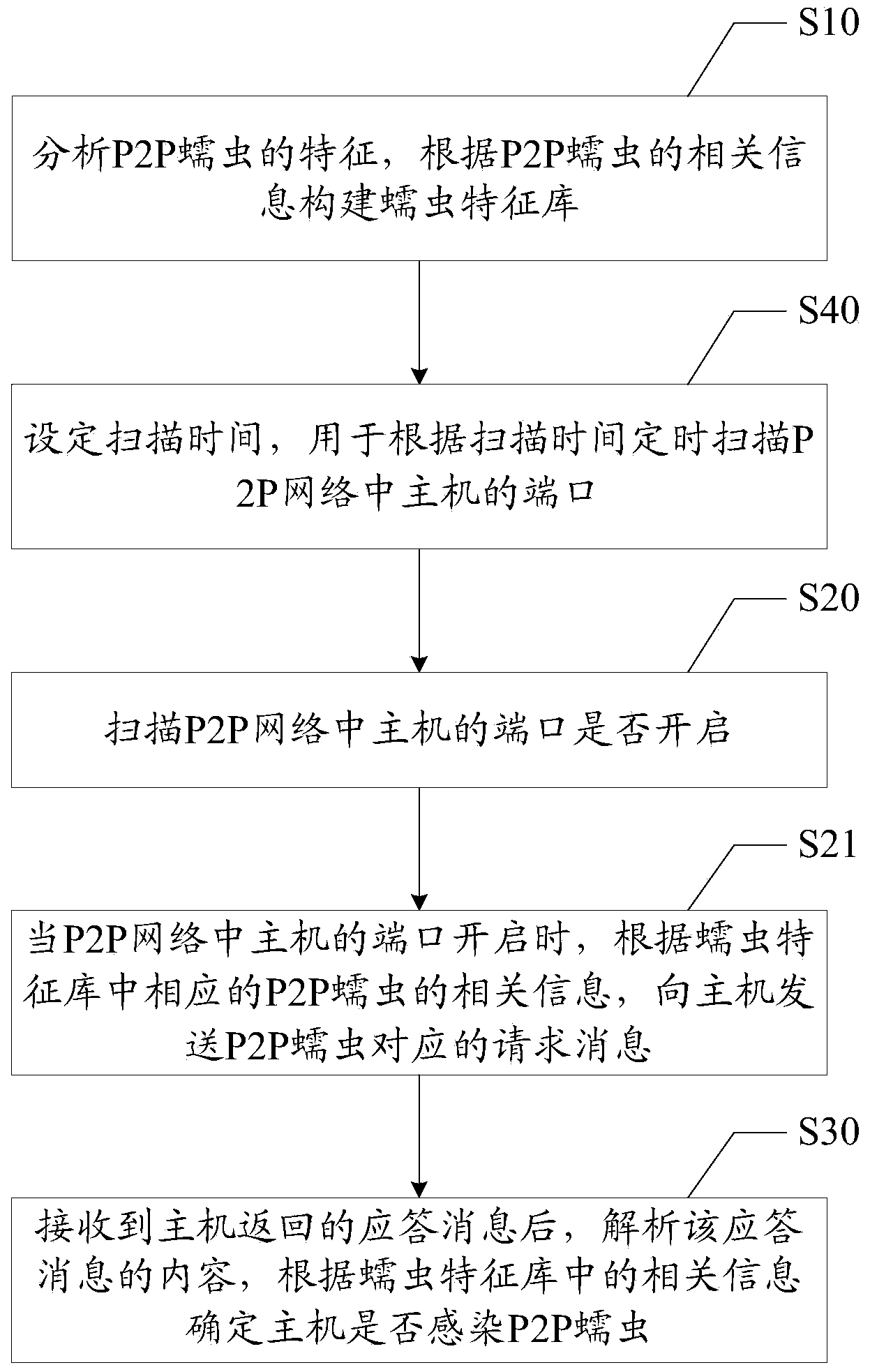
[0092]Based on the first embodiment of the device for P2P worm detection of the present invention, the device also includes:
[0093] The setting module 40 is used to set the scanning time, and is used to regularly scan the ports of the hosts in the P2P network according to the scanning time.
[0094] In this embodiment, before using the firewall to scan the port of the host, the scanning time is set by the setting module 40, so that the firewall regularly scans the port of the host in the P2P network according to the scanning time. The scan time is the interval time for the firewall to regularly scan the host ports, that is, the length of time for each scan interval, and the firewall is used to scan the hosts in the specified network segment in the P2P network once.
[0095] Before using the firewall to scan the ports of the host, set the scan time so that the firewall scans the hosts in the specified network segment in the P2P network once per scan time interval, which furth...
no. 2 example
[0097] Based on the first and second embodiments of the device for P2P worm detection of the present invention, the device also includes:
[0098] The isolation and alarm module 50 is configured to isolate the host and give an alarm when it is determined that the host is infected with P2P worms.
[0099] When receiving the response message of the host, and after the content of the response message is parsed, it matches with the content of the response message of the corresponding P2P worm in the worm database, so that after determining that the host is infected with the P2P worm, the isolation and alarm module 50 will check the host. Carry out isolation and alarm to prevent the host from quickly spreading P2P worms to other hosts through the security holes of other hosts in the P2P network, P2P network file sharing function, resource sharing, etc., thereby causing security threats.
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com