Data protection method, device and system for iBeacon base station
A data protection and base station technology, applied in the field of communication, can solve the problems of fraudulent use of iBeacon data, and achieve the effect of protecting interests, reducing the risk of fraudulent use, and improving security.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
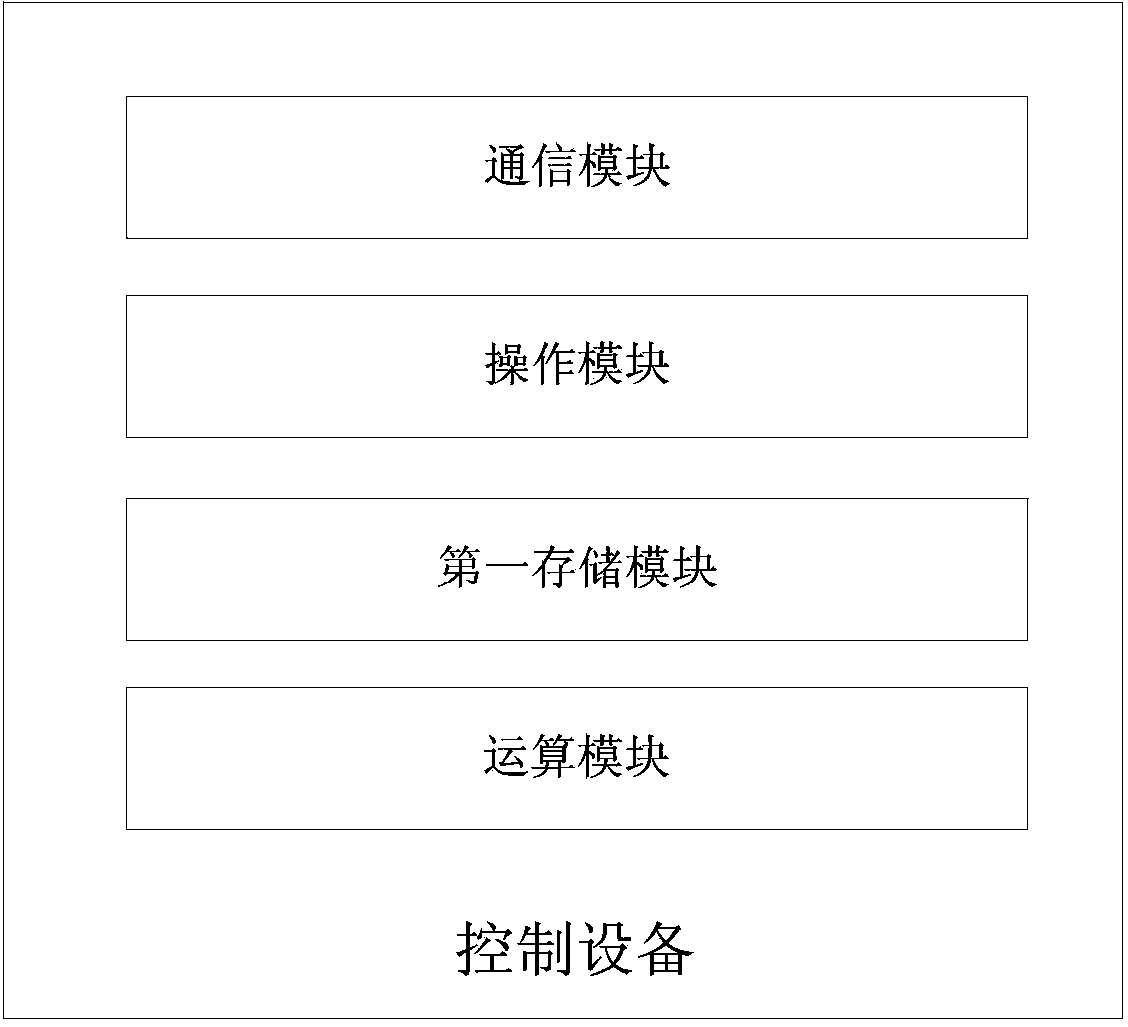
[0057] The application scenario of this embodiment assumes that 10 iBeacon devices are deployed at different locations in a large store, and the store store map drawn according to the real scene inside the store is stored in the server. Coordinate ID. The corresponding relationship between the position information of the iBeacon base station in the map and the identification information of the iBeacon base station (such as UUID, MajorID, MinorID and other identification information of the iBeacon base station) is stored in the mapping table.
[0058] The corresponding relationship stored in the mapping table is not limited thereto. In other embodiments, the mapping table may also store the corresponding relationship between the location coordinates of the iBeacon base station, the unique identifier of the iBeacon base station, and the identification information of the iBeacon base station.
[0059] In this embodiment, the iBeacon base station has a built-in Bluetooth 4.0 chip,...
Embodiment 2
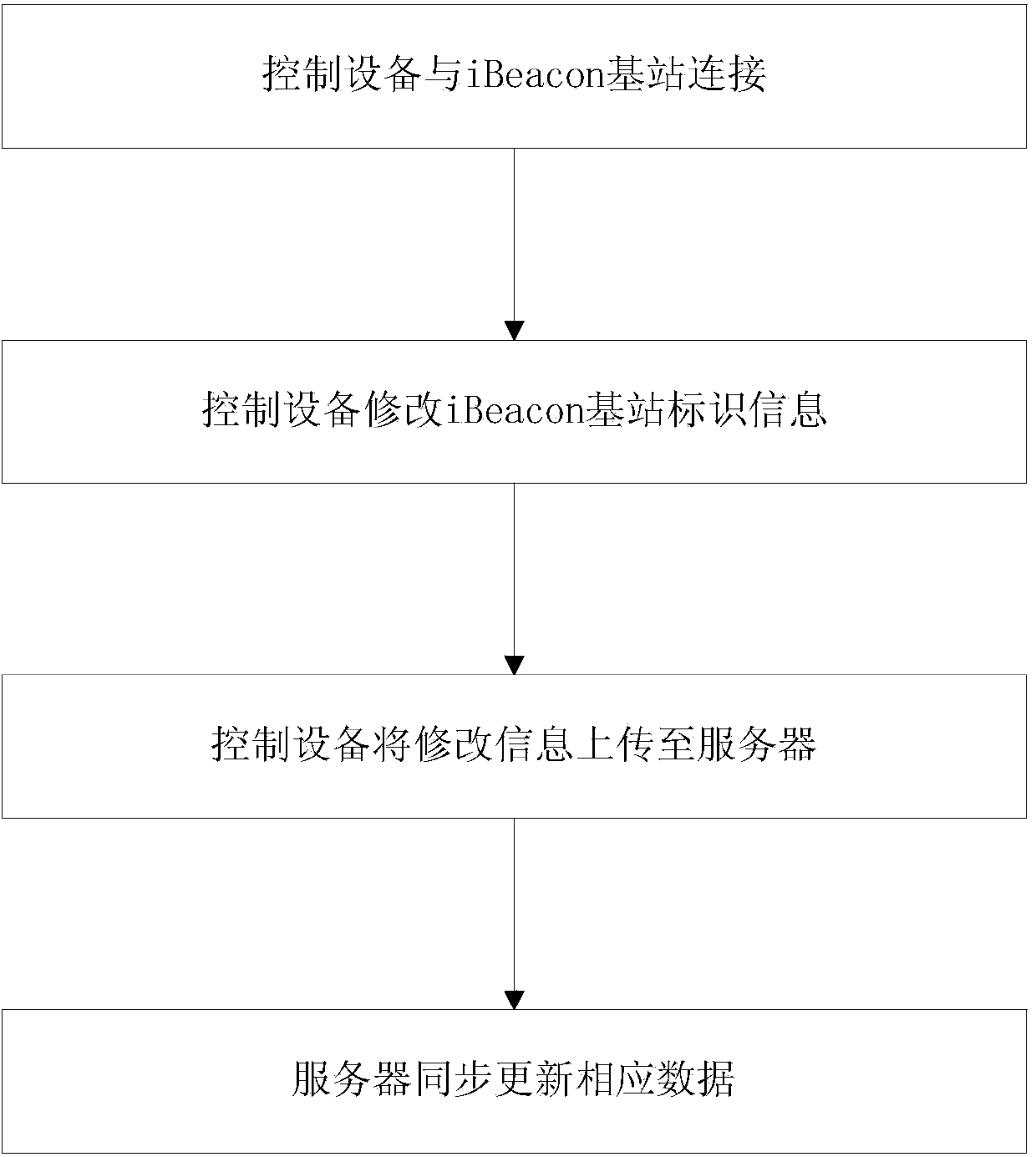
[0073] The difference between this embodiment and Embodiment 1 is that the mobile phone actively connects to the iBeacon base station and modifies the identification information of the iBeacon base station. After the modification is completed, the modified information is uploaded to the server, and the server performs synchronous update.
[0074] Such as figure 1 As shown, the method for protecting iBeacon base station data described in this embodiment, the specific steps include:
[0075] 1. The mobile phone actively connects to the iBeacon base station wirelessly through Bluetooth;
[0076] The mobile APP can automatically or manually connect to the iBeacon base station on a regular or irregular basis.
[0077] 2. The mobile APP modifies the identification information of the iBeacon base station;
[0078] The mobile phone APP can read the stored update information from within the APP, or actively request the update information from the server, or automatically generate the...
Embodiment 3
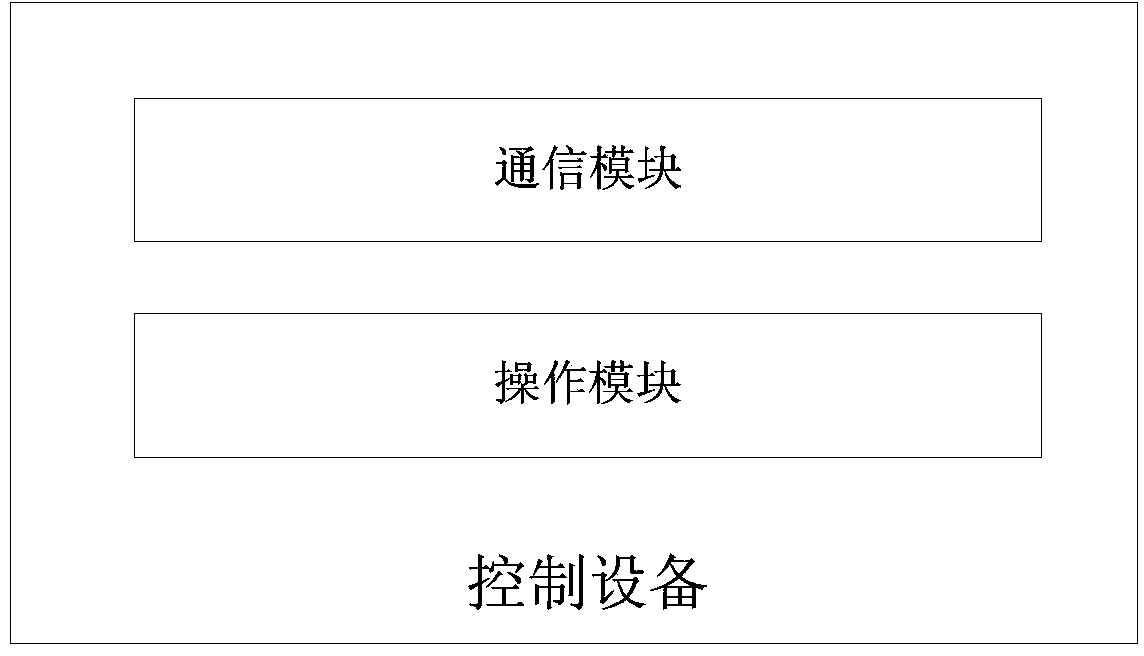
[0087] The difference between this embodiment and Embodiment 1 is that the control device in this embodiment is a PC computer, and the PC computer has control software for controlling the iBeacon base station, and the iBeacon base station is electrically connected to the PC computer through a USB interface, a serial port or other physical interfaces. The specific steps of the iBeacon base station data protection method in the present embodiment include:
[0088] 1. The iBeacon base station is electrically connected to the PC computer through the interface;
[0089] 2. Modify the identification information of the iBeacon base station through the control software in the PC computer;
[0090] 3. After the modification is completed, the PC computer sends the modification information to the server;
[0091] 4. The server receives the modification information, and updates the corresponding identification information in the mapping table storing the correspondence between the locati...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - Generate Ideas
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com