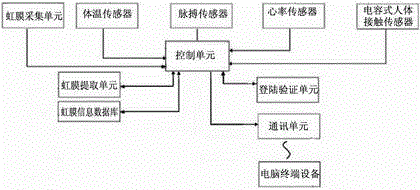
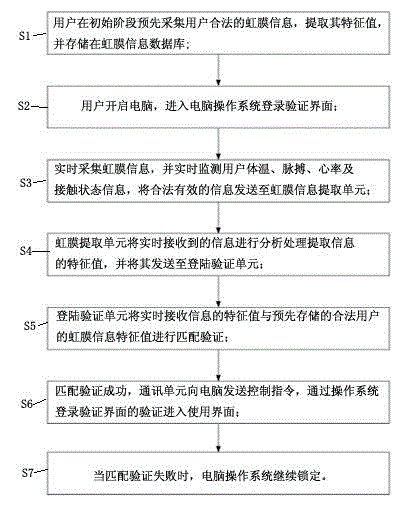
Computer login verification system and method based on iris recognition technology
A login verification and iris recognition technology, which is applied in the field of login verification of the operating system, can solve problems such as easy cracking, impact, and hidden dangers of data security, and achieve the effect of ensuring legal validity, ensuring security, and improving security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0021] Before any embodiment of the present invention is described in detail, it should be understood that the application of the present invention is not limited to the details of the structure and the installation and connection of components, etc. shown in the following description or drawings. The invention is capable of other embodiments and of being practiced or of being carried out in various ways. At the same time, it should be understood that the specific terms and terms used herein to describe the principles and features of the present invention should not be regarded as limiting. As used herein, "comprising", "comprising" and its variants mean including the items listed below and their equivalents and additional items; the term "connected" and its variants are used broadly, including but not limited to directly One or more of the connection methods such as connection, induction or coupling, etc. in an indirect or indirect manner, in addition, "connection" or "coupli...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com