A verification method for e-commerce account based on cloud security
An e-commerce and verification method technology, applied in the Internet field, can solve problems such as occupying website server resources, slowing down website response speed, and user account theft, etc., to improve security, ensure legal validity, and prevent login attacks. Effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
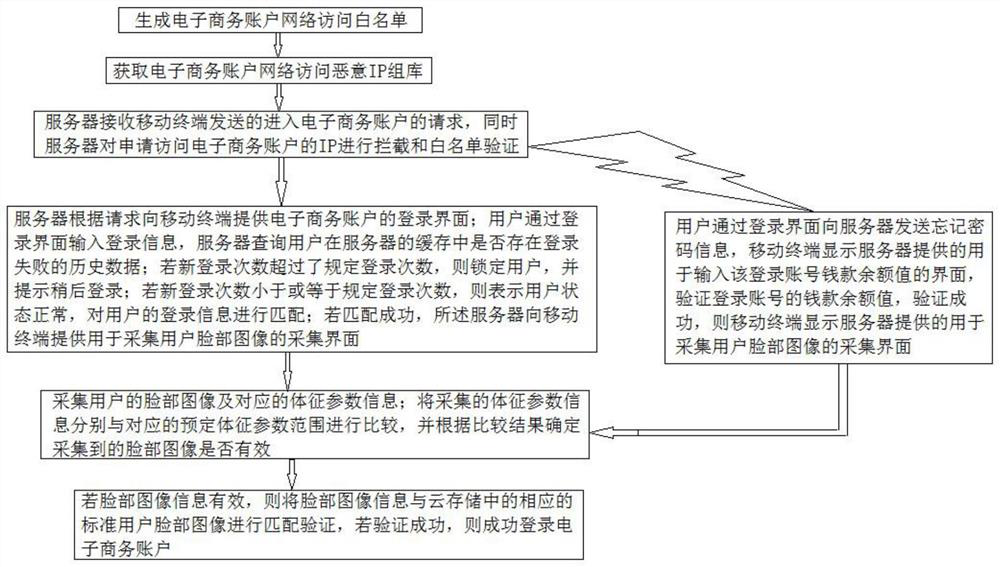
[0051] Such as figure 1 As shown, a method for verifying an e-commerce account based on cloud security includes the following steps:
[0052] Step 1: Generate an e-commerce account network access white list; according to the specific environment of the e-commerce account login, set the network IP that is allowed to access the e-commerce account and its access rights, and generate a unique network access white list for the e-commerce account. list;
[0053] Step 2: Obtain the network access malicious IP group library of e-commerce accounts; analyze the time, space characteristics and maliciousness of the existing network access IPs of e-commerce accounts, and finally generate the malicious IP group library;
[0054] Step 3: The server receives the request to enter the e-commerce account sent by the mobile terminal, and at the same time, the server intercepts and whitelists the IP that applies to access the e-commerce account; the specific steps are as follows:
[0055] S31: W...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com