Security SBOX realization method and apparatus
An implementation method and security technology, applied in the direction of encryption device with shift register/memory, etc., can solve problems such as high cost, and achieve the effect of simplifying combinational logic circuits
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0029] In order to make the above objects, features and advantages of the present invention more comprehensible, specific embodiments of the present invention will be described in detail below in conjunction with the accompanying drawings.
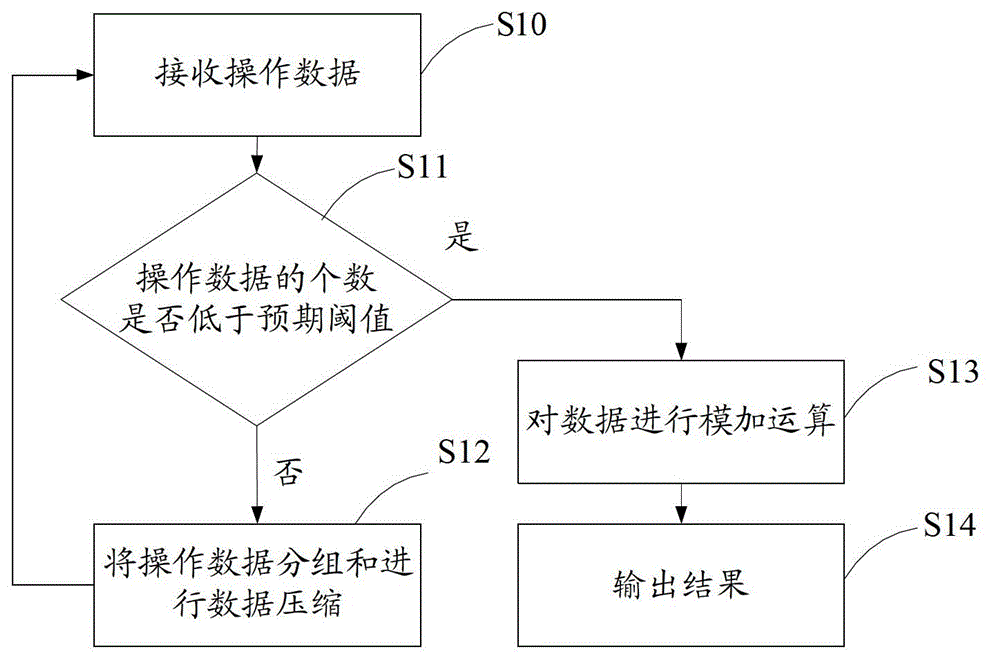
[0030] figure 1 It is a flow chart of the implementation method of the security SBOX in the embodiment of the present invention. like figure 1 As shown, the method includes steps S101-S105.
[0031] First, step S101 is executed to calculate the security SBOX according to the initial SBOX, and the calculation function of the number whose ordinal number is i in the security SBOX is about the ordinal number i, the input variable A and the output variable F of the initial SBOX ( The first function G(i, A, F(A)) of A). Taking the DES encryption algorithm as an example, the initial SBOX of the general DES encryption algorithm is 8. The 8 security SBOXs corresponding to the 8 initial SBOXs may be calculated one by one according to the first f...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com