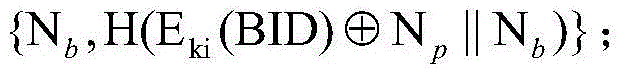Method of implementing binding and authentication of intelligent bracelet and intelligent mobile terminal
A technology for smart mobile terminals and smart bracelets, applied in user identity/authority verification, electrical components, transmission systems, etc., can solve the problems of binding and authentication methods between smart bracelets and smart mobile terminals, and achieve performance impact. Low, improve ease of use, and achieve the effect of secure binding
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
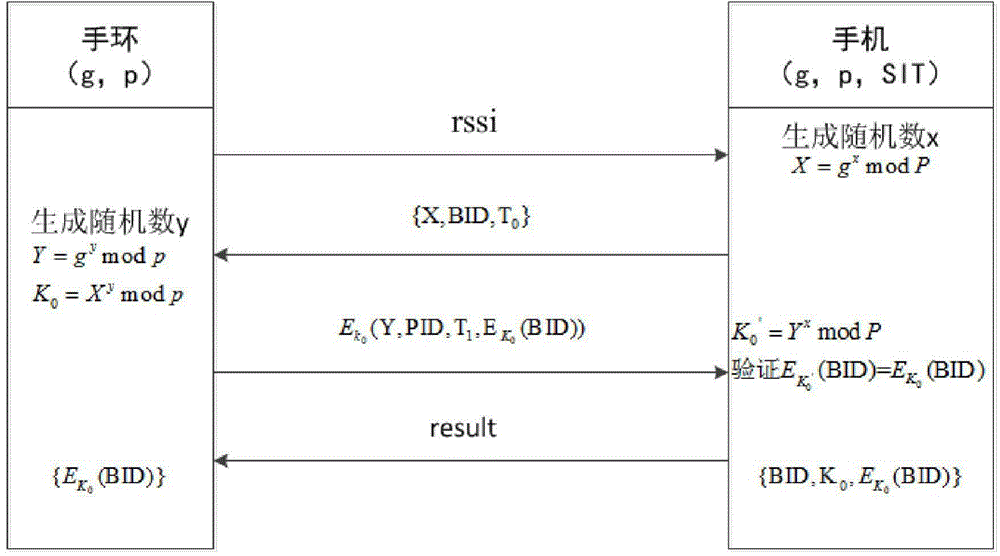
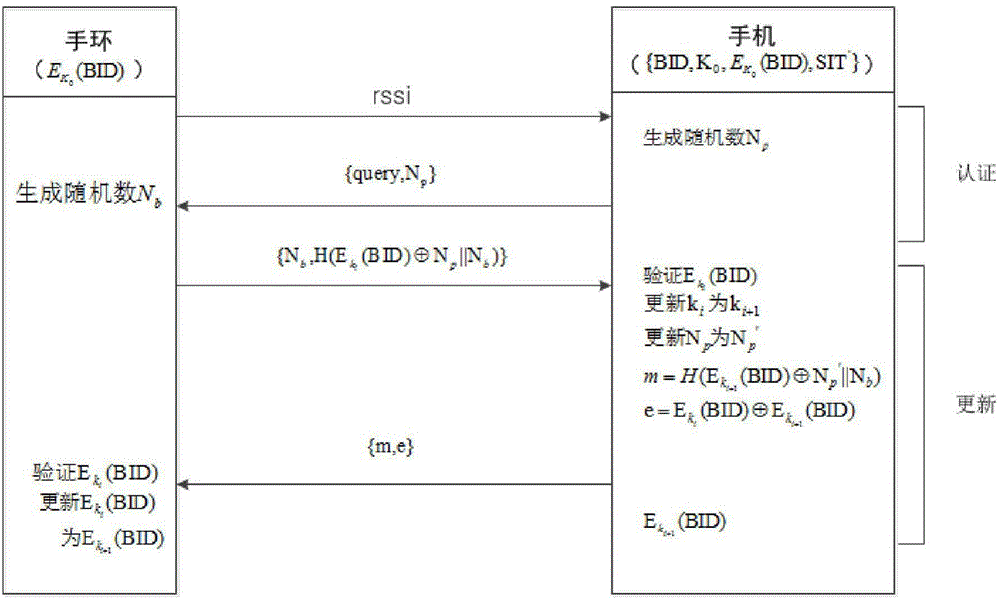
[0030] The present invention aims to propose a method for realizing the binding and authentication of smart bracelets and smart mobile terminals, so as to realize secure binding and pairing between smart bracelets and smart mobile terminals, and to realize access control to smart mobile terminals by using smart bracelets .
[0031] Below in conjunction with accompanying drawing and embodiment the scheme of the present invention will be further described:
[0032] The present invention improves the Diffie-Hellman protocol in the initialization process, adding timestamp authentication and combining the bracelet MAC address and the IMEI number of the smart mobile terminal for identity authentication, and in the initialization process, we consider the security of the channel, through Judging the Bluetooth signal strength rssi of the bracelet to limit the distance between the smart mobile terminal and the bracelet initialization, which can be controlled within the set distance thre...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com