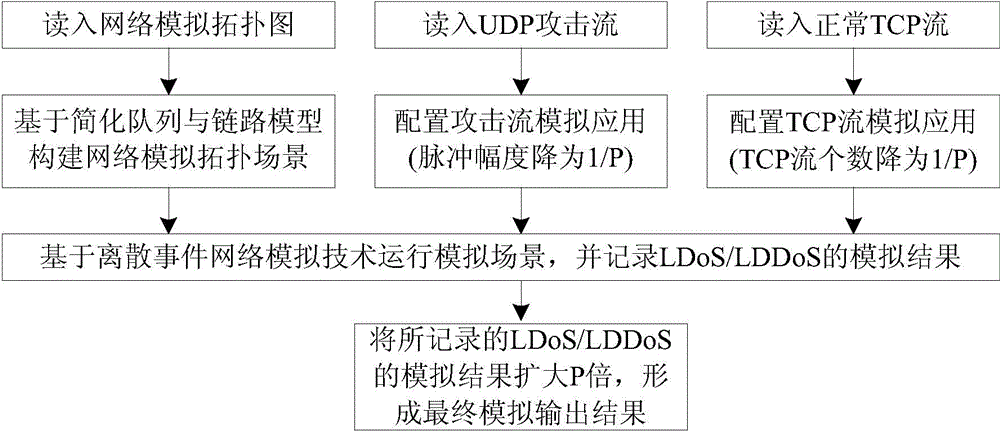
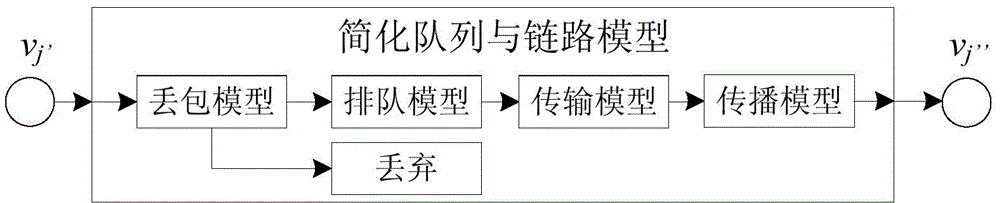
Simulation method oriented to LDoS (Low-rate Denial of Service) and LDDoS (Low-rate Distributed Denial of Service)
A simulation method and network simulation technology, applied in digital transmission systems, electrical components, transmission systems, etc., can solve the problems of high computational overhead, low simulation running time, and reduce LDoS and LDDoS simulation, and achieve the effect of reducing computational overhead.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
[0055] Embodiment 1 LDoS attack
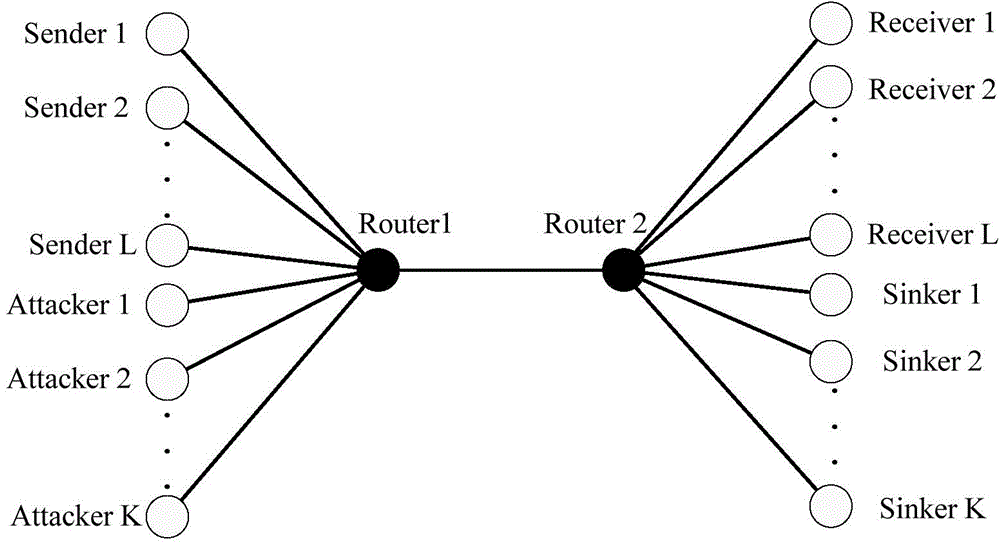
[0056] In this instance, based on image 3 , setting K=1 indicates that there is only one attack source, which is an LDoS attack; L=10 indicates that there are 10 normal TCP flows. By comparing the simulation results of the TCP arrival traffic rate obtained by this method with the results obtained by the traditional method (traditional discrete event simulation technology), the simulation authenticity of this method is verified, such as Figure 4 shown. In this embodiment, the simulation time is 1000 seconds, and the attack time period is between 200-800 seconds. It can be found that the simulation results obtained by this method are basically consistent with those obtained by the traditional method, indicating that this method can guarantee the authenticity of the LDoS simulation results. Table 1 compares the average TCP arrival traffic rate of the two methods under the condition of LDoS attack and without LDoS attack. It can be seen that ...
Embodiment 2
[0062] Embodiment 2 LDDoS attack
[0063] In this instance, based on image 3 , set K=5, indicating that there are multiple attack sources, which is an LDDoS attack; L=10, indicating that there are 10 normal TCP flows. By comparing the simulation results of the TCP arrival traffic rate obtained by this method with the results obtained by the traditional method (traditional discrete event simulation technology), the simulation authenticity of this method is verified, such as Figure 5 shown. In this embodiment, the simulation time is 1000 seconds, and the attack time period is between 200-800 seconds. It can be found that the simulation results obtained by this method are basically consistent with those obtained by the traditional method, indicating that this method can guarantee the authenticity of the LDDoS simulation results. Table 3 compares the average TCP arrival traffic rate of the two methods under the condition of LDDoS attack and without LDDoS attack. It can be see...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com