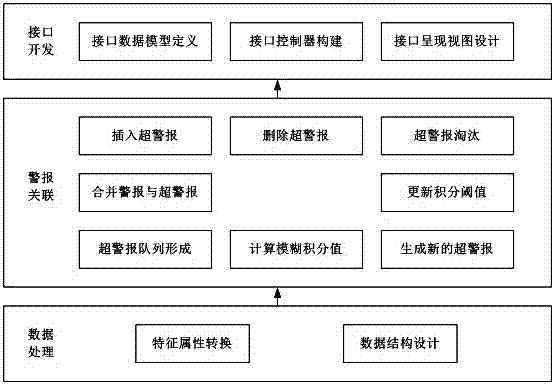
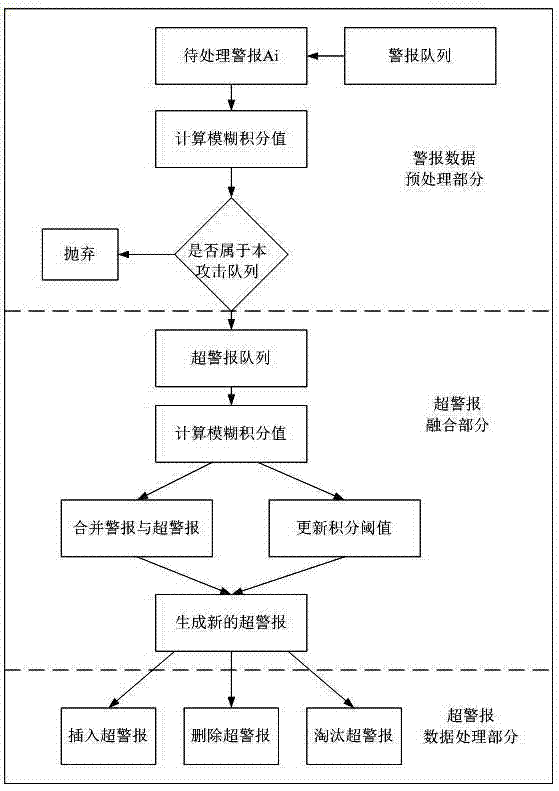
Multi-step attack alarm associated network service interface development method
A service interface and associated network technology, applied in transmission systems, electrical components, etc., can solve problems such as network attacks that are difficult to deal with, and achieve the effect of solving large amounts of data
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment
[0136] 1. LLDOS1.0 attack
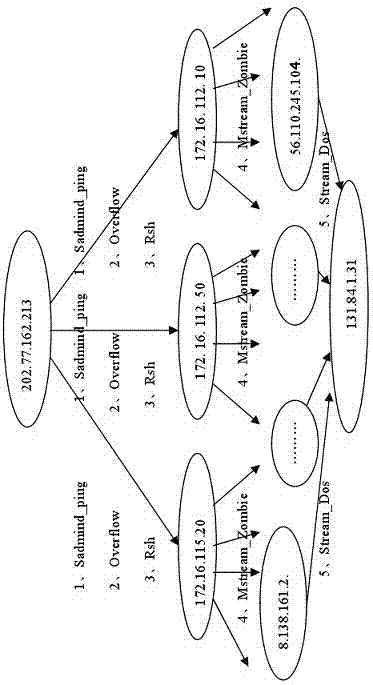
[0137] The present invention uses the LLDOS1.0 attack data in the DARPA2000 data set widely used in the security field as the experimental data to describe the specific implementation of the present invention. The time of this data set is from 09:25 to 12:35 on March 7, 2000, and a total of 33,907 alarms were generated, of which 33,786 alarms were related to LLDOS1.0 attacks. The attack process is as attached image 3 shown.
[0138] 2. The home page of the alarm correlation system is attached Figure 4 As shown, the file upload page is as attached Figure 5 shown.
[0139] 3. After the LLDOS1.0 alarm correlation, the relationship between the total number of alarm input, super-alarm training, and the number of super-alarm-related alarms. The results are attached Image 6 shown.
[0140] 4. The statistical results of the above correlation results are shown in Table 5.
[0141] Table 5 LLDOS1.0 alarm, super-alarm training, and the relationship...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com