Tamper detection method for text documents in cloud storage environment
A text document and document technology, applied in the fields of digital data protection, electronic digital data processing, program/content distribution protection, etc., can solve the problems of large visual impact, small capacity of watermark information carried by carrier files, and poor robustness, etc. Achieve the effect of covering a large amount of information, being easily tampered with, and ensuring security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment approach 1
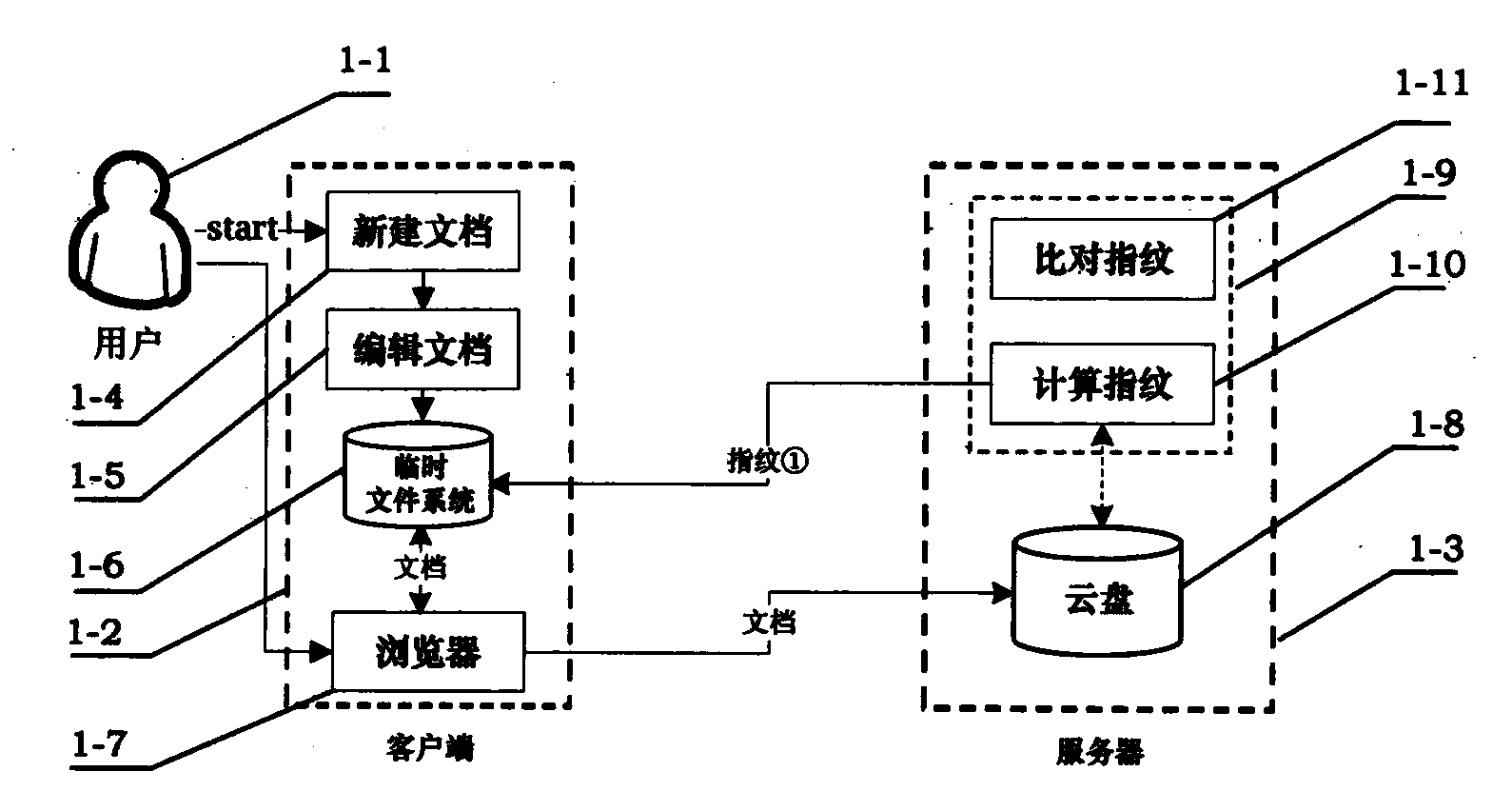
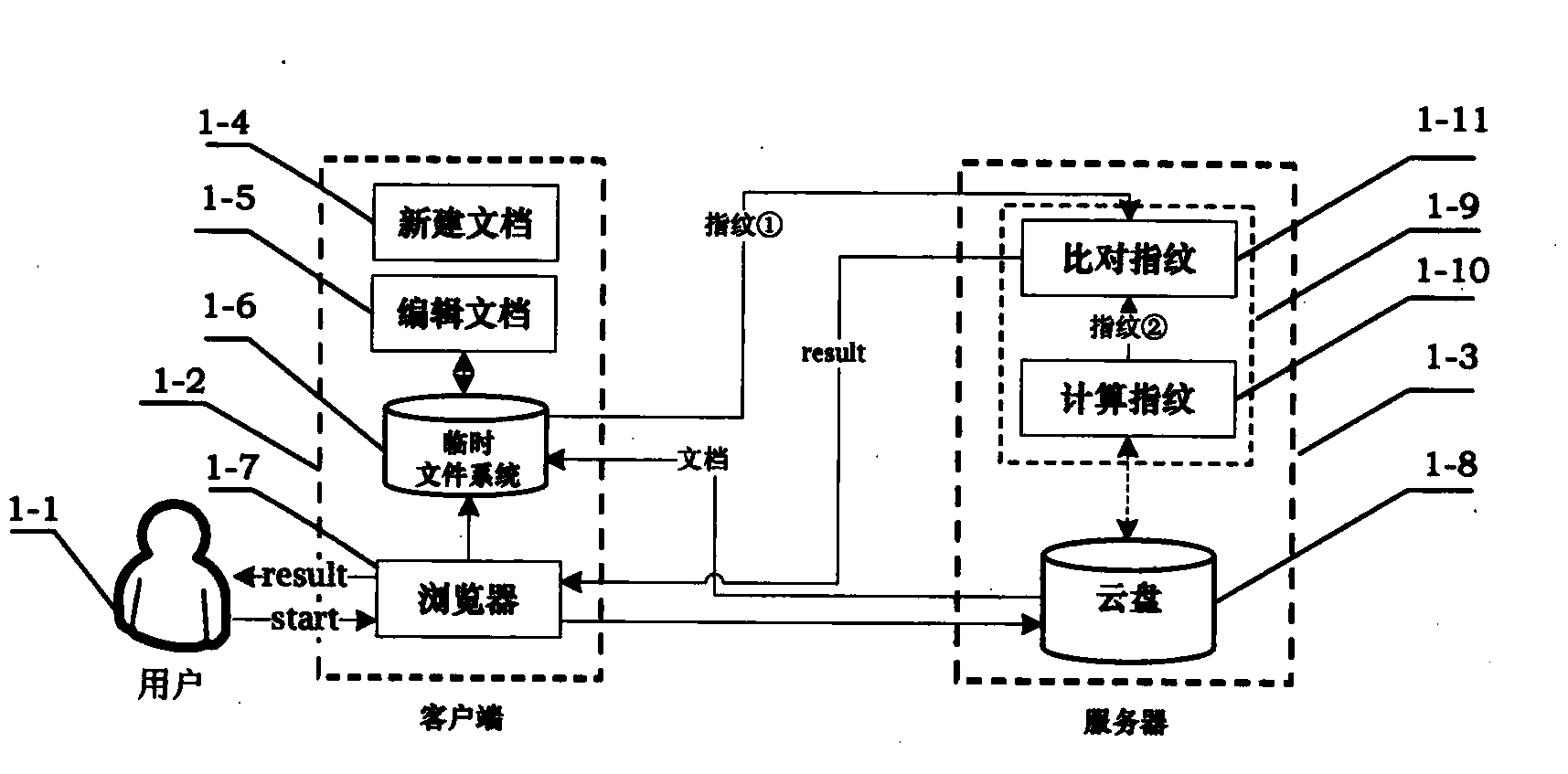
[0053] Embodiment 1: Fig. 1 is the architectural diagram of the tampering detection method used on the server side, which includes two sub-graphs, Figure 1a and Figure 1b . in, Figure 1a is an architectural diagram of the tamper detection method used when a user stores a document on the server side, Figure 1b is an architectural diagram of a tamper detection method used when a user reads a document from the server side.
[0054] Referring to Fig. 1, this solution includes three entities: user 1-1, client 1-2, and server 1-3. User 1-1 can implement the following operations on client 1-2: create new document 1-4, edit document 1-5, temporarily save the document and fingerprint in temporary file system 1-6, and access the server through browser 1-7 1-3. Specifically, the browser 1-7 is the medium through which the user 1-1 accesses the server 1-3 at the client 1-2. In addition to providing the user with an auxiliary storage space, that is, a cloud disk 1-8, the server 1-3...
Embodiment approach 2
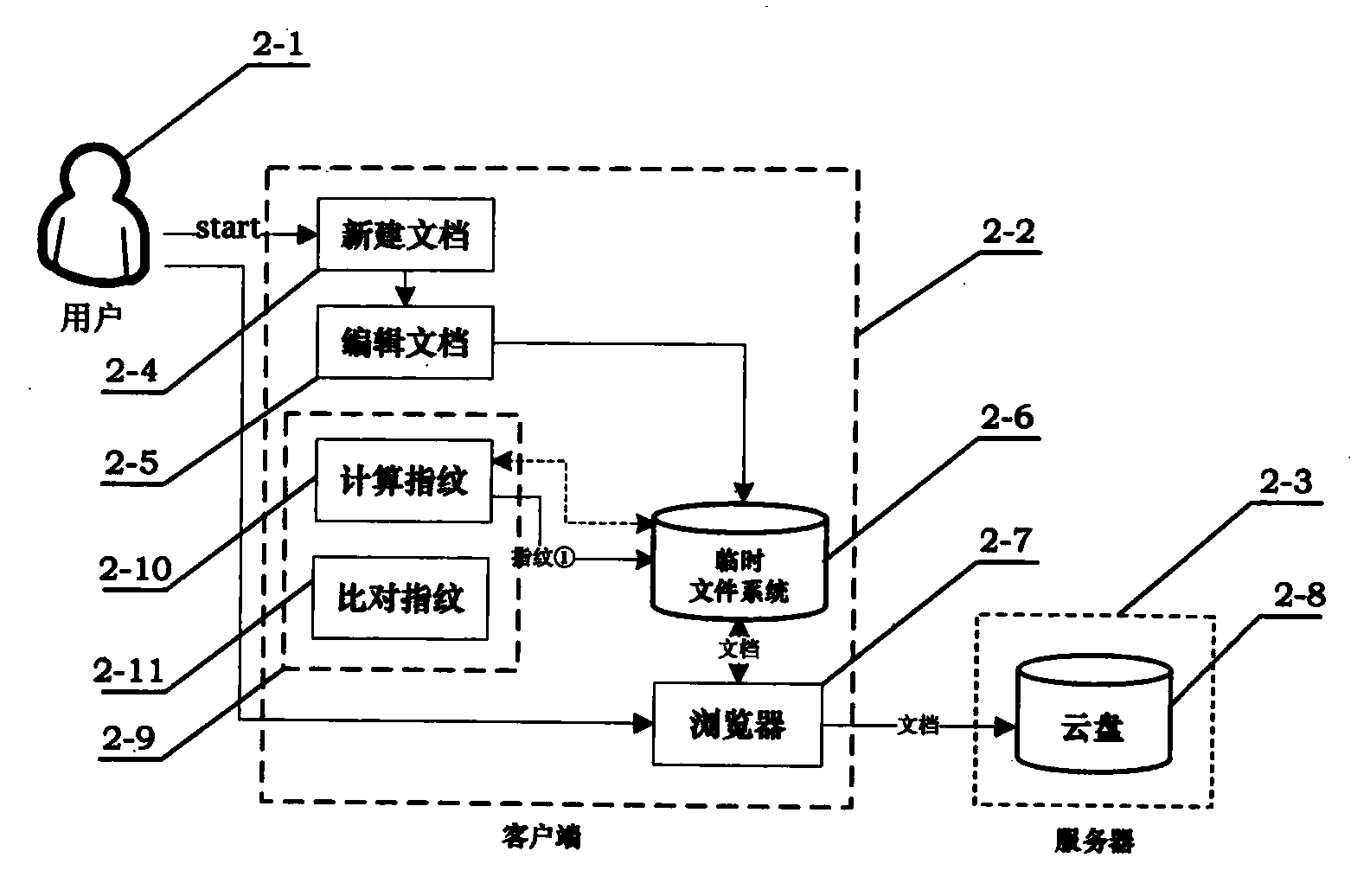
[0058] Embodiment 2: Fig. 2 is the architectural diagram of the tamper detection method used by the client, which includes 2 sub-graphs, Figure 2a and Figure 2b . in, Figure 2a is an architectural diagram of the tamper detection method used when a user stores a document, Figure 2b is an architectural diagram of a tamper detection method used when a document is read by a user.
[0059] Referring to Fig. 2, this solution also includes three entities: user 2-1, client 2-2, and server 2-3. The user 2-1 can implement the following operations on the client 2-2: create a new document 2-4, edit a document 2-5, store documents and fingerprint files in the temporary file system 2-6, and access the server 2 through the browser 2-7 -3, using the tamper detection method 2-9 to calculate the fingerprint module 2-10 and compare the fingerprint module 2-11. The server 2-3 provides the user with an auxiliary storage space, that is, a cloud disk 2-8.
[0060] The specific implementati...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com