Encryption-resistant watermarking
A technology of watermarking and ciphertext, applied in the field of encoding information into data content, can solve the problems of copying and distribution of media content, not allowing users to distribute copies of programs, and restrictions
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
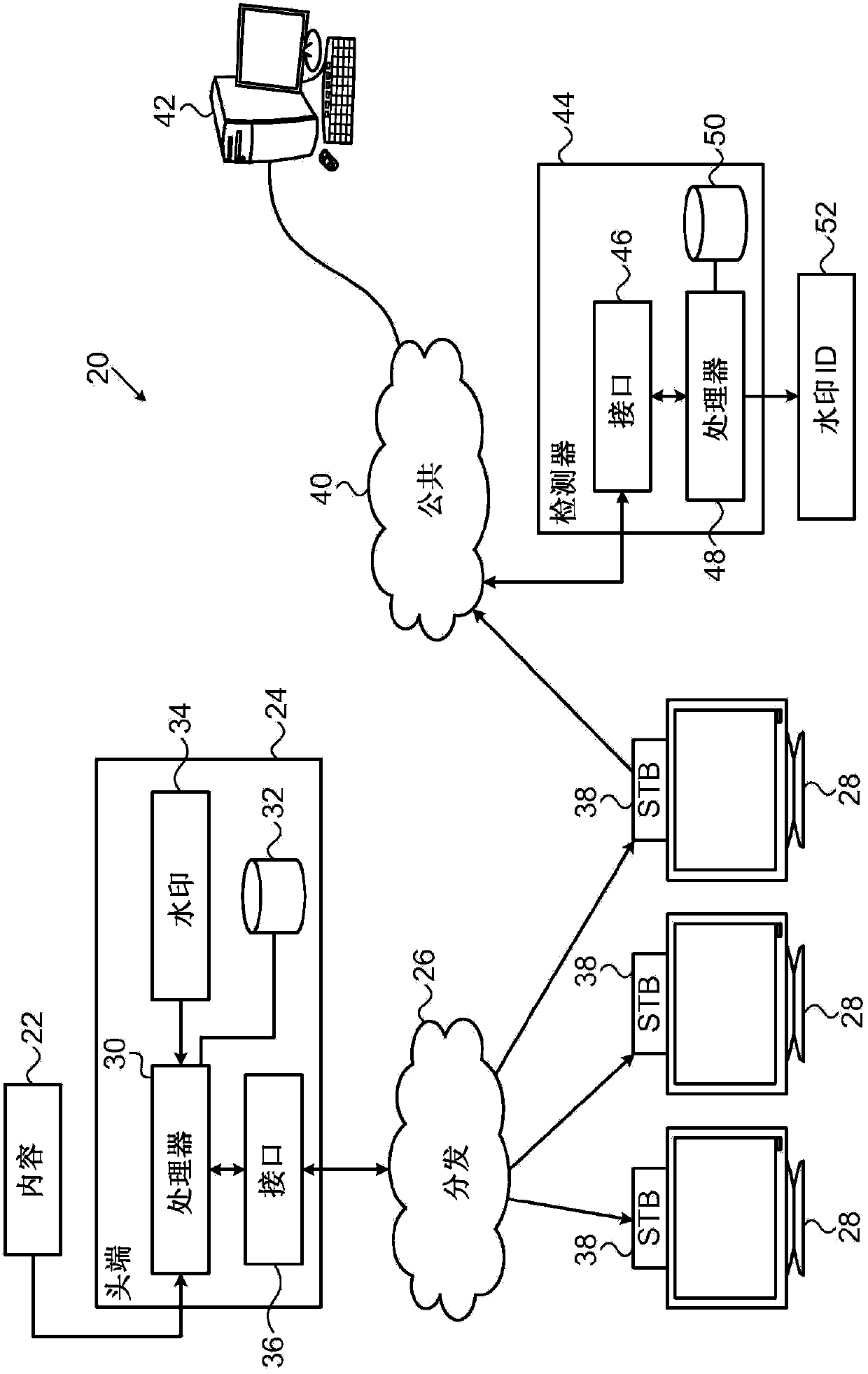
[0022] overview
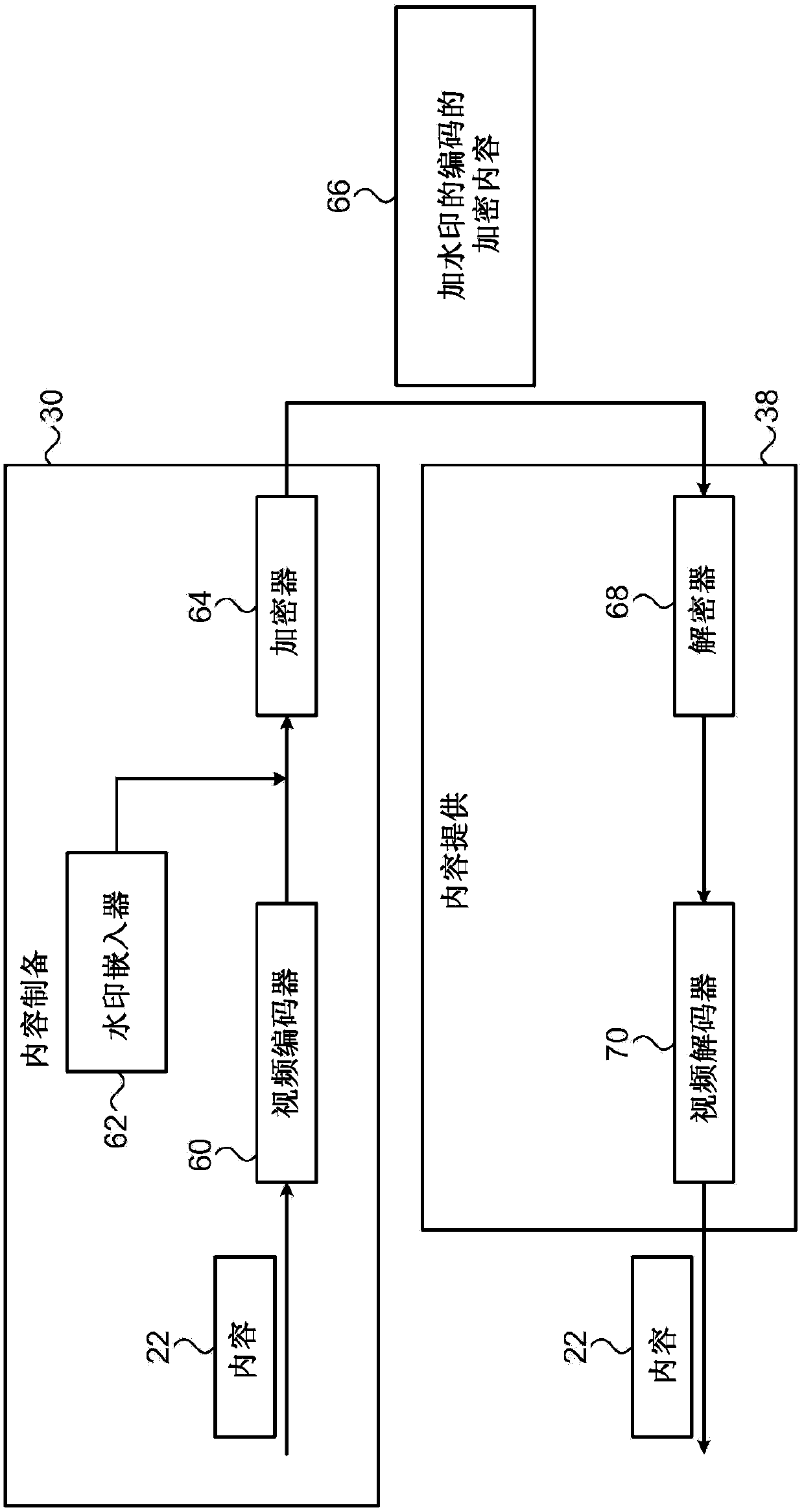
[0023] After applying watermarks to digital content items, content publishers may then wish to inspect traffic in order to detect these watermarks, thereby identifying unauthorized copies of the content item and the source of these copies. Typically, however, communication traffic is encrypted and it becomes difficult or impossible to detect watermarks without first decrypting the traffic. However, content distributors may not be able to obtain the required decryption keys.
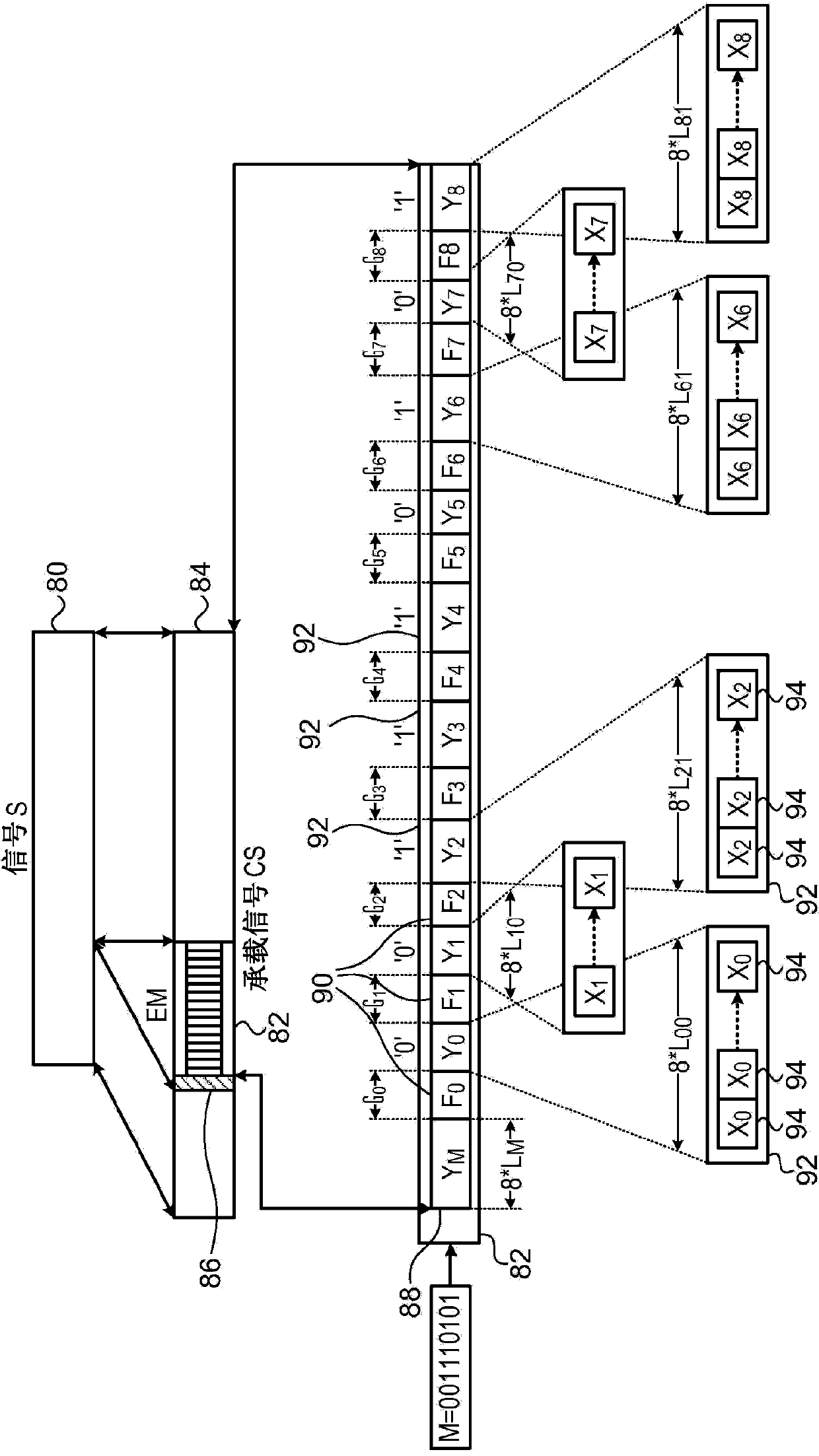
[0024] Embodiments of the invention described below can be used to address this difficulty by providing digital watermarks that can be detected even in encrypted data, especially when certain types of blockciphers are used for encryption. For example, when the electronic codebook (ECB) mode of block cipher encryption is used, each plaintext block is encrypted into a corresponding ciphertext block of the same size. In the embodiments described below, the watermark is encoded using a rep...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com