Inter-cloud-storage-system data migration encryption method
An encryption method and data technology, applied in transmission systems, electrical components, etc., can solve problems such as data paralysis, increased costs, and data confusion, and achieve the effect of improving efficiency and ensuring communication security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
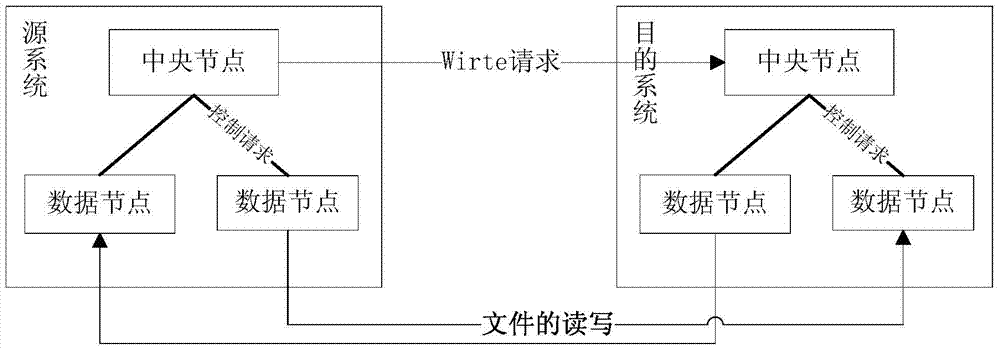
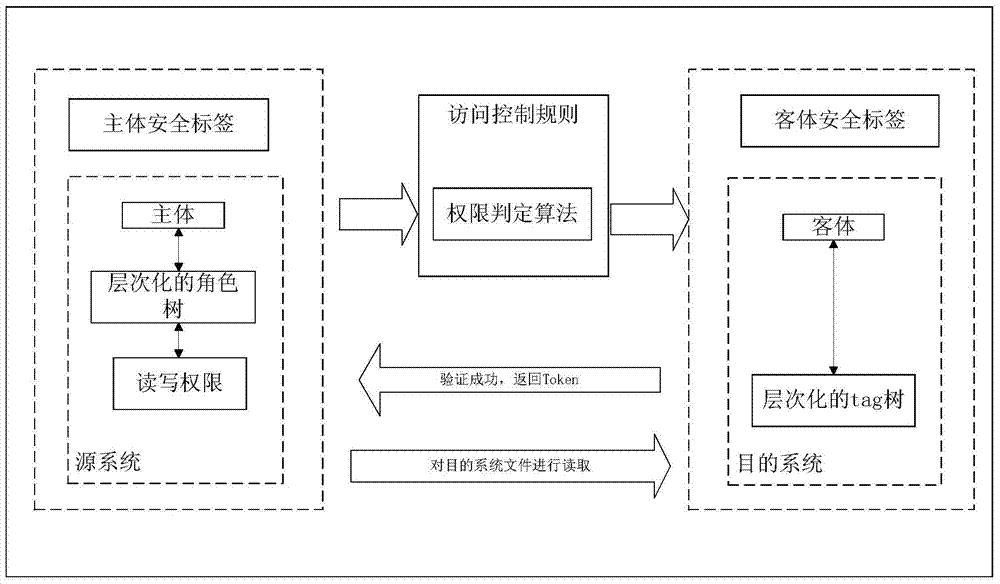
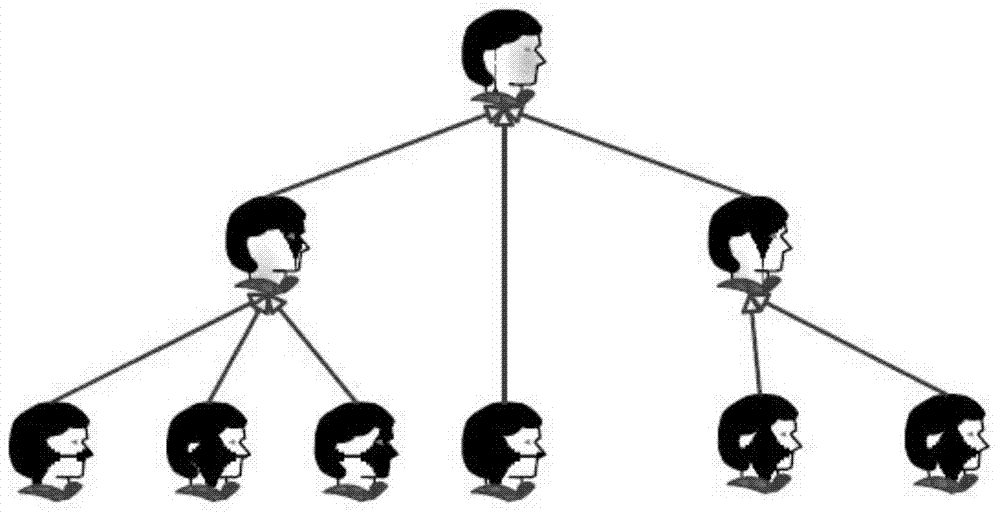
[0048] First, briefly describe the solution of the present invention: first, implement the organization’s access policy through identity-based access control, the central node of the source system as the subject, and the central node of the destination system as the object, which needs to be verified by the access rules, that is, the permission expression In order to realize the mutual communication between the subject and the object. Second, using RBAC, roles are introduced into the subject, and tags are introduced into the object. If the verification is passed, the object returns a Token to the role, so that the role defines read permission (r) and write permission (w) to read and write files with the tag. Third, each subject is associated with a role, and the role has different read and write permissions to access the object tag. According to different permissions, the reading and writing process will not be confused and the efficiency will be improved.
[0049] The securit...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com