Mobile terminal and encrypting method and device for telephone answering of mobile terminal
A technology of telephone answering and encryption method, which is applied in the direction of telephone communication, security devices, electrical components, etc., and can solve the problems of not being able to guarantee the confidentiality and security of the user's call, and the inability to guarantee the privacy of the user's call
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
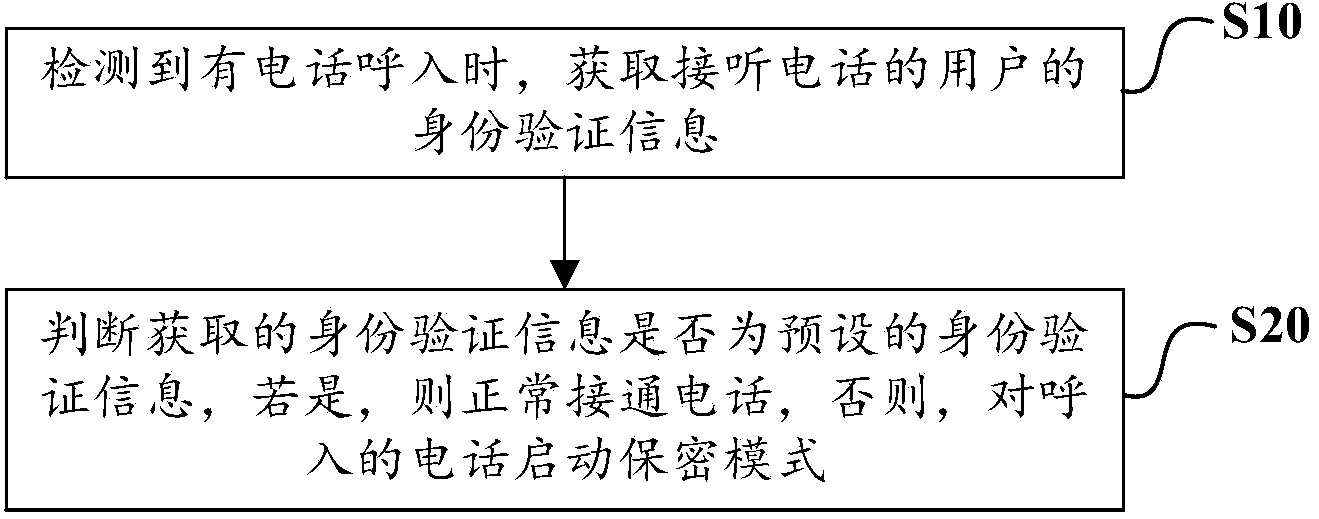
[0045] figure 1 It is a flow chart of the encryption method for answering calls according to an embodiment of the present invention, combined below figure 1 To describe the encryption method for telephone answering according to an embodiment of the present invention, the method is applied to a mobile terminal, and the mobile terminal refers to other portable electronic devices such as mobile phones that can answer calls or voices, such as figure 1 As shown, the encryption method for answering the call includes the following steps:
[0046] S10. When an incoming call is detected, the identity verification information of the user who answers the call is obtained;
[0047] S20 , judging whether the acquired identity verification information is preset identity verification information, and if so, connect the call normally, otherwise, activate the confidentiality mode for the incoming call.
[0048] Wherein, the above-mentioned activation of the privacy mode may be, for example, ...
Embodiment 2
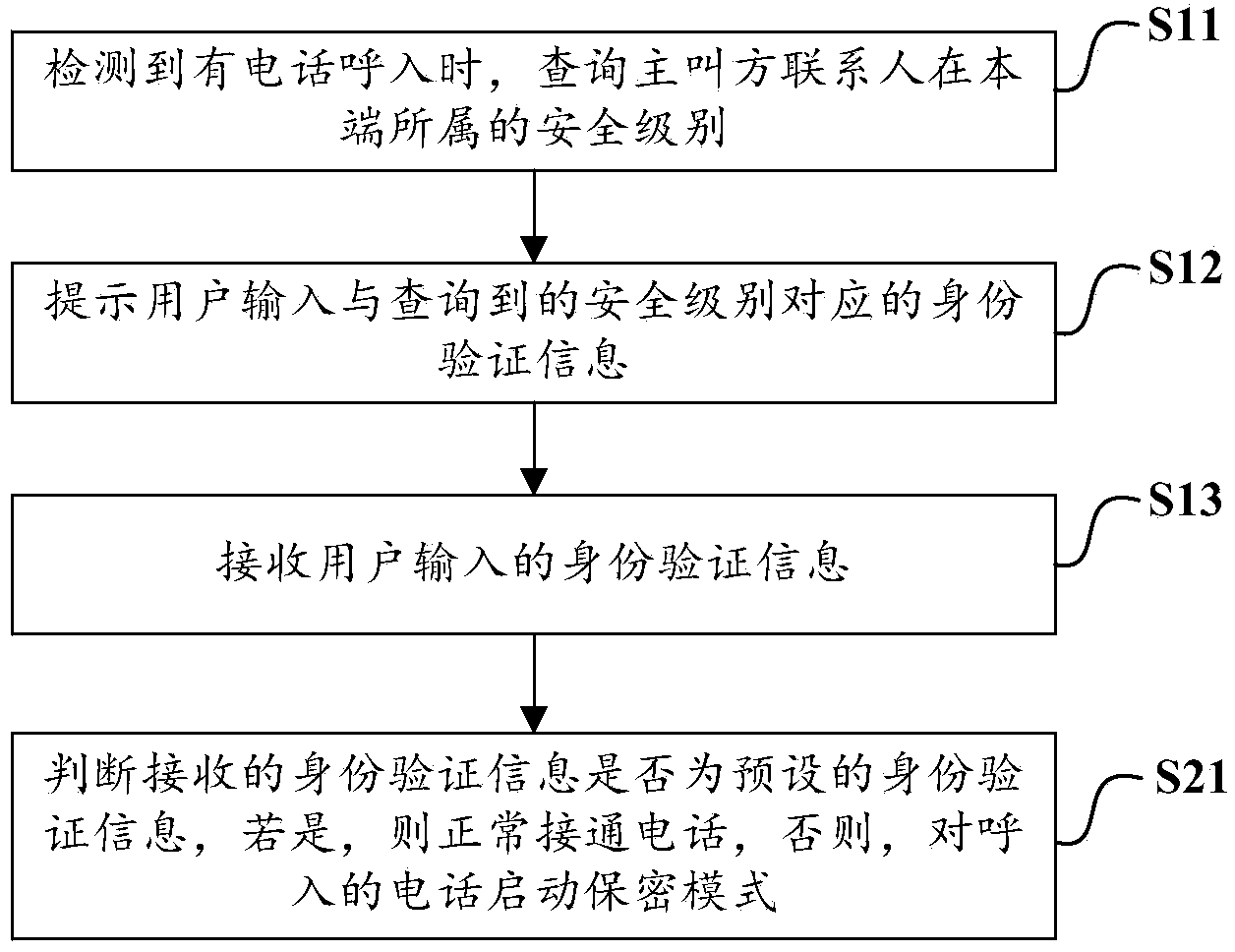
[0054] figure 2 It is a flow chart of an encryption method for answering a call according to another embodiment of the present invention, the method is applied to a mobile terminal, and the mobile terminal is preset with corresponding security levels for different contacts, and each security level is pre-stored Different authentication information, for the above-mentioned authentication information of the user who answers the call, such as figure 2 As shown, the above step S10 specifically includes:
[0055] S11. When an incoming call is detected, query the security level of the contact of the calling party at the local end;
[0056] S12. Prompting the user to input identity verification information corresponding to the queried security level;
[0057] S13. Receive identity verification information input by the user.
[0058] Correspondingly, the above step S20 is specifically:
[0059]S21. Determine whether the received identity verification information is preset identi...
Embodiment 3
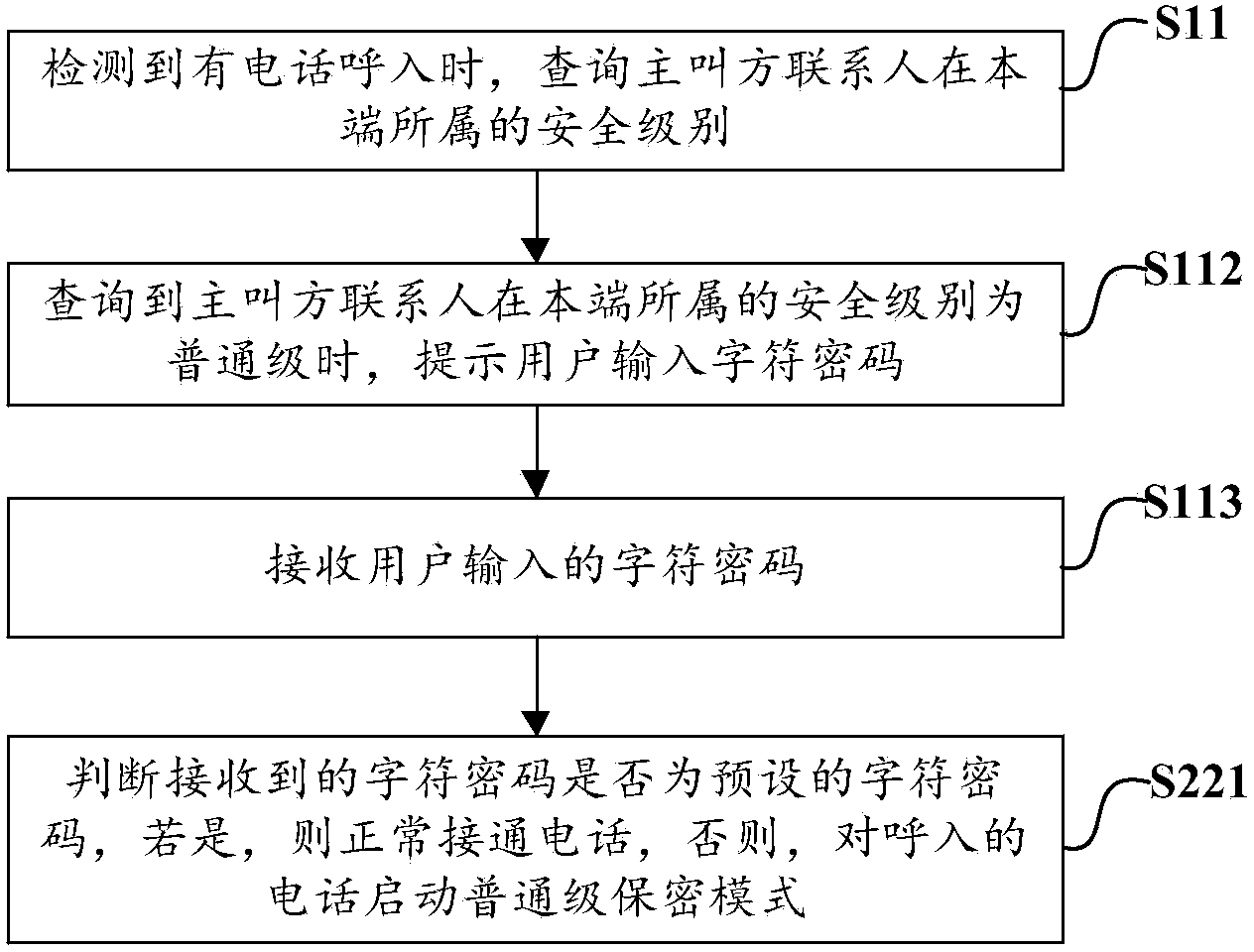
[0064] image 3 It is a flow chart of an encryption method for answering a call according to another embodiment of the present invention, the encryption method for answering a call is applied to a mobile terminal, and the mobile terminal presets a contact person designated by the user as a normal security level, and The identity verification information corresponding to the ordinary security level is a character password, and the encryption method for answering the call includes the above step S11 on the basis of:
[0065] The above-mentioned step S12 is specifically step S112, when it is found that the security level of the calling party contact at the local end is the normal security level, prompting the user to input a character password;
[0066] The above step S13 is specifically step S113, receiving the character password input by the user;
[0067] The above-mentioned step S20 (or S21) is specifically step S221, judging whether the received character password is a pres...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com