Method and device for fault injection attack based on simulation
A fault injection and fault technology, applied in the direction of software testing/debugging, can solve the problems of difficult to observe failure behavior, faulty devices, invisible signals, long time period, etc., and achieve the effect of intuitive and controllable fault injection.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0052] The present invention will be further described below in conjunction with the accompanying drawings and specific embodiments.
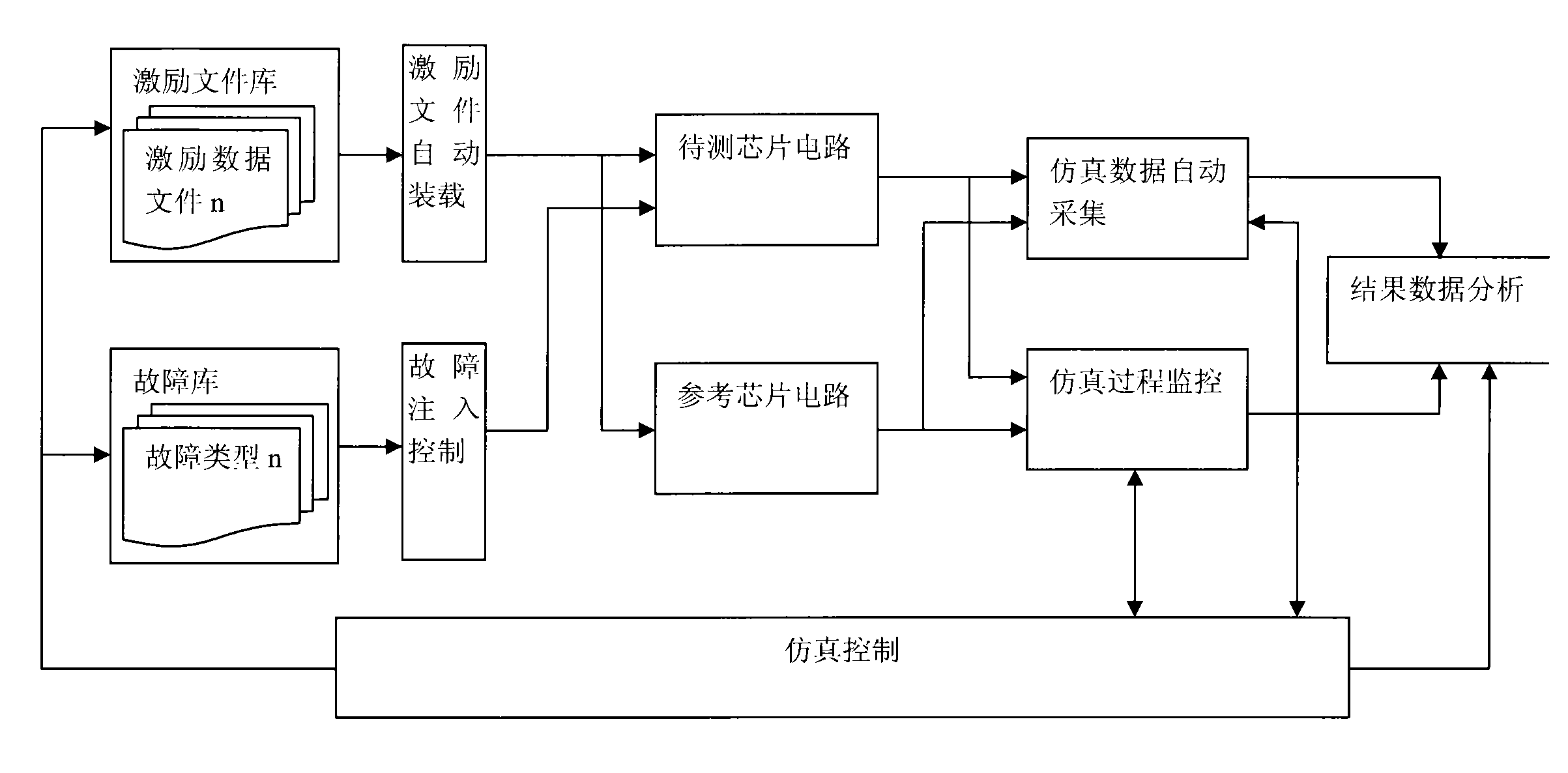
[0053] Such as figure 1As shown, a fault injection attack method based on simulation, its platform implementation frame diagram, including stimulus file library unit, fault library unit, stimulus file automatic loading unit, fault injection control unit, chip circuit under test, reference chip circuit, simulation An automatic data collection unit, a simulation process monitoring unit, a data result analysis unit and a simulation control unit.
[0054] The chip circuit to be tested refers to the chip circuit design with safety protection design to be evaluated. Including but not limited to: algorithm module unit, such as DES, AES, etc., storage control unit, CPU, or full chip, etc.
[0055] The reference chip circuit refers to a chip circuit design that does not inject fault attacks and has the same function as the chip circuit to be tested. ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com