Trojan horse detection method based on traffic analysis without control terminal
A detection method and flow analysis technology, applied to electrical components, transmission systems, etc., can solve problems such as communication speed reduction and weakened flow characteristics
Active Publication Date: 2018-01-30
PLA STRATEGIC SUPPORT FORCE INFORMATION ENG UNIV PLA SSF IEU
View PDF5 Cites 0 Cited by
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Due to the data of different ports selected for user modeling, the Trojan horse program uses covert channel technology to reduce its own communication speed and weaken its own traffic characteristics, which will cause the method to fail
Method used
the structure of the environmentally friendly knitted fabric provided by the present invention; figure 2 Flow chart of the yarn wrapping machine for environmentally friendly knitted fabrics and storage devices; image 3 Is the parameter map of the yarn covering machine
View moreImage
Smart Image Click on the blue labels to locate them in the text.
Smart ImageViewing Examples
Examples
Experimental program
Comparison scheme
Effect test
Embodiment 1
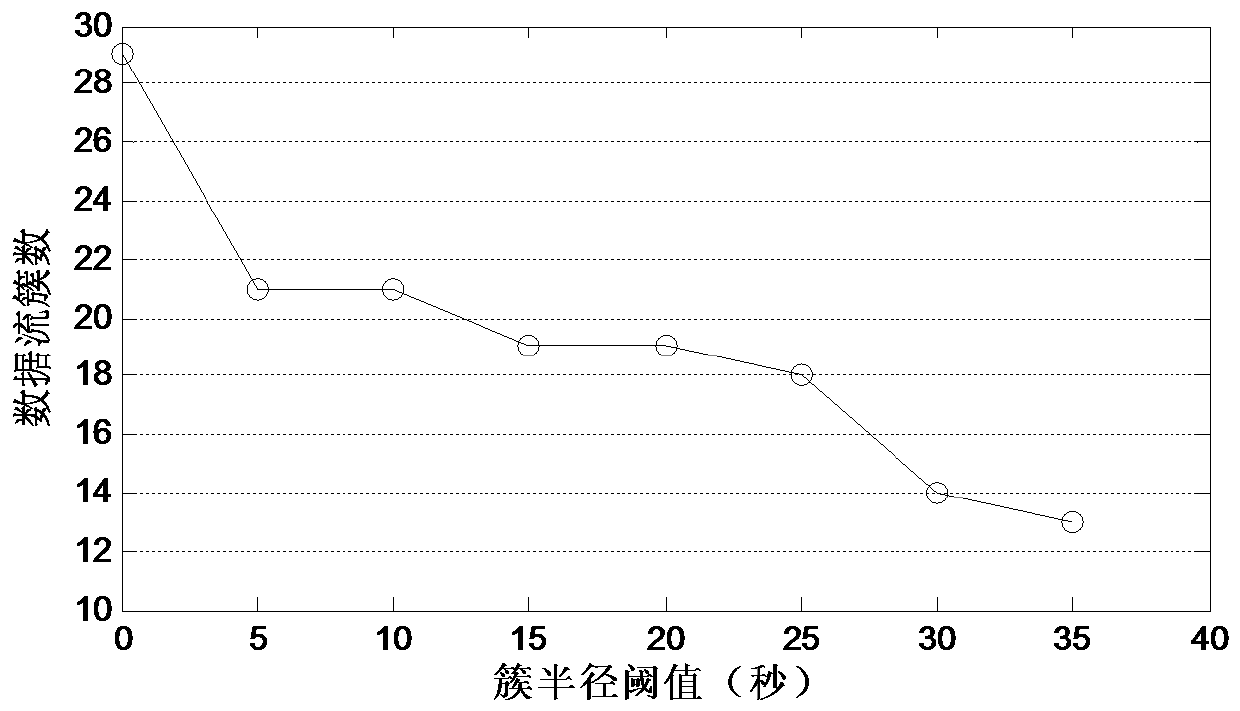
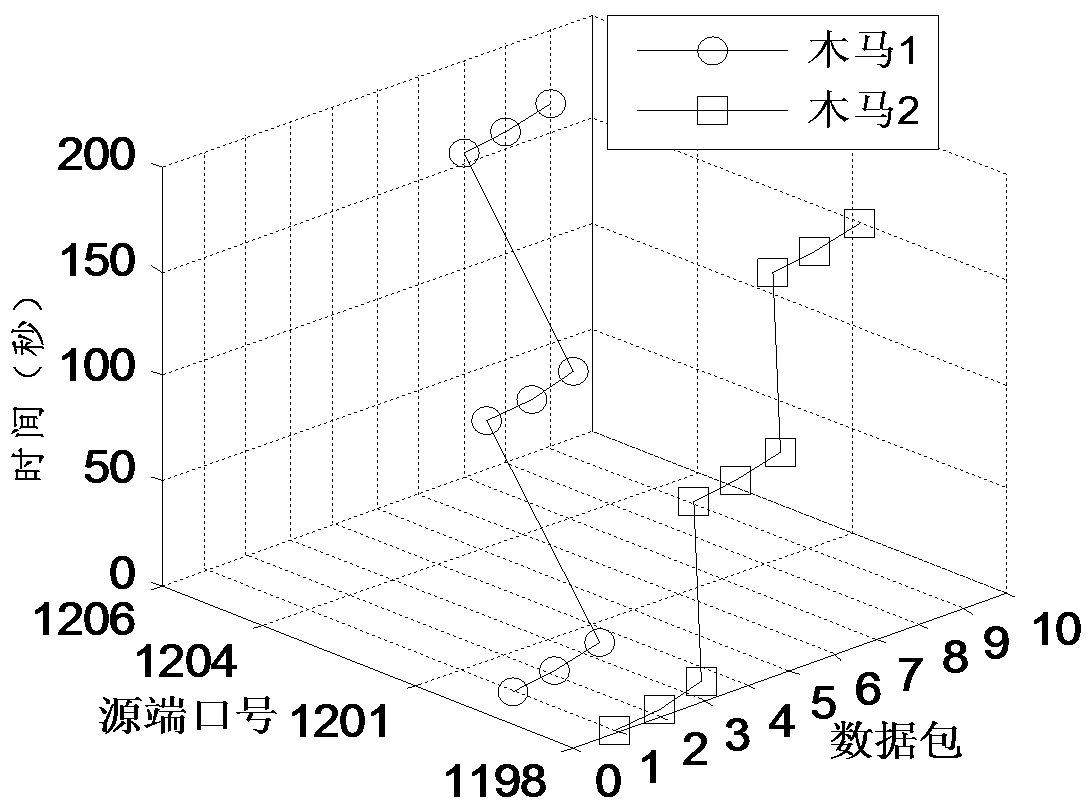
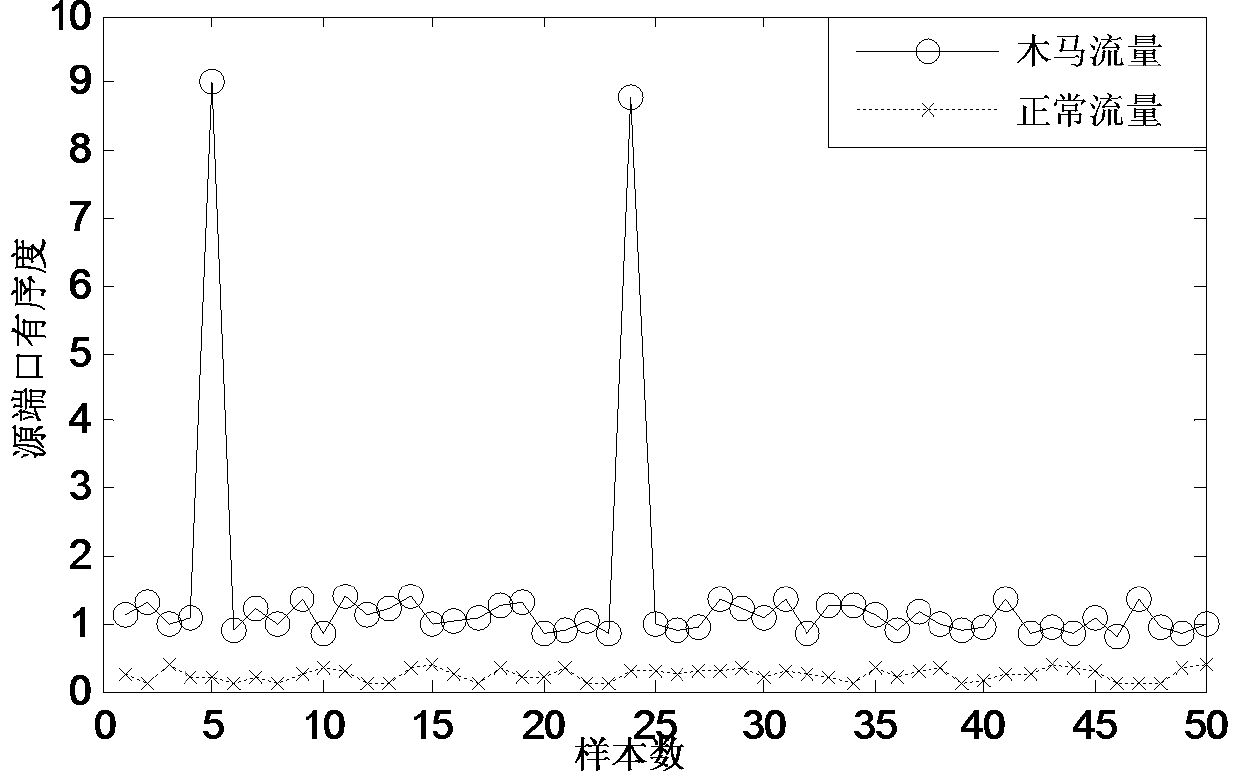
[0065] Embodiment 1: The Trojan horse detection method based on no control terminal flow analysis is:
the structure of the environmentally friendly knitted fabric provided by the present invention; figure 2 Flow chart of the yarn wrapping machine for environmentally friendly knitted fabrics and storage devices; image 3 Is the parameter map of the yarn covering machine
Login to View More PUM
 Login to View More
Login to View More Abstract
The invention discloses a torjan detection method based on uncontrolled end flow analysis. The method includes the steps that firstly, a captured network data package is processed; secondly, the network data package is organized into data flows according to quintuple information and requirements of protocol specifications; then, the data flows are classified according to equivalent tetrads to form data flow sets identified by the tetrads; finally the data flows in the data flow sets are clustered to form data flow clusters by the adoption of a data flow clustering algorithm based on timestamps. According to the torjan detection method based on the uncontrolled end flow analysis, on the basis of carrying out clustering on the network data flows to form the data flow clusters, the data flows are processed with the data flow cluster as a unit to analyze the difference between torjan communication behaviors and normal network communication behaviors, in addition, the difference between the torjan communication behaviors and the normal network communication behaviors are deeply dug in combination with the technologies of statistic analysis and data mining, and therefore uncontrolled end torjan flow in a network can be detected.
Description
technical field [0001] The invention relates to a Trojan horse detection technology based on communication data flow analysis, in particular to a Trojan horse detection method based on no control terminal flow analysis. Background technique [0002] Most of the current stealing attacks are realized by using Trojan horses. The biggest feature of Trojan horses is that their behavior often has strong concealment. After the Trojan horse is successfully implanted into the target computer, the Trojan horse control terminal must communicate with the controlled terminal, so as to issue control instructions to the controlled terminal or control the controlled terminal to return the obtained information to the control terminal. At this stage, the detection and identification of Trojan horse communication traffic is mainly aimed at the situation where the Trojan horse is controlled by the program and the control terminal program has established a connection, and less attention is paid ...
Claims
the structure of the environmentally friendly knitted fabric provided by the present invention; figure 2 Flow chart of the yarn wrapping machine for environmentally friendly knitted fabrics and storage devices; image 3 Is the parameter map of the yarn covering machine
Login to View More Application Information
Patent Timeline
 Login to View More
Login to View More Patent Type & Authority Patents(China)
IPC IPC(8): H04L29/06
CPCH04L63/1408H04L63/145
Inventor 刘胜利王文冰费金龙刘龙陈岩武东英林伟吴双
Owner PLA STRATEGIC SUPPORT FORCE INFORMATION ENG UNIV PLA SSF IEU
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com