A multi-user encryption system and communication method for automatically identifying communication protocols
A communication protocol and encryption system technology, applied in the computer field, can solve the problems of wasting resources, cannot be repeated, and difficult to prevent, and achieve the effect of saving costs and simplifying inventory management
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0035] The technical solution of the present invention is mainly aimed at chip applications that require encryption and system applications composed of them, including but not limited to printer encryption, system software encryption protection, PCBA encryption protection, set-top box encryption, mobile phone information encryption protection, etc.
[0036] In this specification, the word "unit" includes but not limited to software functional units, hardware circuit units, functional units realized by hardware and its complementary software.
[0037] The technical solutions of the present invention will be further described below in conjunction with the accompanying drawings and through specific implementation methods.
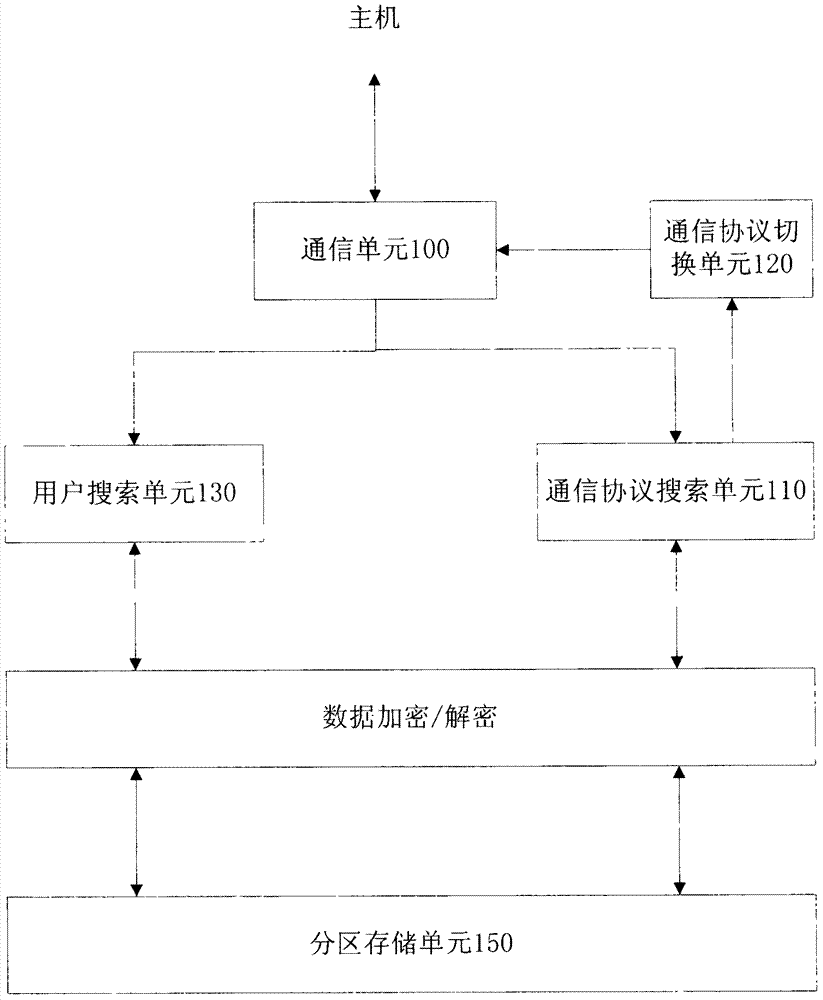
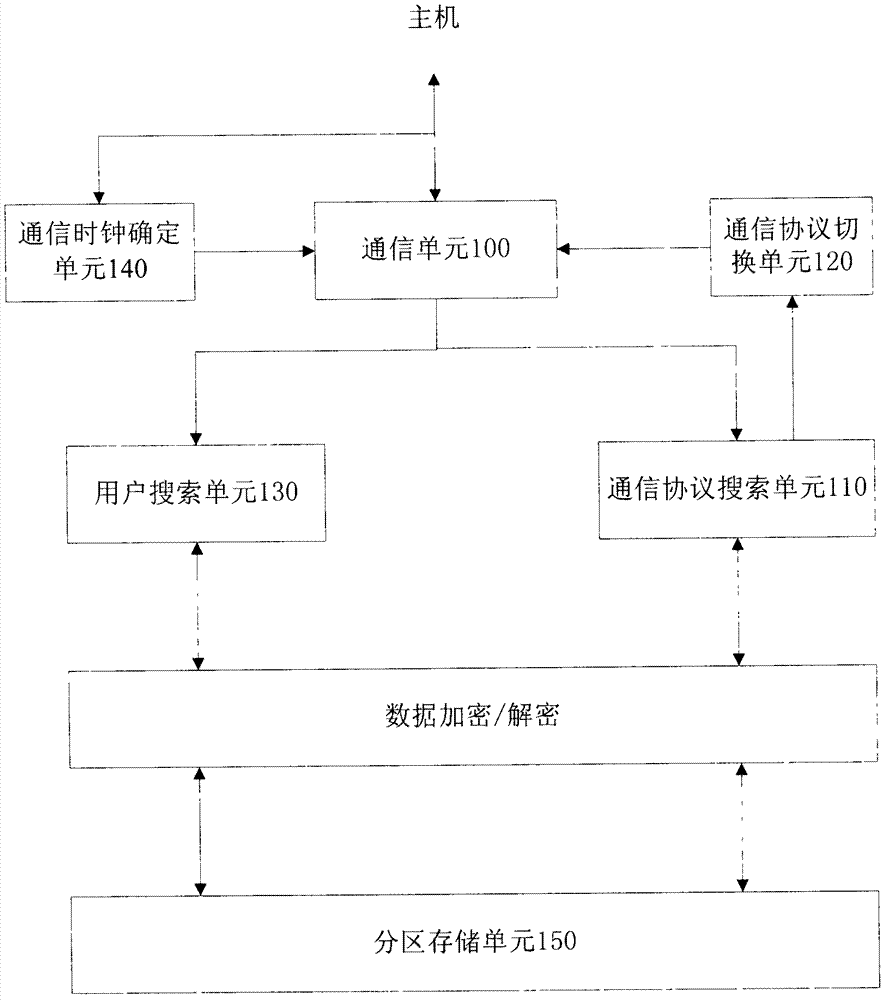
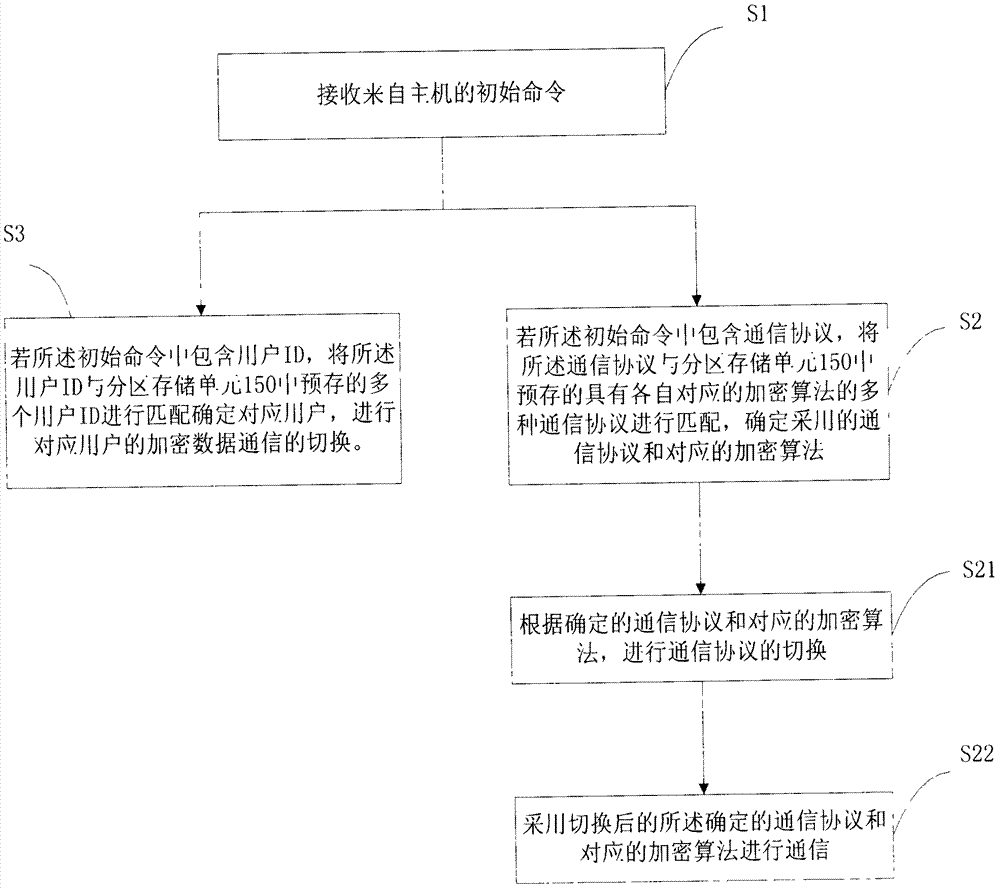
[0038] figure 1 It is a structural block diagram of the first embodiment of a multi-user encryption system that automatically recognizes communication protocols in the present invention. As shown in the figure, it includes a communication unit 100, a communica...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com