Safe data storage and transmission method
A technology for data transmission and secure storage, applied in the field of information security, to shorten the encryption time, save the encryption time, and improve the efficiency
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
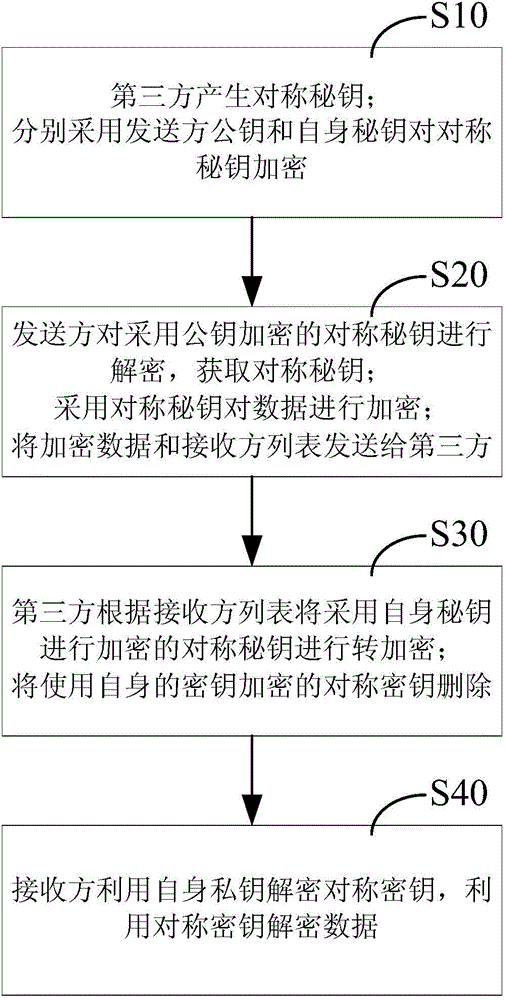
[0020] Based on the defects of the prior art, the present invention provides a method for securely storing and transmitting data.
[0021] Such as figure 1 Shown, the present invention comprises the following steps:
[0022] Step S10: The third party generates a symmetric key cache, encrypts it and sends it to the data sender.
[0023] In this embodiment, first, a third party that normally communicates with the data sender and the data receiver needs to be preset. The third party has the function of quickly implementing big data calculations, and may include, for example, a cloud server or an encryption machine.
[0024] The third party generates a symmetric key, first encrypts the generated symmetric key with the public key of the data sender, and then sends the encrypted symmetric key to the data sender.
[0025] In addition, the third party encrypts the generated symmetric key with its own key and saves it. The third party's own key includes a private key or a generated ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com