Credibility detection method based on password hash and biometric feature recognition
A technology of biometric identification and biometric information, which is applied in the field of computer security, can solve problems such as the inability to identify the user's physical identity, and the computer information detection code is easily reversed, so as to avoid the hidden danger of change and replacement and protect privacy.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
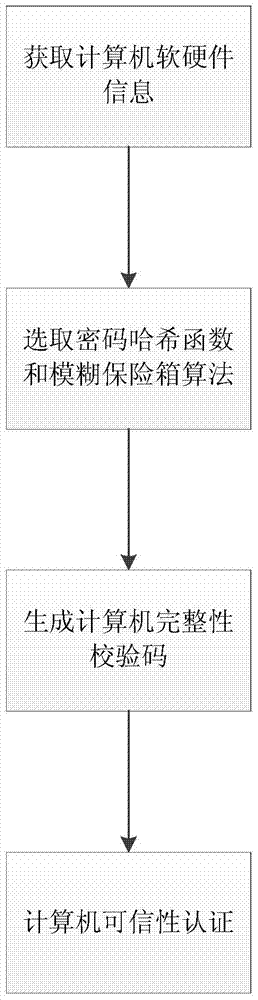
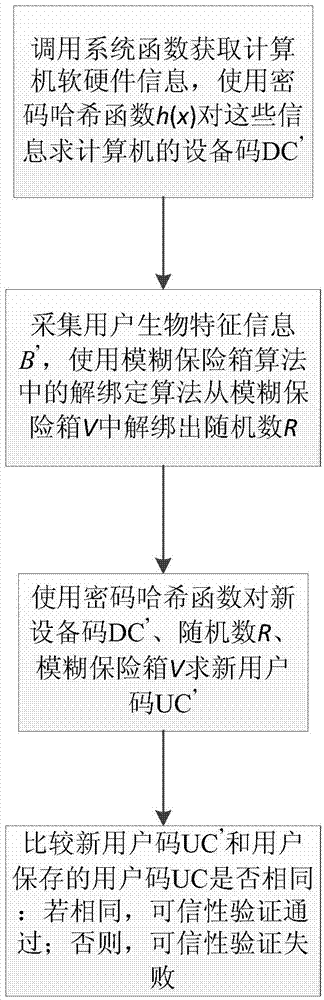
[0025] refer to figure 1 , the implementation steps of the present invention are as follows:
[0026] Step 1, obtain the software and hardware information of the computer.
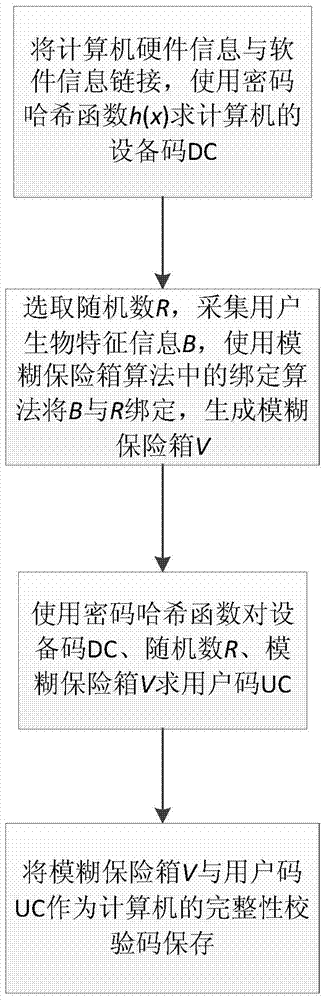
[0027] Call the system function to obtain computer hardware information, such as CPU, hard disk, memory, network card, graphics card, recorded as ID i , i=1,2,3...n, wherein n is the number of hardware to be counted in the computer;
[0028] Call the system function to obtain computer software information, such as operating system, office software, chat tool, denoted as SW j , j=1,2,3...m, where m is the number of software in the computer that needs to be counted.
[0029] Step 2, select the cryptographic hash function, and select the fuzzy safe algorithm.
[0030] 2a) Choose a cryptographic hash function as the encryption function
[0031] Compared with similar encryption methods, the cryptographic hash function has the characteristics of being easy to calculate, difficult to deduce information in re...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com