A Mimic Anti-theft Method for Distributed File System
A distributed file and anti-theft technology, applied in the computer field, can solve the problem of reducing the possibility of simultaneous hijacking of components, and achieve the effect of improving overall security, reducing the risk of information leakage, and reducing the risk of information leakage
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
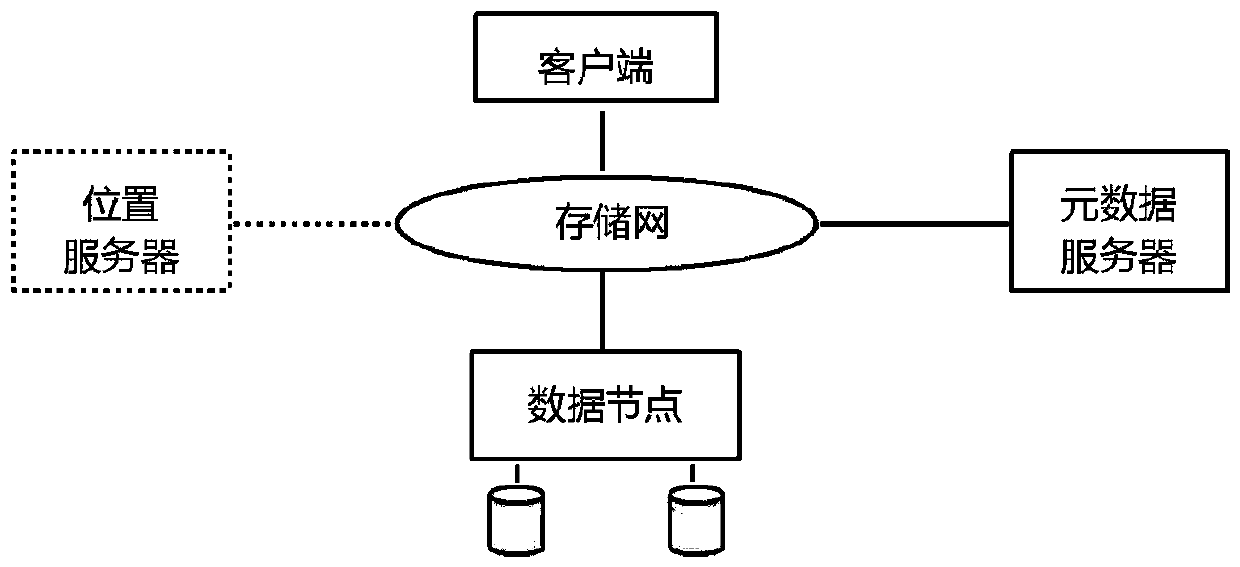
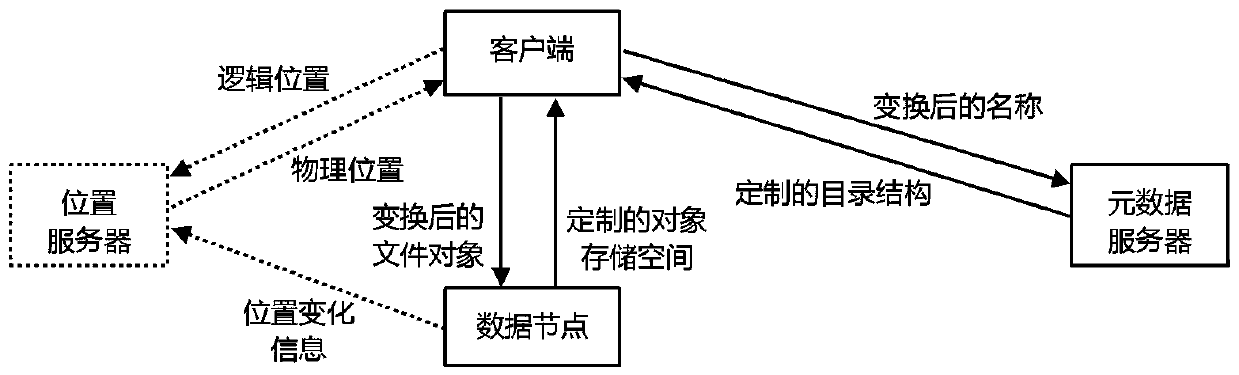
[0031] Embodiment 1, combining Figure 1-Figure 6 A mimetic anti-theft method of a distributed file system includes a hardware environment, the hardware environment includes: data nodes, metadata servers, location servers and clients. The steps for realizing the mimetic anti-theft method described in the client are: Distribution, distributes the management functions of the distributed file system to different components, the metadata server manages the metadata of the file system and its organizational relationship, and the client is responsible for the segmentation and assembly of file data, the generation and operation of file objects, The content of the file object is managed by the data node, and the storage location of the file object is managed by the location server; step 2, transform, transform the format, content and storage location of the information, the client transforms the path name and identification information of the file, and the metadata server presses the t...
Embodiment 2
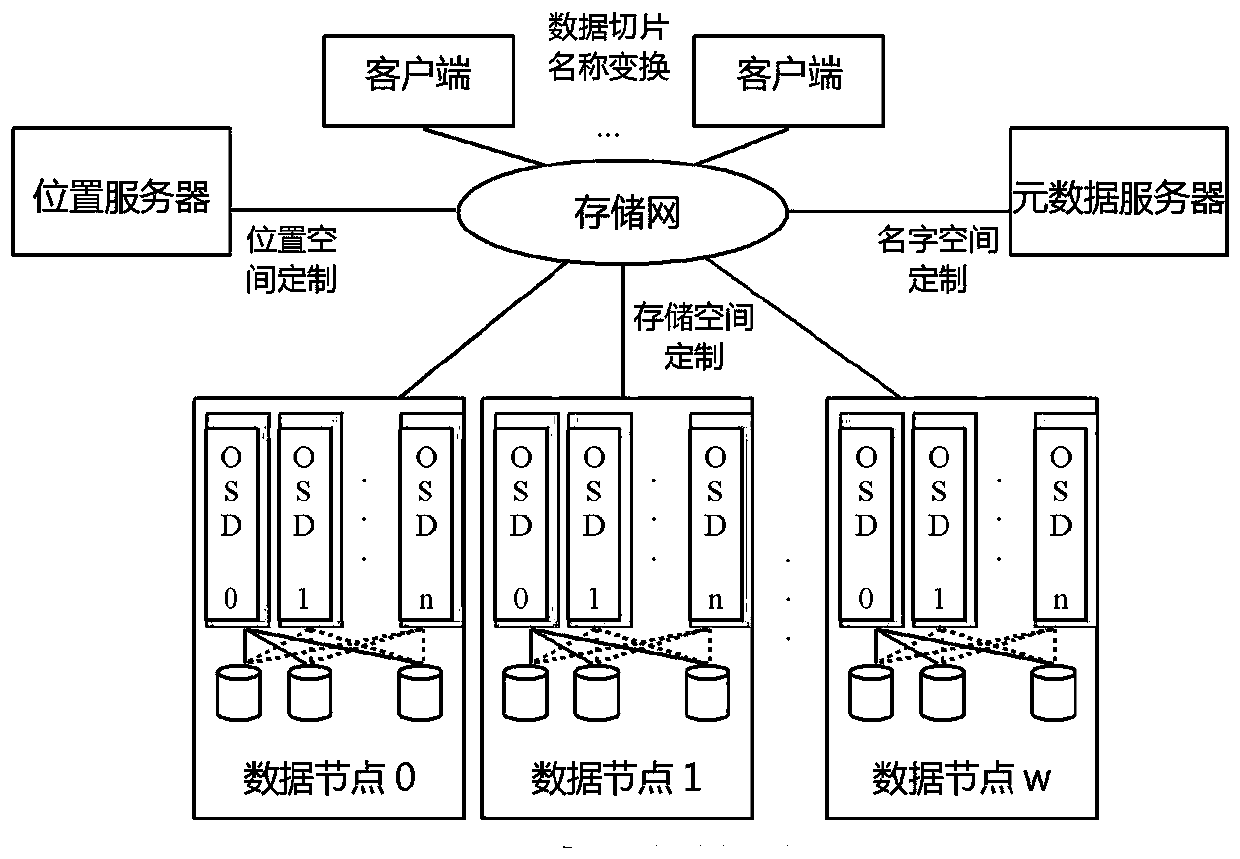
[0041] Example 2: Combining image 3 , establish a first-level directory for each type of client on the data node, and pre-establish several second-level directories under this directory, such as AG0,...,AGm, BG0,...,BGn, etc. The second-level directories should be Scattered across different disks of the data nodes. The client's file objects are all stored in its own directory, and a client's directory is only allowed to be accessed by itself.
[0042] An OSD process is provided for each client in a data node. All file objects of a client in a data node are managed by an OSD process. An OSD process only serves one client, and an OSD process is in a data node. Construct a logical file object storage space for a client.
[0043] Further, using the Linux container mechanism, each OSD process is packaged in a container, so that each OSD process has different network configurations and different name spaces, such as node name, machine name, operating system version, processing d...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com