Credit card encryption method and device
An encryption method and encryption device technology, applied in the field of information security, can solve problems such as potential safety hazards, malicious consumption, and consumer losses, and achieve the effect of convenience and security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
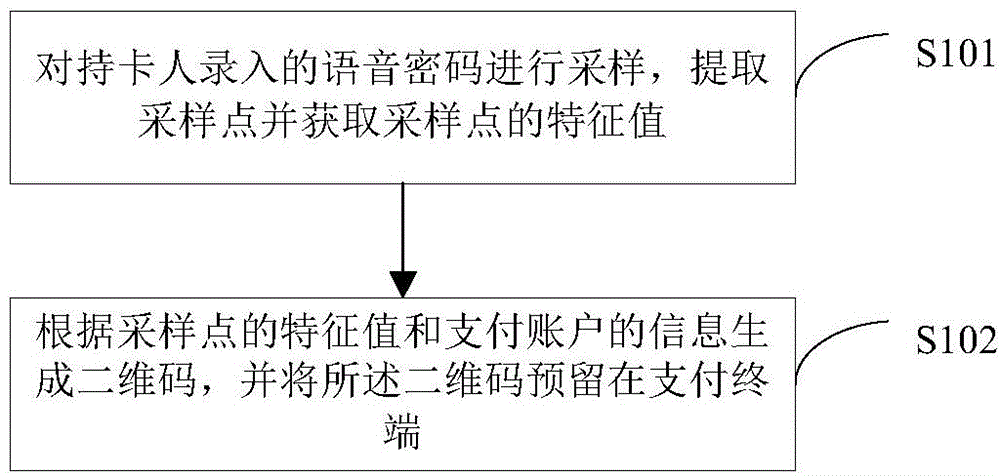
[0088] Figure 4 It is a flowchart of a credit card encryption method in Embodiment 1 of the present invention. Such as Figure 4 As shown, the following steps S401-S409 are included:
[0089] Step S401, sampling the voice password entered by the cardholder, extracting the sampling point and obtaining the feature value of the sampling point;
[0090] Step S402, generate a two-dimensional code according to the characteristic value of the sampling point and the information of the payment account, and reserve the two-dimensional code in the payment terminal;
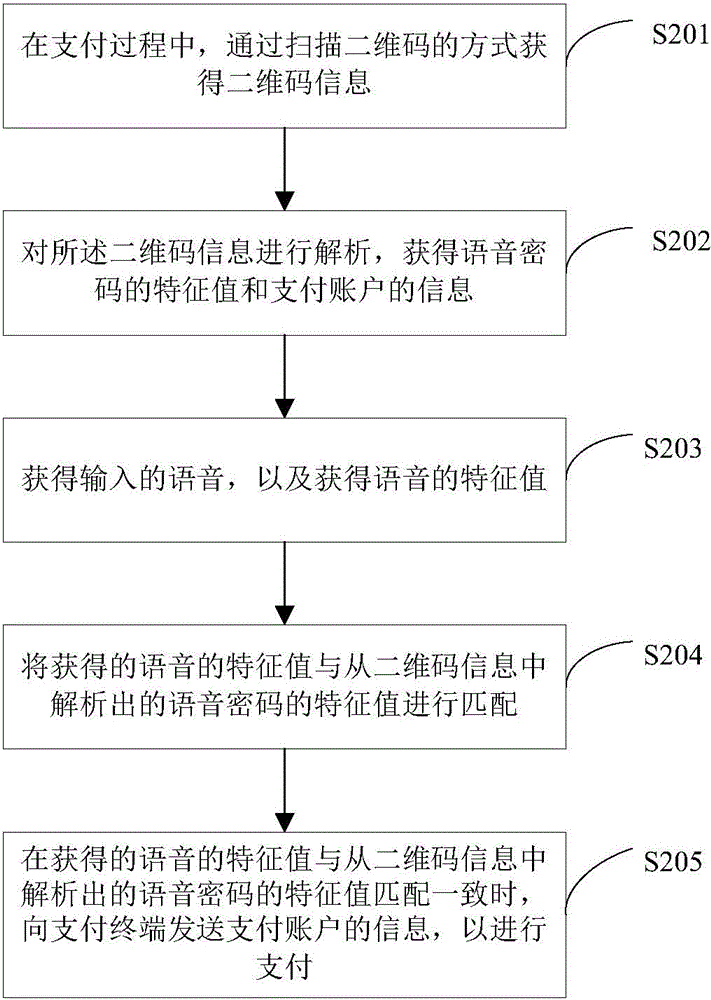
[0091] Step S403, during the payment process, obtain the two-dimensional code information by scanning the two-dimensional code;
[0092] Step S404, analyzing the two-dimensional code information to obtain the characteristic value of the voice password and the information of the payment account;
[0093] Step S405, obtaining the input speech, and obtaining the feature value of the speech;
[0094] Step S406, matching th...
Embodiment 2
[0122] like Figure 8 As shown, the credit card encryption device provided by the embodiment of the present invention includes:
[0123] Generating unit 11; The generating unit 11 includes:
[0124] The sampling module 111 is used to sample the voice password entered by the cardholder, extract the sampling point and obtain the feature value of the sampling point;
[0125] The generating module 112 is configured to generate a two-dimensional code according to the characteristic value of the sampling point and the information of the payment account, and reserve the two-dimensional code in the payment terminal.
[0126] A payment unit 12; the payment unit 12 includes:
[0127] The scanning module 121 is used to obtain the two-dimensional code information by scanning the two-dimensional code during the payment process;
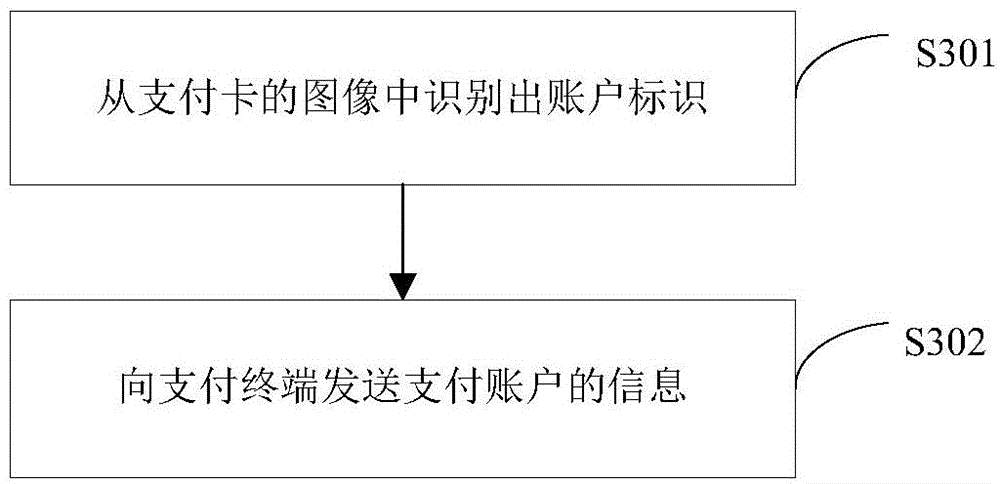
[0128] The analysis module 122 is used to analyze the two-dimensional code information to obtain the feature value of the voice password and the information of...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com