Device and method certificate generation
A device and certificate technology, applied in the field of device authentication, can solve the problems of exposing passwords and difficult to trust certificates, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
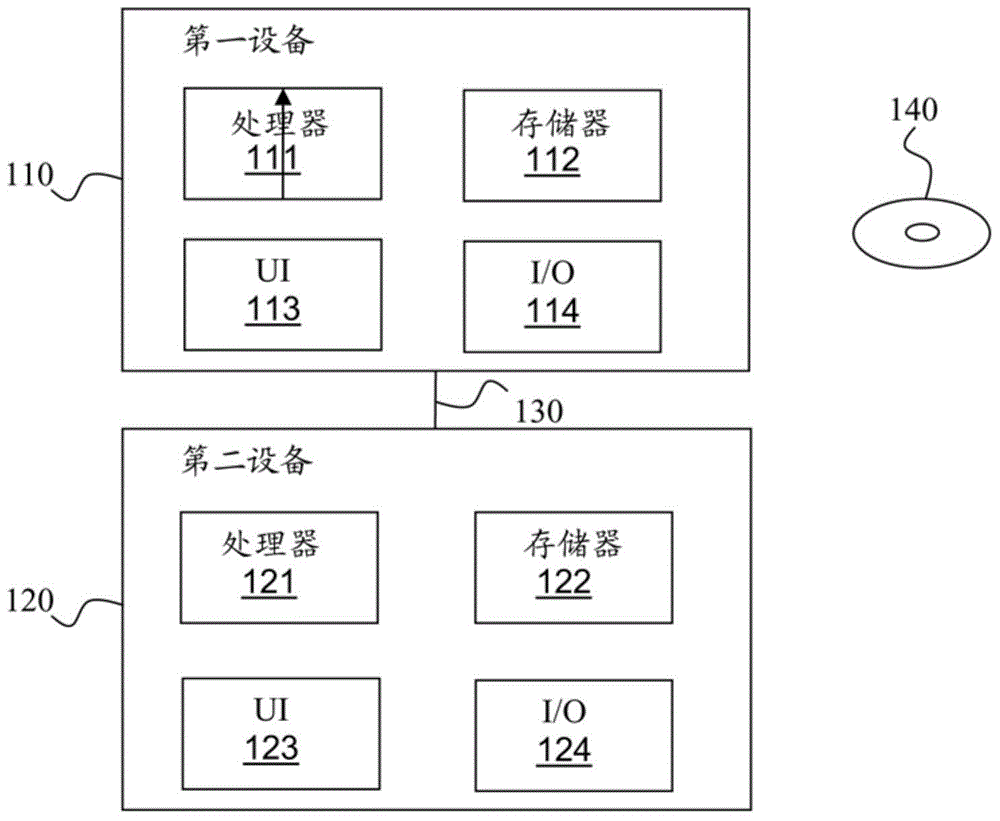
[0036] figure 1 An exemplary system 100 implementing the present disclosure is shown. The system 100 includes a first computing device ("first device") 110 and a second computing device ("second device") 120 . The first and second devices 110, 120 may be any kind of suitable computer or device capable of performing computations, such as standard personal computers (PCs), workstations, smartphones and tablets. Each of the first and second devices 110, 120 preferably comprises at least one processor 111, 121, internal or external memory 112, 122, a user interface 113, 123 for interacting with a user, and a second device for interacting with other devices via a connection 130. Interface 114,124. The first and second devices 110, 120 each also preferably comprise an interface (not shown) for reading a software program from a digital data carrier 140 storing instructions which, when executed by a processor, perform any of the methods described hereinafter . Those skilled in the...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com