A method and system for integrated management of information security equipment based on transparent computing
A transparent computing and information security technology, applied in computer security devices, computing, electronic digital data processing, etc., to achieve strong adaptability and scalability
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0036] Below in conjunction with embodiment, further illustrate the present invention.
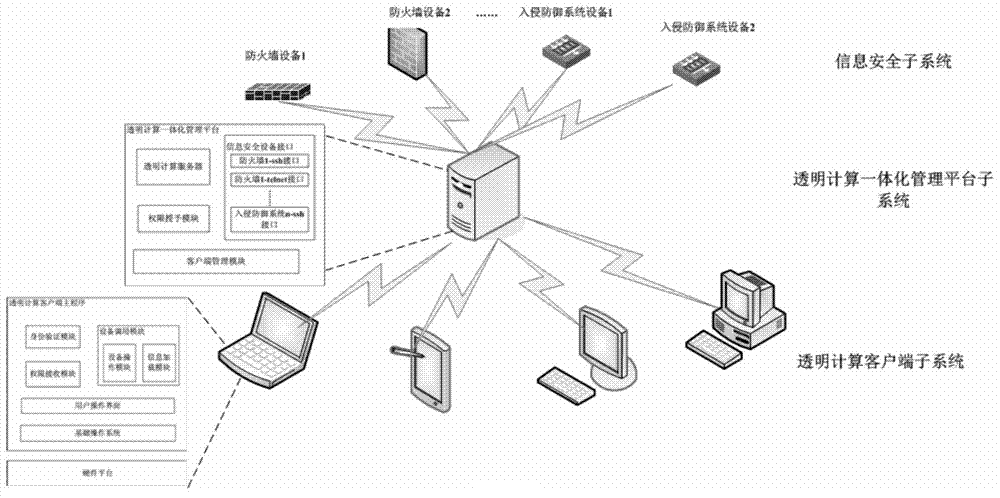
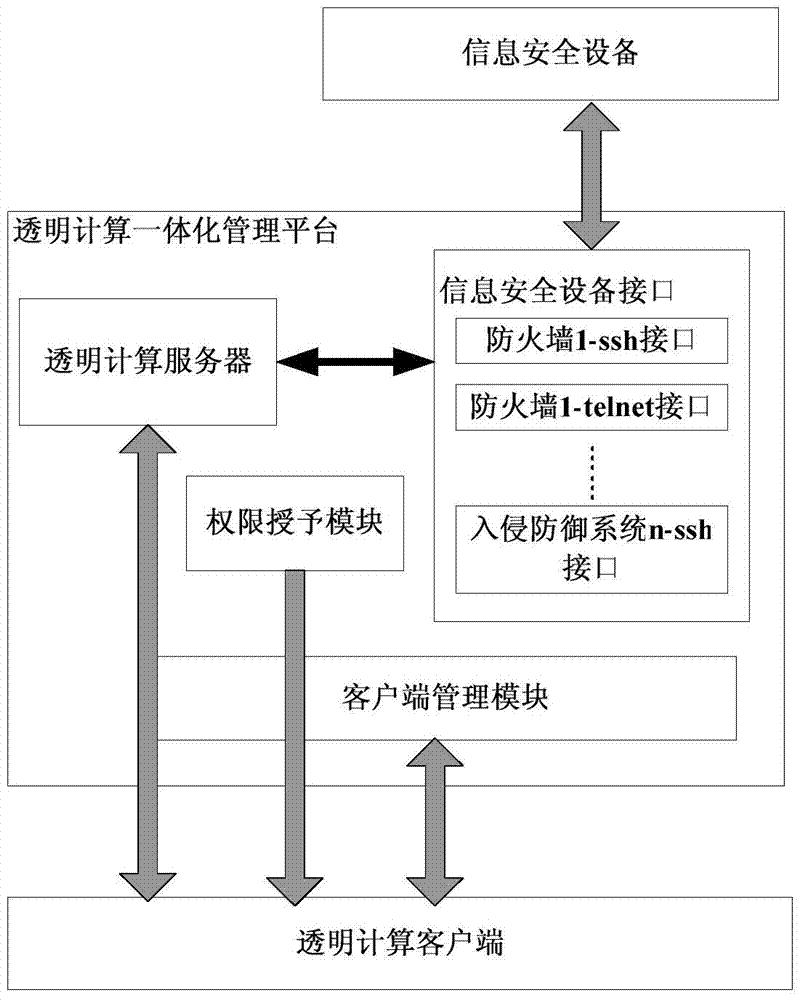
[0037] like figure 1 As shown, the integrated management architecture of information security equipment based on transparent computing includes transparent computing client, transparent computing integrated management platform, and information security equipment.
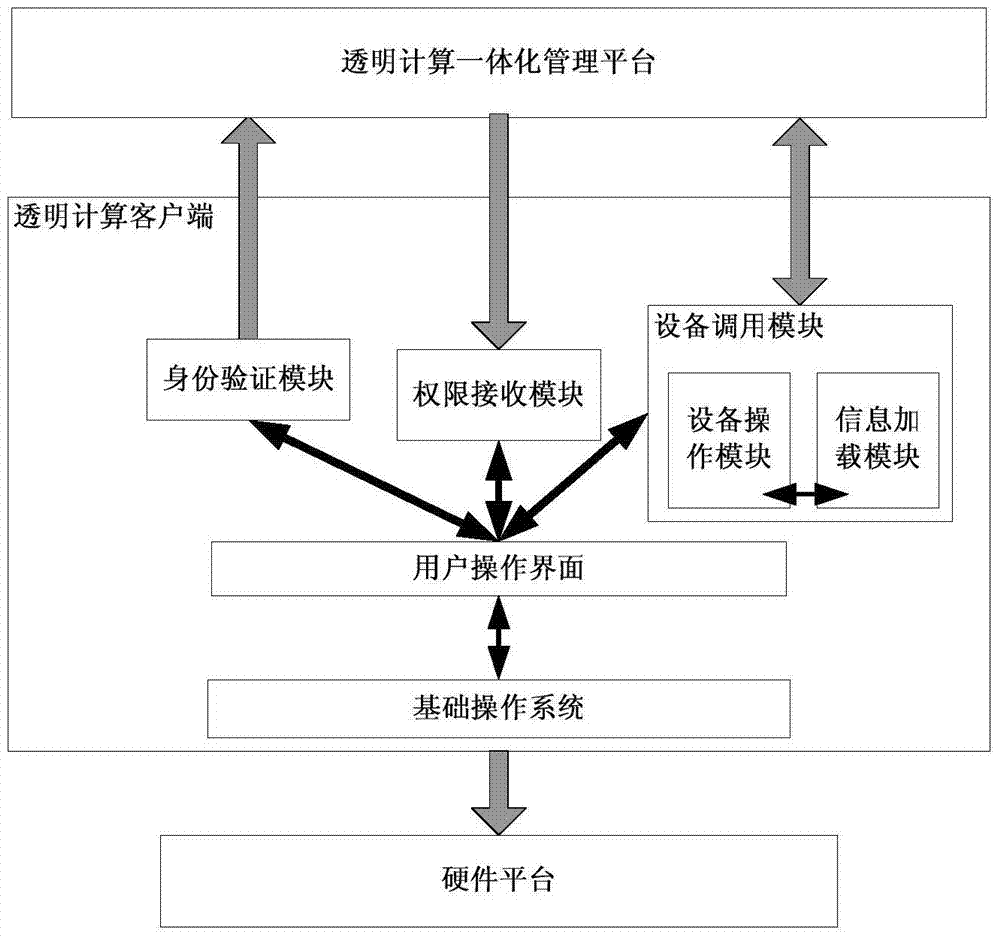
[0038] like figure 2As shown, the transparent computing client includes an identity verification module, a permission receiving module, and a device calling module; the identity verification module is used to verify the current user to ensure the legitimacy of the current user; the permission receiving module is used to receive information from the transparent computing integrated The user can operate a security device only if the information security device grants the authority to the user through the integrated management platform; the device call module is used when the user operates the device. The information from the in...
PUM
 Login to view more
Login to view more Abstract
Description
Claims
Application Information
 Login to view more
Login to view more - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap