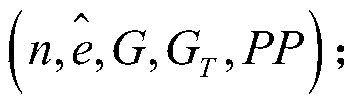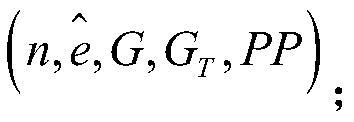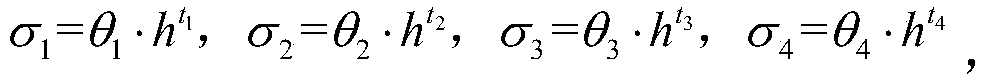An Obfuscation Method for Encrypted Group Signature
A technology of group signature and signature key, applied in the fields of cryptography, group signature and confusion theory
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment
[0084] Such as figure 1 As shown in , an obfuscation method for encrypting group signatures, which is used to protect the signature private keys of members in the group, includes the following steps:
[0085] 1) The group owner builds a signature group, and after determining the administrator, obtains the group parameter sequence pub, the master private key MK and the tracking key TK according to the setup algorithm, sets the signature message length to m bits according to the setup algorithm, and the group members Quantity does not exceed 2 k When , the calculated expression of group parameter sequence pub, master private key MK and tracking key TK is:
[0086]
[0087] PP=(g,h,u,v',v 1 ,...,v m ,Ω,A)
[0088] MK=(g α ,ω)∈G×Z n
[0089]
[0090] n=p·q
[0091]
[0092] Ω=g ω
[0093] And meet the constraints: the size of k is linear with λ, and there is a positive integer c 1 and c 2 , with c 1 ×λ≤log 2 p≤c 2 ×λ and c 1 ×λ≤log 2 q≤c 2 ×λ holds,
[...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com