Identity verification method and apparatus
An identity verification method and verification code technology, applied in the field of identity verification methods and devices, can solve the problem of small screen size of mobile phones, and achieve the effects of improving the pass rate, improving user experience, and being easy to input.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
no. 1 example
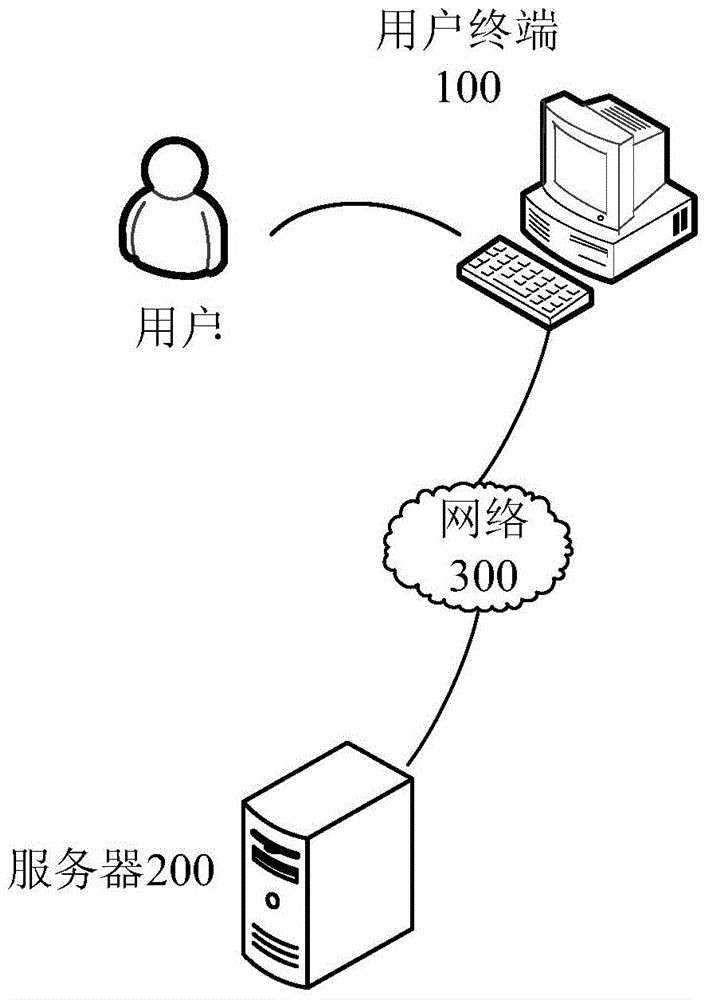
[0049] see Figure 5 , shows a flow chart of an identity verification method provided by the first embodiment of the present invention. combine figure 2 , this embodiment describes the processing flow of the user terminal, and the identity verification method provided by this embodiment includes the following steps:
[0050] Step S11: the user terminal sends a verification code pull request to the server.
[0051] In this step, the user terminal may send a verification code pull request to a pre-configured server (or called a verification code server), for example, a web page address, to obtain the verification code. The page ID can be carried in the verification code pull request. The page ID is used to identify a unique page, which can be a number, and the page ID will change every time the page is refreshed, corresponding to the verification code pull request.
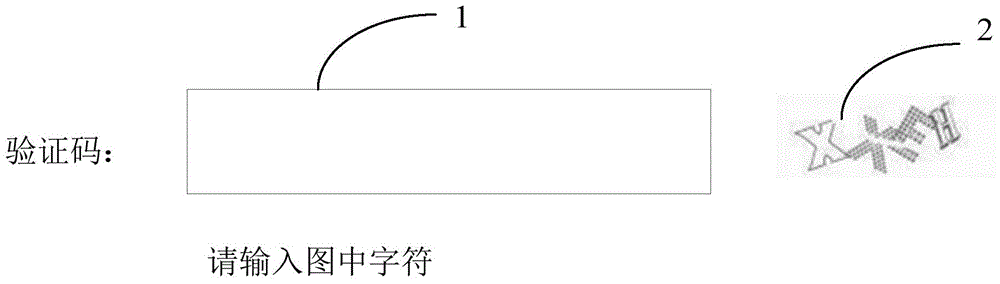
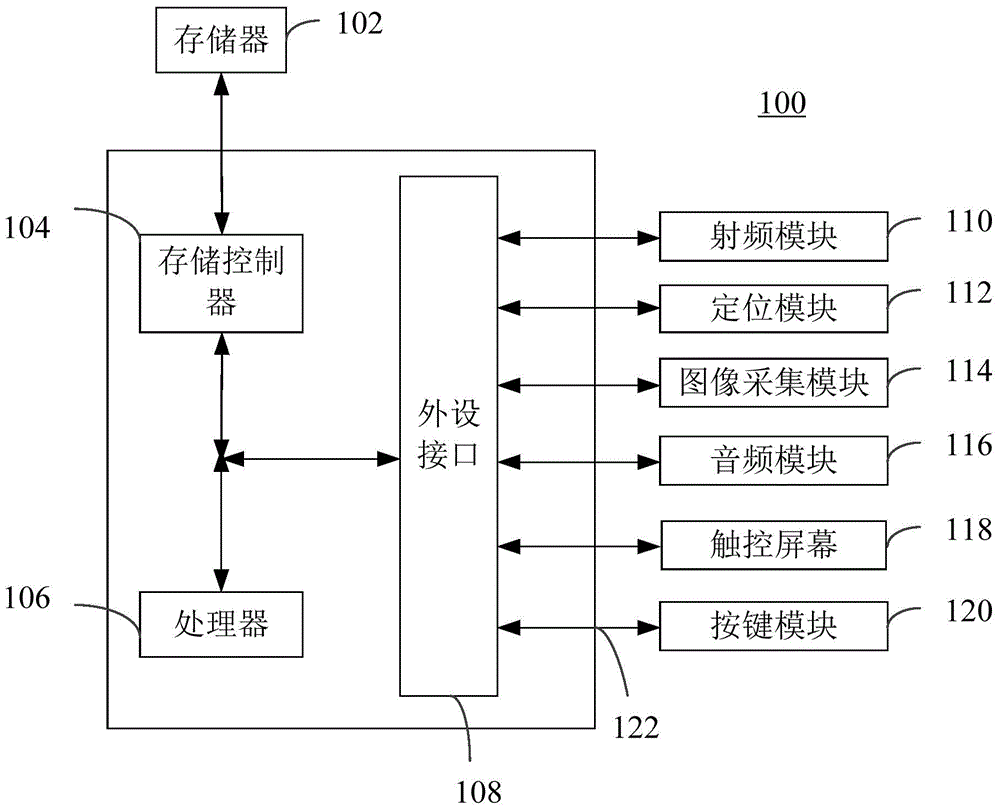
[0052] Step S12: Receive and display the verification code picture and input interface returned by the serve...
no. 2 example
[0070] Figure 7 It is a schematic flowchart of the identity verification method in the second embodiment of the present invention. Please refer to Figure 7 , this embodiment mainly describes the processing flow of the server, and the identity verification method in this embodiment includes:
[0071] Step S21: Receive the verification code pull request sent by the user terminal.
[0072] In this step, the server receives a verification code pull request sent by the user terminal, and the verification code pull request may carry a page identifier.
[0073] Step S22: Generate a verification code picture and an input interface according to the verification code pull request, the content of the verification code picture includes a plurality of verification objects arranged in a predetermined order, the content of the input interface includes a plurality of candidate objects, The multiple candidate objects include at least all verification objects in the verification code pictu...
no. 3 example
[0085] see Figure 8 , shows a flow chart of an identity verification method provided by the third embodiment of the present invention. combine figure 2 , this embodiment describes the interaction processing flow between the user terminal and the server. The authentication methods in this embodiment may include:
[0086] In step S301, the user terminal sends a verification code pull request to the server.
[0087] Step S302, the server generates a verification code picture and an input interface according to the verification code pull request, the content of the verification code picture includes a plurality of verification objects arranged in a predetermined order, and the content of the input interface includes a plurality of candidate objects , the multiple candidate objects include at least all verification objects in the verification code picture.
[0088] Step S303, the server returns the verification code picture and the input interface to the user terminal.
[00...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com