A component protocol mining method, device and system
A protocol and component technology, applied in the field of program mining, can solve the problems of low mining efficiency and high labor consumption, and achieve the effects of improving accuracy and completeness, improving efficiency and reducing costs.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
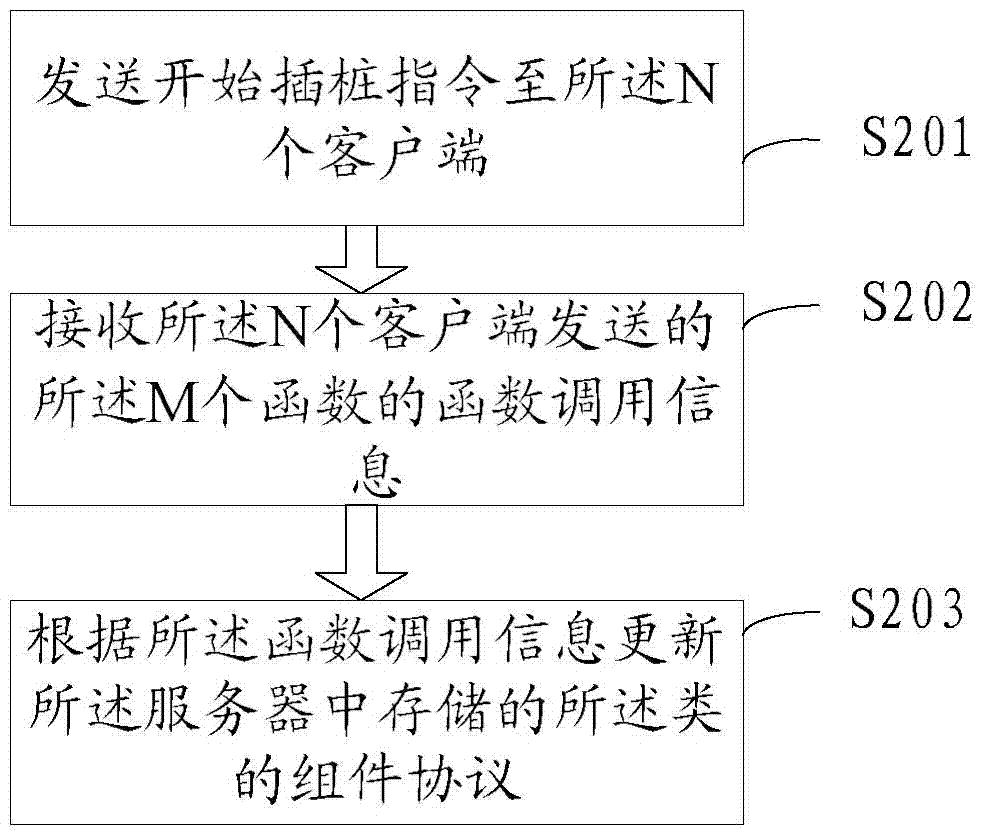
[0067] This embodiment provides a component protocol mining method, the method is applied in the server 102, the server 102 is connected to N clients 101, and N is an integer greater than 1, such as figure 2 As shown, the method includes:
[0068] Step S201, sending a stub start instruction to the N clients, where the stub start command carries function identifiers of M functions of the class to be mined, and M is an integer greater than 1;
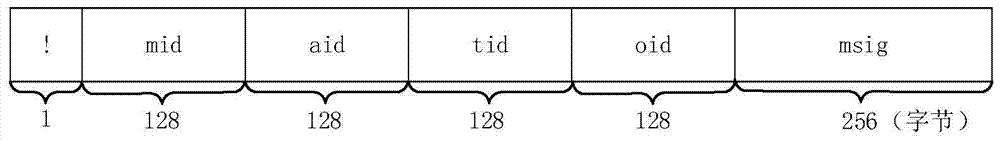
[0069] Step S202, receiving the function call information of the M functions sent by the N clients; the function call information is the information collected by the N clients based on the start instrumentation instruction;
[0070] Step S203, updating the component protocol of the class stored in the server according to the function call information.
[0071] In the embodiment of the present application, the function is an interface function, that is, a public function.
[0072] In the embodiment of the present application, the server...
Embodiment 2
[0120] In this embodiment, a component protocol mining method is provided, and the method is applied to a client 101, and the client 101 is connected to a server 102, such as Figure 6 As shown, the method includes:
[0121] Step S601, receiving the start instrumentation instruction sent by the server, the start instrumentation instruction carries the function identifiers of M functions of the class to be mined, and M is an integer greater than 1;
[0122] Step S602, determining L functions from the M functions; M≥L≥1;
[0123] Step S603, when the target application is running on the client, instrument the L functions of the target application to collect function call information of the L functions;
[0124] Step S604, sending the function call information to the server, so that the server updates the component protocol of the class stored in the server according to the function call information.
[0125] In the embodiment of the present application, the determination of L f...
Embodiment 3
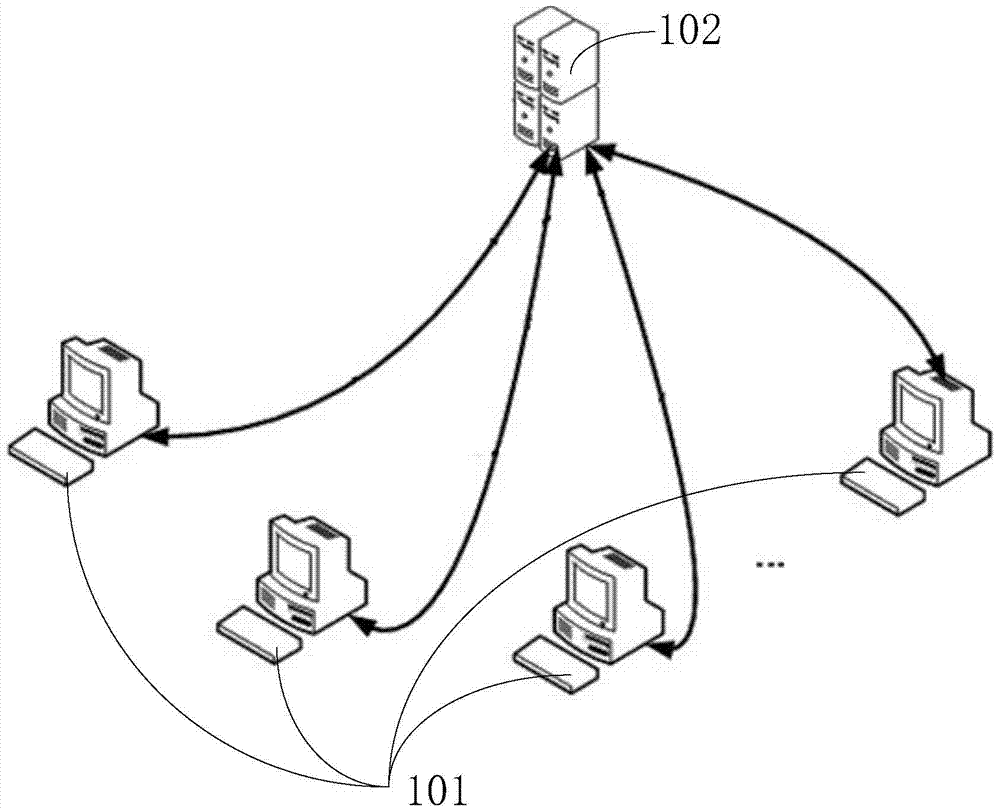
[0134] This embodiment provides a component protocol mining system, such as figure 1 As shown, the system includes a server 102 and N clients 101 connected to the server 102, where N is an integer greater than 1;
[0135] Wherein, the server 102 is configured to send a stub start instruction to the N clients, where the stub start command carries function identifiers of M functions of the class to be mined, and M is an integer greater than 1;
[0136] The N clients 101 are used to receive the start instrumentation instruction; and determine L functions from the M functions; M≥L≥1; and when running the target application program on the clients, Instrumenting the L functions of the target application to collect function call information of the L functions; and sending the function call information to the server 102;
[0137] The server 102 is further configured to receive the function call information sent by the N clients 101 ; and update the component protocol of the class sto...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com