Spam comment recognition method and system based on Bayesian algorithm and terminal
A technology of Bayesian algorithm and spam comments, which is applied in the identification method of spam comments based on Bayesian algorithm, system and terminal field, which can solve the problems that Bayesian algorithm cannot be directly identified, so as to improve user experience and reduce interference Effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
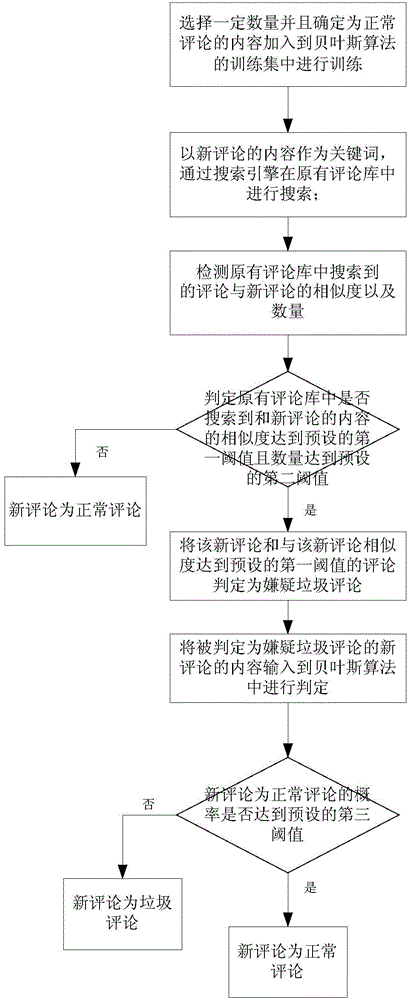
[0033] Such as figure 1 As shown, this embodiment discloses a method for identifying spam comments based on the Bayesian algorithm, and the steps are as follows:
[0034] Select a certain number of content that is determined to be normal comments and add them to the training set of the Bayesian algorithm for training; in this step, the number of normal comments selected to be input into the training set of the Bayesian algorithm for training is more than 100,000, generally 10 up to 500,000.
[0035] Use the content of the new comment as a keyword to search in the original comment database through the search engine;
[0036] Detect the similarity and quantity between the comments searched in the original comment database and the new comments. threshold, then the new comment and the comment whose similarity with the new comment reaches the preset first threshold is judged as a suspected spam comment, otherwise the new comment is judged as a normal comment; wherein the preset f...
Embodiment 2
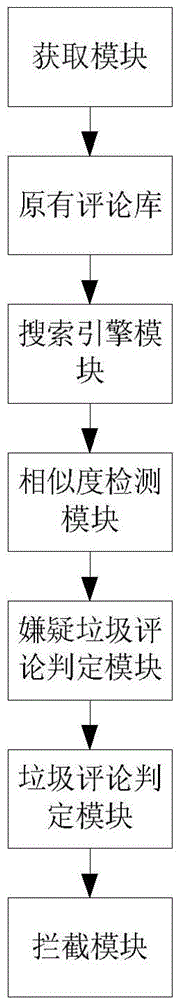
[0042] Such as figure 2 As shown, this embodiment also discloses a spam comment identification system based on the Bayesian algorithm for realizing the above identification method, which includes
[0043] The acquisition module is used to obtain a certain amount of content that is determined to be normal comments, and then input it into the training set of the Bayesian algorithm for training;
[0044] The original comment database, the database used for all comment content, is the original database of the system;
[0045] The search engine module is used to use the content of the new comment as a keyword to search for the content of the comment in the original comment database;
[0046] The similarity detection module is used to detect the similarity between the comments in the original comment database searched by the search engine module and the new comments;
[0047] A quantity detection module is used to detect the quantity of comments whose similarity with the new comm...
Embodiment 3
[0052] This embodiment also discloses a terminal including the above-mentioned spam comment identification system based on the Bayesian algorithm. The terminal can be a mobile phone, a tablet computer and a computer.
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com