Hybrid encryption method and device for realizing the same
A hybrid encryption and secret square technology, applied in the field of information security, can solve problems such as slow data processing speed, complex algorithm operation, and inability to distribute keys, and achieve the effects of easy modularization, high processing efficiency, and improved security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
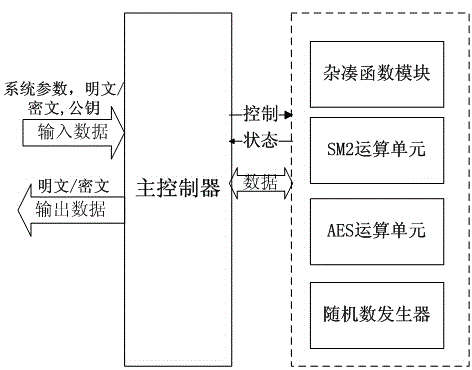
Image
Examples
Embodiment Construction
[0034] The technical scheme of the present invention is described in detail below in conjunction with accompanying drawing:
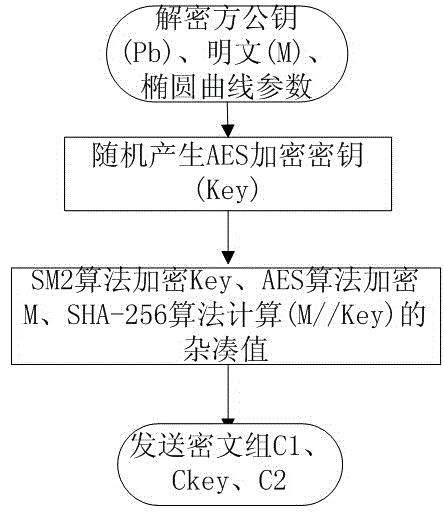
[0035] figure 1 The encryption flow of the hybrid encryption method of the present invention is shown. Such as figure 1 As shown, the encrypting party receives the plaintext M to be encrypted, the public key Pb of the decrypting party, and the elliptic curve system parameters used for SM2 encryption. Subsequently, an AES key Key is randomly generated. Then, use the AES key Key to encrypt the plaintext M with the AES algorithm, use the public key Pb of the decryption party to encrypt the AES key Key with the SM2 algorithm, and use the SHA-256 algorithm to calculate the hash of the AES key and the plaintext (M / / Key) value. Finally, the encryption party sends the ciphertext group: the ciphertext C1 obtained by AES encryption, the key block Ckey obtained by SM2 encryption, and the digest C2 calculated by the SHA-256 algorithm.
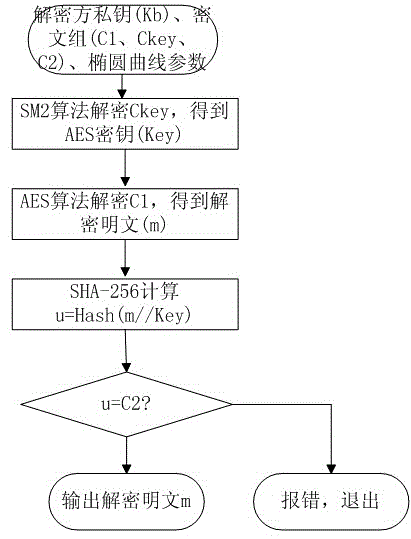
[0036] figure 2 The d...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com