Malicious website protection method based on OpenFlow protocol
An openflow protocol, malicious website technology, applied in transmission systems, electrical components, etc., can solve the problem of protection and protection schemes, not taking into account the active access to malicious websites, etc., to achieve the effect of preventing deception
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment
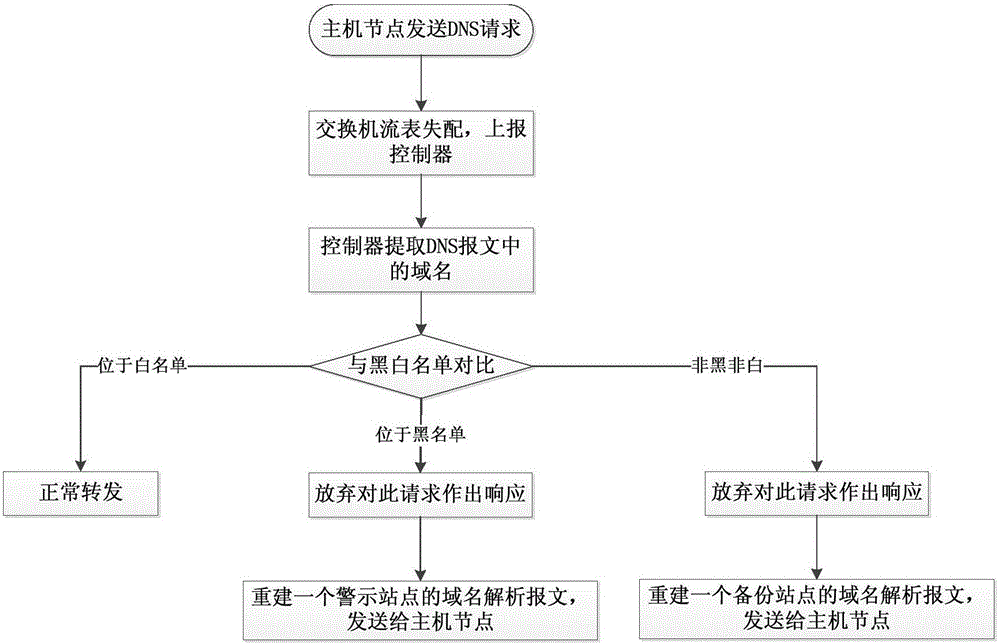
[0044] to combine figure 1 , the user accesses the www.1cbc.com.cn malicious website, in the malicious website protection method based on the OpenFlow protocol, the steps are as follows:
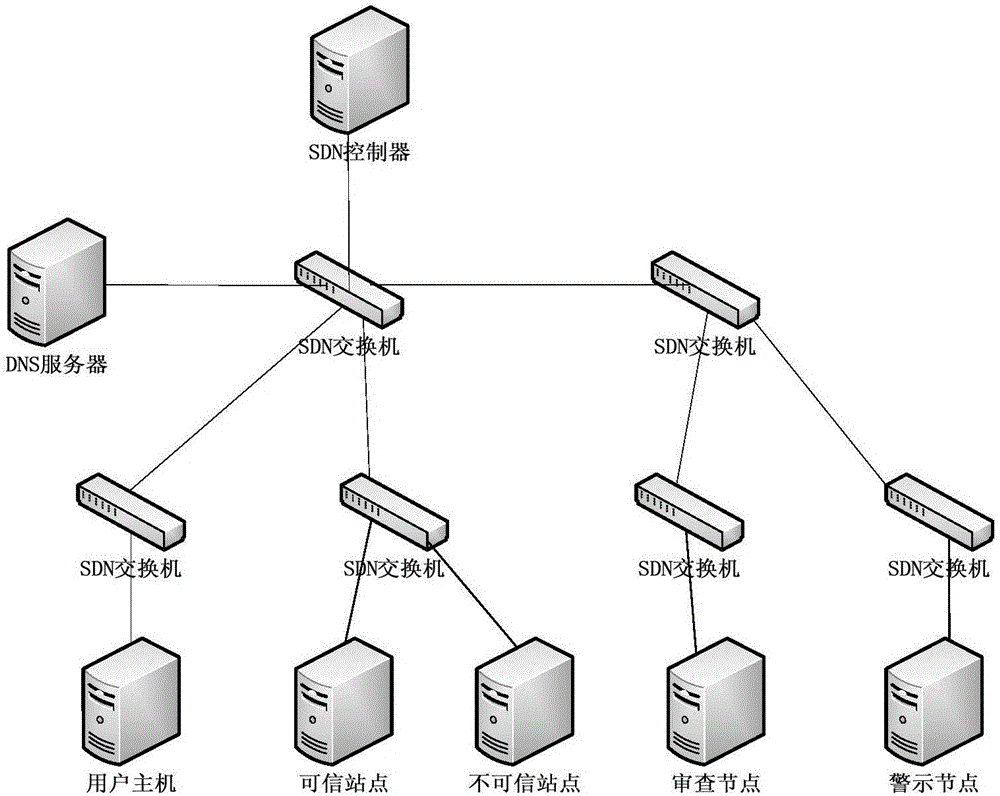
[0045] The first step is to monitor the OpenFlow packets in the network. Use the interface of the controller to obtain SDN network information, and monitor all OpenFlow messages reported to the controller node in the network. Process the received message, extract the port number in the message transport layer, analyze the message with port number 53, extract the domain name information of the application layer, and finally obtain the core domain name of "1cbc"; 53 packets are forwarded normally.
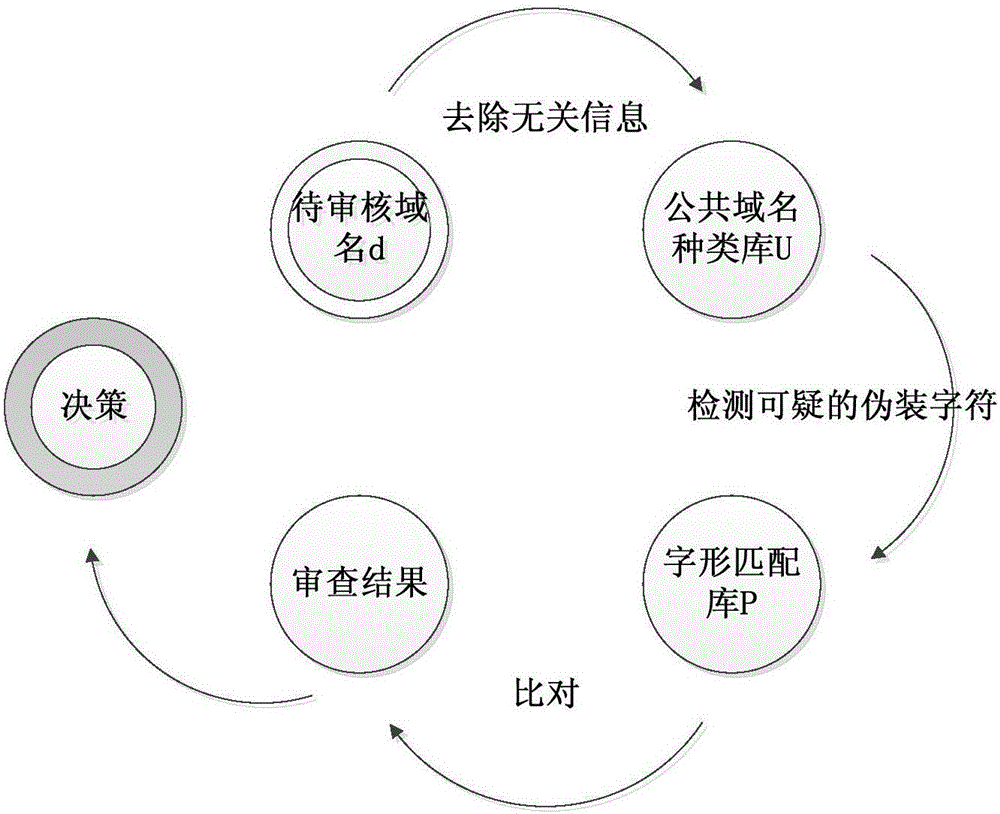
[0046] The second step is to match the domain name information with the black and white lists in the controller node, such as Figure 4 As shown, according to the matching result, it is judged whether the domain name is trustworthy. The specific steps are divided into three steps:
[0047] (1...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com