Method for tracking source code vulnerability correlation influence of Android system
A system source and loophole technology, applied in the direction of instruments, electrical digital data processing, platform integrity maintenance, etc., can solve problems such as incomplete update of system module functions, and achieve the effect of overcoming industrial utilization value, perfect system functions, and quick positioning.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0032] Below in conjunction with accompanying drawing and specific embodiment the present invention is described in further detail;
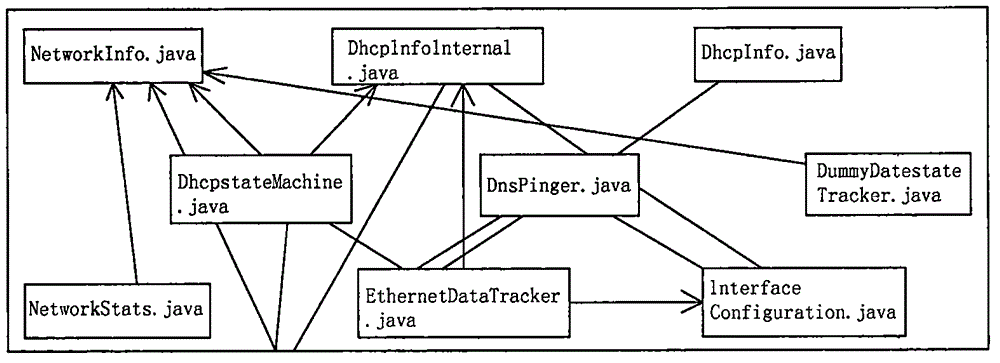
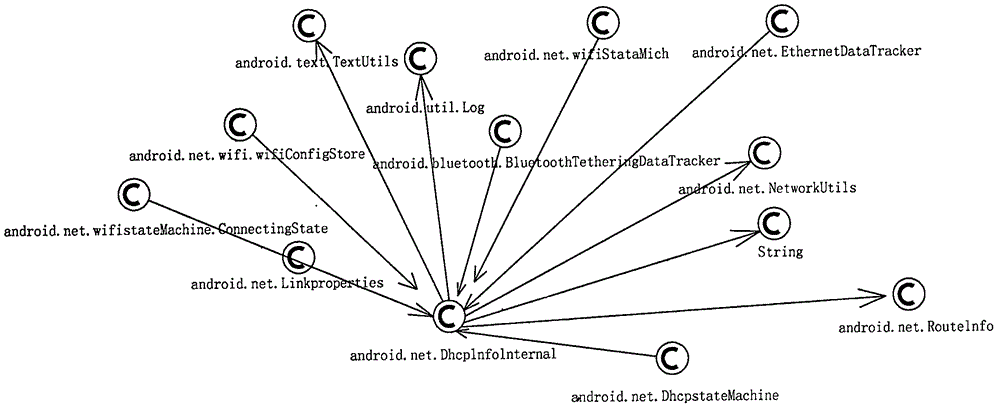
[0033] like figure 1 , 2 , 3, and 4, a method for tracking the impact of Android system source code vulnerabilities, including the following steps:
[0034] 1. Generate components
[0035] (1) Artificially analyze and divide the Android source code into multiple layers and modules. Most of the structure of the Android system will not change greatly during the upgrade process, and can be divided into multiple modules, such as Application and kernel layers, and then divided into layers Multiple modules, folders and files under the module can be used as components, and there are software elements such as classes or functions under the file component;
[0036] (2), scan the Android source code directory, use the folders and files under each module as components, generate multiple corresponding components, and define a set of component rules;
[...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com