Shell checking method based on dynamic behaviors of APK (android package) packing software
A software and behavioral technology, which is applied in the directions of instruments, electronic digital data processing, and platform integrity maintenance, etc., can solve the problems of low accuracy of shell checking results, low efficiency of shell checking, confusion of shell checking results, etc., and achieve the efficiency of shell checking Low, low accuracy, and increased difficulty effects
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0031] Below in conjunction with accompanying drawing, further describe the present invention through embodiment, but do not limit the scope of the present invention in any way.
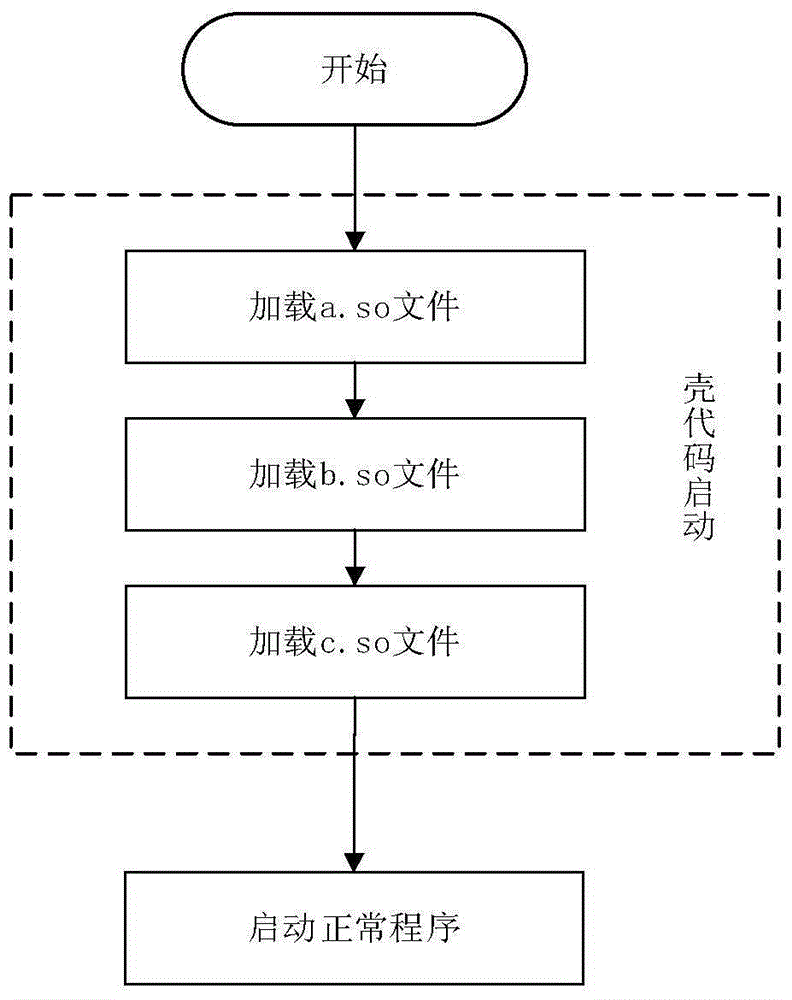
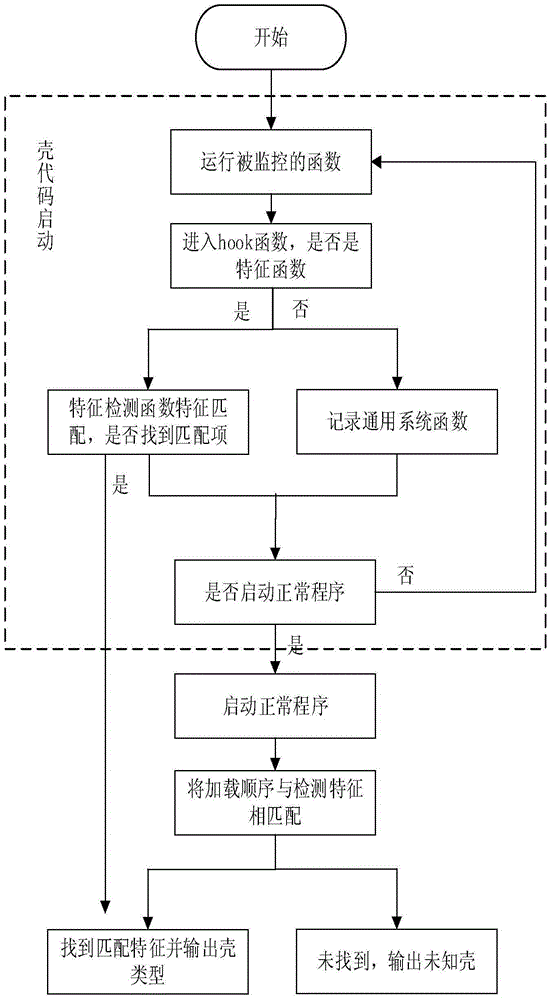
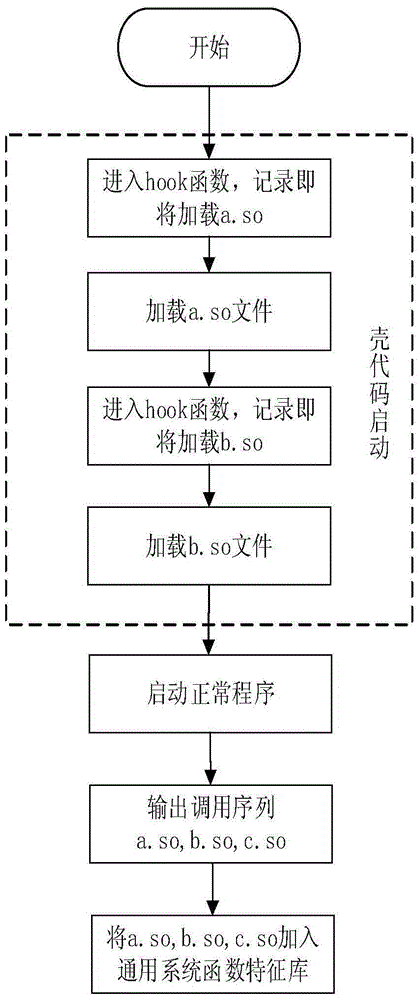
[0032] The present invention provides a shell checking method based on the dynamic behavior of APK shelling software. The Hook function monitors the call of the system function and feature function by the shell program, so that the packed program runs in the environment where the monitoring program is deployed. Once the monitored function is called, it jumps to the Hook function for recording. Thereby obtain the calling feature of packing software to system function and feature function, as detection feature; Then by feature comparison, obtain the type of the corresponding shell program of the program of packing; The present invention can effectively detect the type of mainstream APK shell , improve the accuracy and efficiency of analyzing packed malicious code.
[0033] figure 1 It is a flow chart...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com